New Variant of DLL Search Order Hijacking Bypasses Windows 10 and 11 Protections
The Hacker News
JANUARY 1, 2024
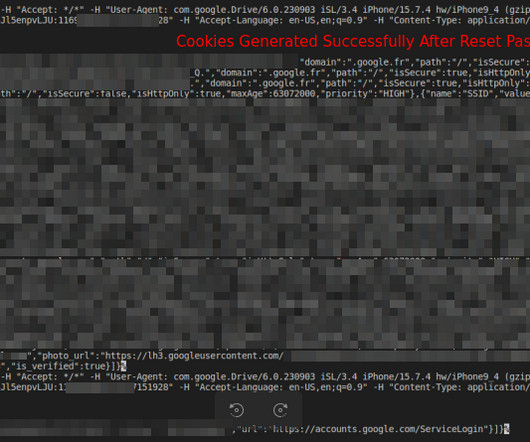
Security researchers have detailed a new variant of a dynamic link library (DLL) search order hijacking technique that could be used by threat actors to bypass security mechanisms and achieve execution of malicious code on systems running Microsoft Windows 10 and Windows 11.


































Let's personalize your content