Can Privacy, Security and Ease of Use Work Together?
Lohrman on Security
MAY 29, 2022
In this interview with Washington state Chief Privacy Officer Katy Ruckle, we explore the role of data privacy in providing government services.

Lohrman on Security
MAY 29, 2022
In this interview with Washington state Chief Privacy Officer Katy Ruckle, we explore the role of data privacy in providing government services.

DoublePulsar
MAY 29, 2022
Two days ago, Nao_sec identified an odd looking Word document in the wild, uploaded from an IP address in Belarus: Continue reading on DoublePulsar ».
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.
Security Affairs
MAY 29, 2022
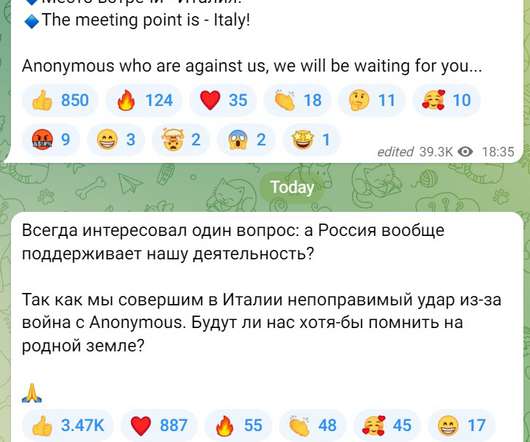
Pro-Russian hacker group KillNet is threatening again Italy, it announced a massive and unprecedented attack on May 30. Pro-Russian hacker group KillNet is threatening again Italy, it announced a massive and unprecedented attack on May 30. Pro-Russian ‘hacktivist’ group Killnet is one of the most active non-state actors operating since the beginning of the Russian invasion of Ukraine.

Bleeping Computer
MAY 29, 2022
Kaspersky's quarterly report on mobile malware distribution records a downward trend that started at the end of 2020, detecting one-third of the malicious installations reported in Q1 2021, and about 85% of those counted in Q4 2021. [.].

Speaker: Erroll Amacker
Automation is transforming finance but without strong financial oversight it can introduce more risk than reward. From missed discrepancies to strained vendor relationships, accounts payable automation needs a human touch to deliver lasting value. This session is your playbook to get automation right. We’ll explore how to balance speed with control, boost decision-making through human-machine collaboration, and unlock ROI with fewer errors, stronger fraud prevention, and smoother operations.

Security Affairs
MAY 29, 2022
A man from New York was sentenced to four years in prison for trading stolen credit card data and assisting the Infraud Organization. John Telusma (aka ‘Peterelliot’), a New York man from New York (37), was sentenced this week to four years in prison for purchasing stolen or compromised credit cards and assisting the Infraud Organization in monetizing their criminal activity fraudulent activity.
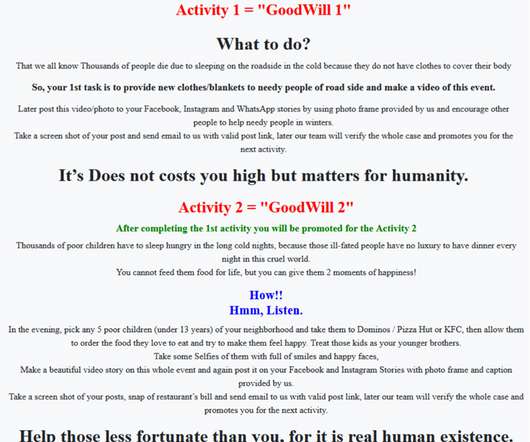
The Hacker News
MAY 29, 2022
Cybersecurity researchers have disclosed a new ransomware strain called GoodWill that compels victims into donating for social causes and provide financial assistance to people in need. "The ransomware group propagates very unusual demands in exchange for the decryption key," researchers from CloudSEK said in a report published last week.
Cyber Security Informer brings together the best content for cyber security professionals from the widest variety of industry thought leaders.

Bleeping Computer
MAY 29, 2022
John Telusma, a 37-year-old man from New York, was sentenced to four years in prison for selling and using stolen and compromised credit cards on the Infraud carding portal operated by the transnational cybercrime organization with the same name. [.].

CyberSecurity Insiders
MAY 29, 2022
Ed Williams, EMEA Director of SpiderLabs,? Trustwave. After years of a severe skills drought, the availability of security professionals appears to be gradually improving. The global shortfall in security professionals dropped from 3.12 million to 2.72 million last year. However, although this is notable progress, it is not taking place fast enough.
Bleeping Computer
MAY 29, 2022
EnemyBot, a botnet based on code from multiple malware pieces, is expanding its reach by quickly adding exploits for recently disclosed critical vulnerabilities in web servers, content management systems, IoT, and Android devices. [.].

CyberSecurity Insiders
MAY 29, 2022
Dr. Melanie Garson, an international security specialist working for the University College of London, expressed her deep concerns about national security while interacting with a news web resource. She said that hospital infrastructure was on the verge of being cyber-attacked by Russian sleeper cells, whose aim is to disrupt the healthcare infrastructure and to create panic among patients and their near & dear.

Advertisement
Many cybersecurity awareness platforms offer massive content libraries, yet they fail to enhance employees’ cyber resilience. Without structured, engaging, and personalized training, employees struggle to retain and apply key cybersecurity principles. Phished.io explains why organizations should focus on interactive, scenario-based learning rather than overwhelming employees with excessive content.

Security Boulevard
MAY 29, 2022
As I mentioned in a previous blog post, 4G is really pretty good. It makes quite a few useful things possible: fast general Internet access (on the order of DSL) download and even upload of high-resolution video always-on behavior (with batteries lasting the entire day) apps relying on location and identity (technically a smartphone feature). The post Do we really need 5G?

CyberSecurity Insiders
MAY 29, 2022
By Lokke Moerel, Senior Of Counsel, Morrison & Foerster (Brussels). Europe is one of the most digitalized societies in the world, and this has only been accelerated by the COVID?19 pandemic. Within no time, people started working from home and children were being schooled online. According to a 2020 report by McKinsey , the pandemic accelerated digital adoption by seven years.

The Hacker News
MAY 29, 2022
Network credentials and virtual private network (VPN) access for colleges and universities based in the U.S. are being advertised for sale on underground and public criminal marketplaces. "This exposure of sensitive credential and network access information, especially privileged user accounts, could lead to subsequent cyber attacks against individual users or affiliated organizations," the U.S.

CyberSecurity Insiders
MAY 29, 2022
A research group from ESET has discovered that cyber-crooks are paying a monthly fee of $5000 to gain fraudulent access to 467 android apps to steal banking-related details. Information is out that the campaign has been running for quite some time and is aiming to siphon cryptocurrencies along with fiat. Dubbed an ERMAC banking Trojan, the malware is seen impersonating android users in Poland and has now spread slowly to New Zealand.

Advertisement
The DHS compliance audit clock is ticking on Zero Trust. Government agencies can no longer ignore or delay their Zero Trust initiatives. During this virtual panel discussion—featuring Kelly Fuller Gordon, Founder and CEO of RisX, Chris Wild, Zero Trust subject matter expert at Zermount, Inc., and Principal of Cybersecurity Practice at Eliassen Group, Trey Gannon—you’ll gain a detailed understanding of the Federal Zero Trust mandate, its requirements, milestones, and deadlines.

Acunetix
MAY 29, 2022
Businesses often perceive vulnerability scanning as an alternative to penetration testing. This perception is wrong. An organization conscious of cybersecurity must include both these activities in their business processes and make sure that they work in unison. Missing out on one of them greatly decreases. Read more. The post Penetration testing vs vulnerability scanning appeared first on Acunetix.

Security Boulevard
MAY 29, 2022
Ransomware /?rans(?)mw??/ a type of malicious software aimed to hinder access to a computer system until a sum of money is paid. In a ransomware attack, victims receive an unsuspicious email attached with a malware. Upon opening the email(which might […]. The post Increasing Threat Of Ransomware to Online Business appeared first on WeSecureApp :: Simplifying Enterprise Security!

The State of Security
MAY 29, 2022
Do you recall one of the first really fun chemistry experiment you performed as a child? If your school followed the usual curriculum, then you probably made a model volcano and then added some baking soda to the opening, followed by the addition of vinegar. A variation of this experiment was to add the ingredients […]… Read More. The post Protecting Against Bad Chemistry (with Cybersecurity) appeared first on The State of Security.

Security Boulevard
MAY 29, 2022
Tanya Janca, founder of the We Hack Purple Academy, Director of Developer Relations and Community at Bright, and author of “Alice & Bob Learn Application Security” joins us to discuss the current state and future of Application Security. In this episode we discuss what Tanya’s been up to, what’s changed in AppSec over the last […]. The post The State of Application Security with Tanya Janca appeared first on The Shared Security Show.

Speaker: Sierre Lindgren
Fraud is a battle that every organization must face – it’s no longer a question of “if” but “when.” Every organization is a potential target for fraud, and the finance department is often the bullseye. From cleverly disguised emails to fraudulent payment requests, the tactics of cybercriminals are advancing rapidly. Drawing insights from real-world cases and industry expertise, we’ll explore the vulnerabilities in your processes and how to fortify them effectively.

The State of Security
MAY 29, 2022
Tripwire’s May 2022 Patch Priority Index (PPI) brings together important vulnerabilities for Microsoft. First on the patch priority list this month are 2 remote code execution vulnerabilities for Excel and a security feature bypass vulnerability for Office. Up next are patches that affect components of the Windows operating systems. These patches resolve over 40 vulnerabilities, […]… Read More.

Security Boulevard
MAY 29, 2022
Our thanks to Zero Day Initiative for publishing their outstanding Pwn2Own Vancouver 2022 videos on the organization’s’ YouTube channel. Permalink. The post Zero Day Initiative’s Pwn2Own Vancouver 2022 – Billy Jheng Bing-Jhong’s, Muhammad Alifa Ramdhan’s And Nguy?n Hoàng Th?ch’s ‘STARLabs Vs. Oracle VirtualBox’ appeared first on Security Boulevard.

Security Boulevard
MAY 29, 2022
Our thanks to Zero Day Initiative for publishing their outstanding Pwn2Own Vancouver 2022 videos on the organization’s’ YouTube channel. Permalink. The post Zero Day Initiative’s Pwn2Own Vancouver 2022 – ‘Masato Kinugawa Vs. Microsoft Teams’ appeared first on Security Boulevard.

Security Boulevard
MAY 29, 2022
In this interview with Washington state Chief Privacy Officer Katy Ruckle, we explore the role of data privacy in providing government services. . The post Can Privacy, Security and Ease of Use Work Together? appeared first on Security Boulevard.

Advertisement
Keeper Security is transforming cybersecurity for people and organizations around the world. Keeper’s affordable and easy-to-use solutions are built on a foundation of zero-trust and zero-knowledge security to protect every user on every device. Our next-generation privileged access management solution deploys in minutes and seamlessly integrates with any tech stack to prevent breaches, reduce help desk costs and ensure compliance.

Security Boulevard
MAY 29, 2022
via the comic artistry and dry wit of Randall Munroe , resident at XKCD ! Permalink. The post XKCD ‘Field Topology’ appeared first on Security Boulevard.

Security Boulevard
MAY 29, 2022
Tripwire’s May 2022 Patch Priority Index (PPI) brings together important vulnerabilities for Microsoft. First on the patch priority list this month are 2 remote code execution vulnerabilities for Excel and a security feature bypass vulnerability for Office. Up next are patches that affect components of the Windows operating systems. These patches resolve over 40 vulnerabilities, […]… Read More.

Security Boulevard
MAY 29, 2022
Do you recall one of the first really fun chemistry experiment you performed as a child? If your school followed the usual curriculum, then you probably made a model volcano and then added some baking soda to the opening, followed by the addition of vinegar. A variation of this experiment was to add the ingredients […]… Read More. The post Protecting Against Bad Chemistry (with Cybersecurity) appeared first on The State of Security.
Let's personalize your content