Are We Seeing Fewer Ransomware Attacks? Not Now
Lohrman on Security
MAY 28, 2023
Despite what you may have heard, ransomware threats continue to grow and evolve in mid-2023. Here’s what you need to know.

Lohrman on Security
MAY 28, 2023
Despite what you may have heard, ransomware threats continue to grow and evolve in mid-2023. Here’s what you need to know.

Bleeping Computer
MAY 28, 2023
A new 'File Archivers in the Browser' phishing kit abuses ZIP domains by displaying fake WinRAR or Windows File Explorer windows in the browser to convince users to launch malicious files. [.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

CyberSecurity Insiders
MAY 28, 2023
Artificial Intelligence (AI) has emerged as a game-changer, revolutionizing industries and transforming the way we live and work. However, as AI continues to advance, it brings with it a new set of cybersecurity risks and challenges. In this blog, we will delve into the potential risks associated with AI and the importance of implementing robust cybersecurity measures to safeguard against these threats.

Bleeping Computer
MAY 28, 2023
The Python Package Index (PyPI) has announced that it will require every account that manages a project on the platform to have two-factor authentication (2FA) turned on by the end of the year. [.

Advertisement
How many people would you trust with your house keys? Chances are, you have a handful of trusted friends and family members who have an emergency copy, but you definitely wouldn’t hand those out too freely. You have stuff that’s worth protecting—and the more people that have access to your belongings, the higher the odds that something will go missing.

CyberSecurity Insiders
MAY 28, 2023
In today’s digital landscape, cybersecurity has become a critical concern for individuals and organizations alike. Aspiring cybersecurity researchers often wonder where to start and what areas to explore. This article aims to provide a comprehensive list of cybersecurity research topics suitable for beginners, helping them delve into the fundamentals of this rapidly evolving field.
Security Affairs
MAY 28, 2023
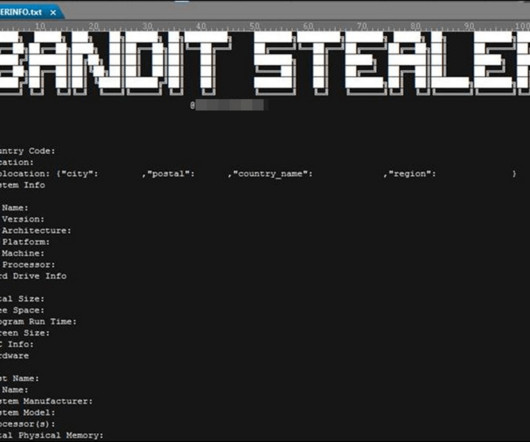
Bandit Stealer is a new stealthy information stealer malware that targets numerous web browsers and cryptocurrency wallets. Trend Micro researchers discovered a new info-stealing malware, dubbed Bandit Stealer, which is written in the Go language and targets multiple browsers and cryptocurrency wallets. At this time, the malware only targets Windows systems, but experts pointed out that it has the potential to expand to other platforms because it is written in Go.
Cyber Security Informer brings together the best content for cyber security professionals from the widest variety of industry thought leaders.

Security Boulevard
MAY 28, 2023
Operational Technology (OT) security controls include the measures, workflows and procedures put in place to protect various OT systems from cyber threats. OT systems are used to control, run and monitor critical infrastructure, such as those in power plants, water treatment facilities, and transportation systems. As these systems become increasingly interconnected, they turn more vulnerable […] The post Essential security practices in OT control systems appeared first on Security Boulevard.

Security Affairs
MAY 28, 2023
Swiss electrification and automation technology giant ABB confirmed it has suffered a data breach after a ransomware attack. ABB has more than 105,000 employees and has $29.4 billion in revenue for 2022. On May 7, 2023, the Swiss multinational company, leading electrification and automation technology provider, suffered a cyber attack that reportedly impacted its business operations.

The Hacker News
MAY 28, 2023
The Python Package Index (PyPI) announced last week that every account that maintains a project on the official third-party software repository will be required to turn on two-factor authentication (2FA) by the end of the year. "Between now and the end of the year, PyPI will begin gating access to certain site functionality based on 2FA usage," PyPI administrator Donald Stufft said.

Security Boulevard
MAY 28, 2023
Despite what you may have heard, ransomware threats continue to grow and evolve in mid-2023. Here’s what you need to know. The post Are We Seeing Fewer Ransomware Attacks? Not Now appeared first on Security Boulevard.

Advertiser: Revenera
In a recent study, IDC found that 64% of organizations said they were already using open source in software development with a further 25% planning to in the next year. Most organizations are unaware of just how much open-source code is used and underestimate their dependency on it. As enterprises grow the use of open-source software, they face a new challenge: understanding the scope of open-source software that's being used throughout the organization and the corresponding exposure.

Quick Heal Antivirus
MAY 28, 2023
With groundbreaking innovations and intelligent machines revolutionizing industries, the advent of AI is sparking endless possibilities If you’re. The post Antivirus Security and the Role of Artificial Intelligence (AI) appeared first on Quick Heal Blog.

Security Boulevard
MAY 28, 2023
Our thanks to BSidesSF for publishing their presenter’s superlative BSidesSF 2023 content on the organizations’ YouTube channel. Permalink The post BSidesSF 2023 – Sohini Mukherjee, Tim Lam – Defining a Data Masking Framework at Scale appeared first on Security Boulevard.

Appknox
MAY 28, 2023
Launching a mobile app in Bahrain, whether for iOS or Android, requires careful consideration of security measures.

Security Boulevard
MAY 28, 2023
We offer a guide to become an ethical hacker based off some information on common non-technical and technical skills hackers find useful for their role. The post How to Become an Ethical Hacker appeared first on Security Boulevard.

Advertisement
Within the past few years, ransomware attacks have turned to critical infrastructure, healthcare, and government entities. Attackers have taken advantage of the rapid shift to remote work and new technologies. Add to that hacktivism due to global conflicts and U.S. elections, and an increased focus on AI, and you have the perfect recipe for a knotty and turbulent 2024.
Hacker's King
MAY 28, 2023
The internet is a vast landscape, and within its depths lie hidden gems that offer unique tools and services. These underground websites are often known for their secretive nature and provide unconventional solutions to everyday problems. In this article, we will shine a light on some underground websites that offer fascinating features and functionalities.

Security Boulevard
MAY 28, 2023
In this episode, we discuss Meta’s record-breaking $1.3 billion fine by the EU for unlawfully transferring user data, shedding light on the increasing risks faced by tech companies in violating privacy rules. Highly realistic images of a Pentagon explosion went viral on Twitter, causing a stock market dip. We discuss the risks associated with Twitter’s […] The post Meta’s $1.3 Billion Fine, AI Hoax Hysteria, Montana’s TikTok Ban appeared first on Shared Security Podcast.
Malwarebytes
MAY 28, 2023
Last week on Malwarebytes Labs: Update now: 9 vulnerabilities impact Cisco Small Business Series ChatGPT: Cybersecurity friend or foe? Webinar recap: EDR vs MDR for business success Identity crisis: How an anti-porn crusade could jam the Internet, featuring Alec Muffett: Lock and Code S04E11 Malvertising via brand impersonation is back again Update now!

Security Boulevard
MAY 28, 2023
SINGAPORE – 29 May 2022 – LogRhythm, a leading cybersecurity company, has been recognised with the SIEM – Computer Software accolade at the 2023 SBR Technology Excellence Awards. This marks the 5th consecutive year the company has been given this… The post LogRhythm Receives Best SIEM – Computer Software at the SBR Technology Excellence Awards 2023 for its Ability to Eliminate Noise Effectively appeared first on LogRhythm.

Advertisement
The healthcare industry has massively adopted web tracking tools, including pixels and trackers. Tracking tools on user-authenticated and unauthenticated web pages can access personal health information (PHI) such as IP addresses, medical record numbers, home and email addresses, appointment dates, or other info provided by users on pages and thus can violate HIPAA Rules that govern the Use of Online Tracking Technologies by HIPAA Covered Entities and Business Associates.
Let's personalize your content