2023’s Dark Horse Cyber Story: Critical Infrastructure Attacks
Lohrman on Security
DECEMBER 3, 2023
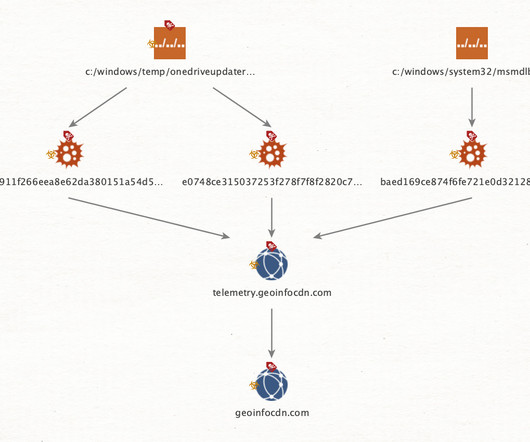
There are several cybersecurity trends that truly deserve top attention when we look back at 2023 — and they will get it. Meanwhile, cyber attacks against critical infrastructure quietly grow, despite a lack of major attention.





































Let's personalize your content