Widow-Maker: A CIO Story
Lohrman on Security
APRIL 23, 2023
When Bill Vajda, the Wyoming CIO in 2022, suddenly left his role in January of this year, few knew the real reason why. Here's the rest of the story.

Lohrman on Security
APRIL 23, 2023
When Bill Vajda, the Wyoming CIO in 2022, suddenly left his role in January of this year, few knew the real reason why. Here's the rest of the story.

Tech Republic Security
APRIL 23, 2023
PURPOSE Every enterprise needs to establish a plan of action to assess and then recover from unauthorized access to its network. This policy from TechRepublic Premium provides a foundation from which to start building your specific procedures. From the policy: ASSIGN AN INCIDENT RESPONSE TEAM An incident response team should be put together and a. The post Incident response policy appeared first on TechRepublic.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

CyberSecurity Insiders
APRIL 23, 2023
In recent years, the term “offensive cyber capabilities” has become increasingly common in discussions around national security and military strategies. Offensive cyber capabilities refer to the ability of a nation or organization to launch cyber attacks on other countries, groups, or individuals. Offensive cyber capabilities are a powerful tool in modern warfare, as they can be used to disrupt enemy operations, steal sensitive information, and even cause physical damage to infrastru
Bleeping Computer
APRIL 23, 2023
A new enterprise-targeting malware toolkit called 'Decoy Dog' has been discovered after inspecting anomalous DNS traffic that is distinctive from regular internet activity. [.

Advertisement
How many people would you trust with your house keys? Chances are, you have a handful of trusted friends and family members who have an emergency copy, but you definitely wouldn’t hand those out too freely. You have stuff that’s worth protecting—and the more people that have access to your belongings, the higher the odds that something will go missing.

CyberSecurity Insiders
APRIL 23, 2023
Lung cancer is a dangerous and contagious disease that spreads throughout the body quickly and is not easy to detect in its early stages. However, thanks to the technology of artificial intelligence-enabled machine learning tools, detecting lung cancer is now possible almost 10 years before its onset. Dubbed as ‘CanPredict’, the AI program helps high-risk patients receive appropriate treatment before the disease becomes deadly.
Bleeping Computer
APRIL 23, 2023
Enterprise-level network equipment on the secondary market hide sensitive data that hackers could use to breach corporate environments or to obtain customer information. [.
Cyber Security Informer brings together the best content for cyber security professionals from the widest variety of industry thought leaders.

The Hacker News
APRIL 23, 2023
A new "all-in-one" stealer malware named EvilExtractor (also spelled Evil Extractor) is being marketed for sale for other threat actors to steal data and files from Windows systems. "It includes several modules that all work via an FTP service," Fortinet FortiGuard Labs researcher Cara Lin said. "It also contains environment checking and Anti-VM functions.

Security Affairs
APRIL 23, 2023
Non-profit health insurer Point32Health suffered a ransomware attack and has taken systems offline in response to the incident. Non-profit health insurer Point32Health has taken systems offline in response to a ransomware attack that took place on April 17. The insurer immediately launched an investigation into the incident with the help of third-party cybersecurity experts to determine the ext The organization notified law enforcement and regulators, and it is currently working to recover the o
The Hacker News
APRIL 23, 2023
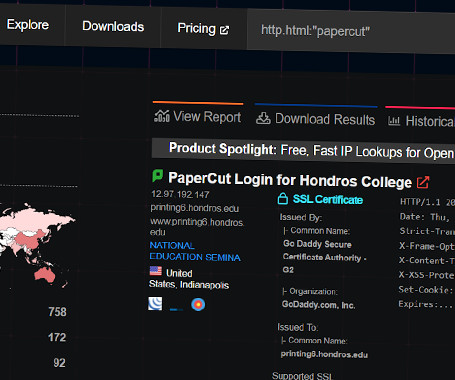
Print management software provider PaperCut said that it has "evidence to suggest that unpatched servers are being exploited in the wild," citing two vulnerability reports from cybersecurity company Trend Micro.

Malwarebytes
APRIL 23, 2023
Malwarebytes’ researchers have found a malvertising scheme that leads to clickjacking. Clickjacking is a form of ad fraud which is also referred to as click fraud or click spam. It is a practice performed by certain dubious advertising networks, where they sometimes use automated programs—from simple to sophisticated bots and botnets—to interact with advertisements online.

Advertiser: Revenera
In a recent study, IDC found that 64% of organizations said they were already using open source in software development with a further 25% planning to in the next year. Most organizations are unaware of just how much open-source code is used and underestimate their dependency on it. As enterprises grow the use of open-source software, they face a new challenge: understanding the scope of open-source software that's being used throughout the organization and the corresponding exposure.

Security Affairs
APRIL 23, 2023
A new round of the weekly SecurityAffairs newsletter arrived! Every week the best security articles from Security Affairs are free for you in your email box. Enjoy a new round of the weekly SecurityAffairs newsletter, including the international press. Abandoned Eval PHP WordPress plugin abused to backdoor websites CISA adds MinIO, PaperCut, and Chrome bugs to its Known Exploited Vulnerabilities catalog At least 2 critical infrastructure orgs breached by North Korea-linked hackers behind 3CX att

Malwarebytes
APRIL 23, 2023
Last week on Malwarebytes Labs: Fake Chrome updates spread malware Woman tracks down and turns table on Airbnb scammer Update Chrome now! Google patches actively exploited flaw Beware: Fake IRS tax email wants your Microsoft account Ransomware in Germany, April 2022 – March 2023 Living Off the Land (LOTL) attacks: Detecting ransomware gangs hiding in plain sight Payment giant's point-of-sale outage caused by ALPHV ransomware Spring cleaning tips for your browser Avoid this "lost injured do

WIRED Threat Level
APRIL 23, 2023
Pumpkin Sandstorm. Spandex Tempest. Charming Kitten. Is this really how we want to name the hackers wreaking havoc worldwide?

SecureBlitz
APRIL 23, 2023
Learn how to protect your online identity in this post. The Internet is a powerful tool for businesses and individuals alike. But it can also be dangerous for people who don’t know how to keep their personal data safe. Identity theft is an escalating concern that causes billions of dollars in yearly losses. As scammers […] The post How To Protect Your Online Identity In 2023 appeared first on SecureBlitz Cybersecurity.

Advertisement
Within the past few years, ransomware attacks have turned to critical infrastructure, healthcare, and government entities. Attackers have taken advantage of the rapid shift to remote work and new technologies. Add to that hacktivism due to global conflicts and U.S. elections, and an increased focus on AI, and you have the perfect recipe for a knotty and turbulent 2024.

Security Boulevard
APRIL 23, 2023
Our thanks to USENIX for publishing their Presenter’s outstanding USENIX Security ’22 Conference content on the organization’s’ YouTube channel. Permalink The post USENIX Security ’22 – David Koisser, Patrick Jauernig, Gene Tsudik, Ahmad-Reza Sadeghi – ‘V’CER: Efficient Certificate Validation In Constrained Networks ‘ appeared first on Security Boulevard.

Troy Hunt
APRIL 23, 2023
I feel like a significant portion of this week's video went to discussing "the Coinbase breach that wasn't a Coinbase breach" There are various services out there that are used by the likes of password managers to alert their customers to new breaches (including HIBP in 1Password) and whoever Dashlane is using frankly, royally cocked up the attribution.
Security Boulevard
APRIL 23, 2023
When Bill Vajda, the Wyoming CIO in 2022, suddenly left his role in January of this year, few knew the real reason why. Here's the rest of the story. The post Widow-Maker: A CIO Story appeared first on Security Boulevard.

Malwarebytes
APRIL 23, 2023
Thanks to Malwarebytes' Stefan Dasic who provided the research and screenshots for this article. Flipper Zero, a " multi-tool device for hackers ", is frequently out of stock due to its popularity in hardware circles. Flipper Zero combines research and penetration hardware tools into a single unit. It can be used straight out of the box, but it's also open-source and customizable, so users can extend its functionality however they like.

Advertisement
The healthcare industry has massively adopted web tracking tools, including pixels and trackers. Tracking tools on user-authenticated and unauthenticated web pages can access personal health information (PHI) such as IP addresses, medical record numbers, home and email addresses, appointment dates, or other info provided by users on pages and thus can violate HIPAA Rules that govern the Use of Online Tracking Technologies by HIPAA Covered Entities and Business Associates.

Security Boulevard
APRIL 23, 2023
There have been quite a few regulatory developments recently surrounding cybersecurity and its bedfellow, tech, or IT/ICT (Information and Communications Technology) risk. So, I thought I’d take a few lines to explore some of the salient points and what they might mean for cyber risk professionals in the coming weeks and months. There’s quite a … Read More The post What the SEC and Other Regulators Are Saying About Where to Start Your CRQ Journey appeared first on Security Boulevard.
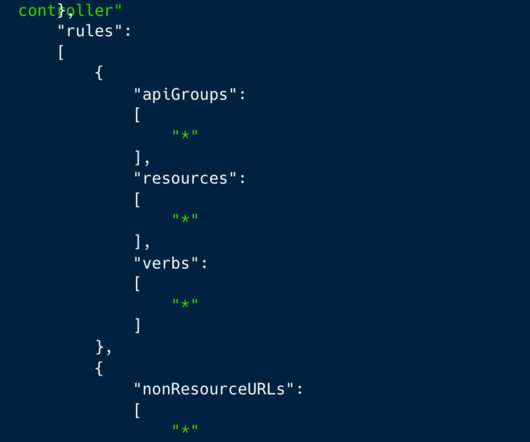
Security Affairs
APRIL 23, 2023
Experts warn of a large-scale cryptocurrency mining campaign exploiting Kubernetes (K8s) Role-Based Access Control ( RBAC ). Cloud security firm Aqua discovered a large-scale cryptocurrency mining campaign exploiting Kubernetes (K8s) Role-Based Access Control ( RBAC ) to create backdoors and run miners. The campaign was tracked as RBAC Buster, the experts reported that the attacks are actively targeting at least 60 clusters in the wild. “We have recently discovered the first-ever evidence
Let's personalize your content