Breaking Laptop Fingerprint Sensors
Schneier on Security
NOVEMBER 29, 2023
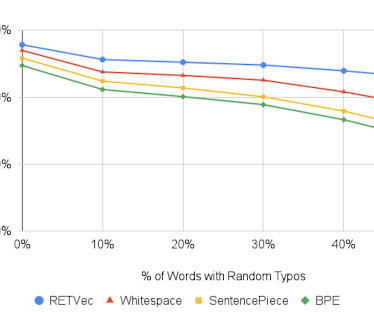
They’re not that good : Security researchers Jesse D’Aguanno and Timo Teräs write that, with varying degrees of reverse-engineering and using some external hardware, they were able to fool the Goodix fingerprint sensor in a Dell Inspiron 15, the Synaptic sensor in a Lenovo ThinkPad T14, and the ELAN sensor in one of Microsoft’s own Surface Pro Type Covers.






































Let's personalize your content