Attack on Security Titans: Earth Longzhi Returns With New Tricks
Trend Micro
MAY 1, 2023
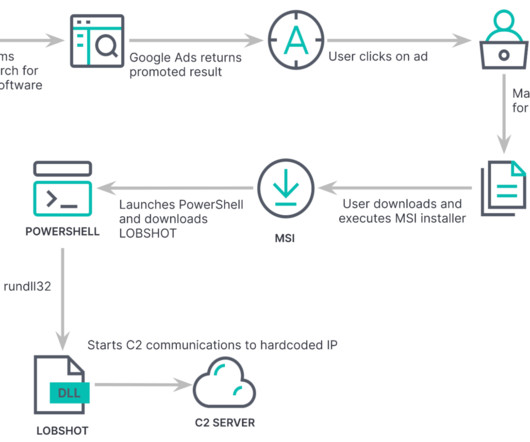
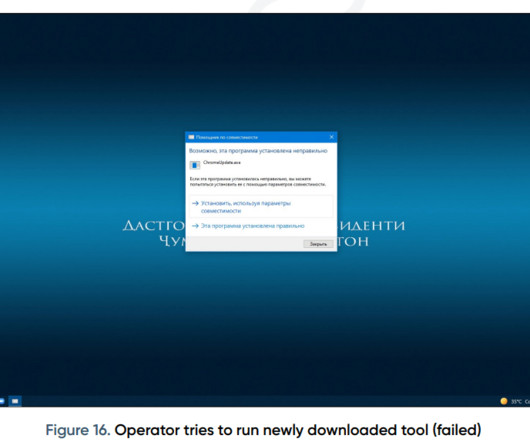
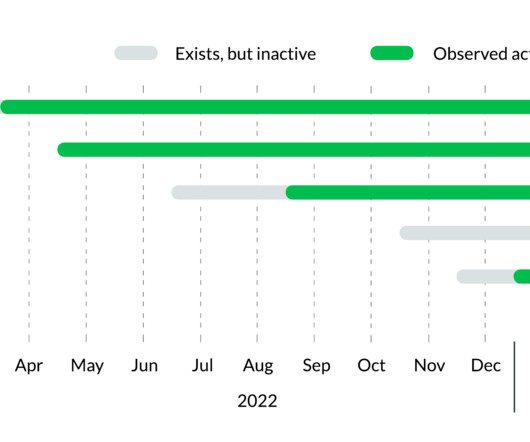
After months of dormancy, Earth Longzhi, a subgroup of advanced persistent threat (APT) group APT41, has reemerged using new techniques in its infection routine. This blog entry forewarns readers of Earth Longzhi’s resilience as a noteworthy threat.

































Let's personalize your content