How to Think Like a Hacker — and Defend Your Data
Lohrman on Security
MARCH 17, 2024
In this interview with white hat hacker Mishaal Khan, we learn about open source intelligence gathering and how to hack humans — or not.

Lohrman on Security
MARCH 17, 2024
In this interview with white hat hacker Mishaal Khan, we learn about open source intelligence gathering and how to hack humans — or not.

Penetration Testing
MARCH 17, 2024
Fujitsu, the Japanese multinational technology giant, has revealed a data breach resulting from a malware infection within its corporate network. The company disclosed that sensitive files containing both personal and customer information were exposed... The post Fujitsu Discloses Data Breach, Customer and Personal Information Compromised appeared first on Penetration Testing.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

Bleeping Computer
MARCH 17, 2024
AT&T says a massive trove of data impacting 71 million people did not originate from its systems after a hacker leaked it on a cybercrime forum and claimed it was stolen in a 2021 breach of the company. [.
Penetration Testing
MARCH 17, 2024
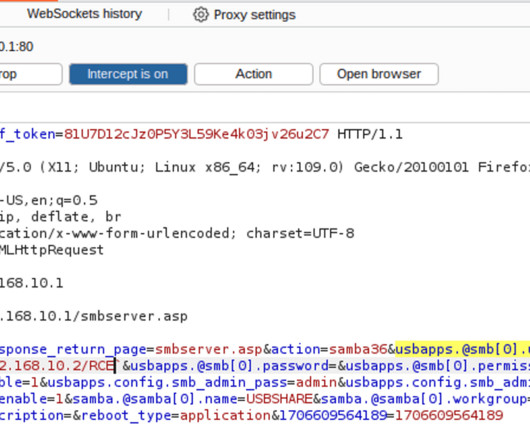
Security researchers have uncovered two serious “command injection” vulnerabilities in the widely used TRENDnet AC2600 MU-MIMO WiFi Router (model TEW-827DRU). These vulnerabilities, labeled CVE-2024-28353 and CVE-2024-28354, leave these routers alarmingly exposed to potential remote... The post CVE-2024-28353 & 28354: TRENDnet Router Takeover Flaws Exposed, No Patch Available appeared first on Penetration Testing.

Advertisement
How many people would you trust with your house keys? Chances are, you have a handful of trusted friends and family members who have an emergency copy, but you definitely wouldn’t hand those out too freely. You have stuff that’s worth protecting—and the more people that have access to your belongings, the higher the odds that something will go missing.
Security Affairs
MARCH 17, 2024
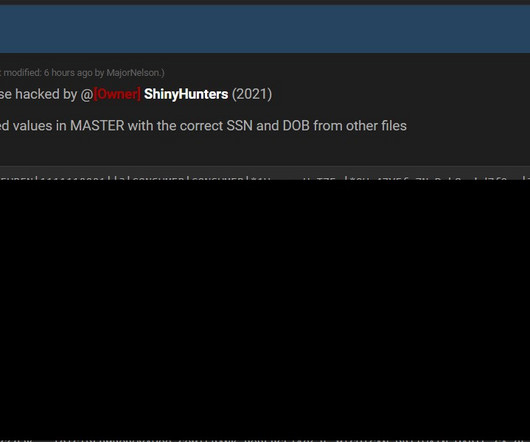
Researchers at vx-underground first noticed that more than 70,000,000 records from AT&T were leaked on the Breached hacking forum. More than 70,000,000 records from an unspecified division of AT&T were leaked onto Breached, vx-underground researchers reported. Today 70,000,000+ records from an unspecified division of AT&T were leaked onto Breached.

Penetration Testing
MARCH 17, 2024
Autodesk, a leader in the design and engineering software industry, has released critical security updates for several popular applications. These patches address two vulnerabilities (CVE-2024-23138 and CVE-2024-23139) that could have severe consequences for users... The post CVE-2024-23138 & 23139: Autodesk Patches Critical Flaws in Popular Design Software appeared first on Penetration Testing.
Cyber Security Informer brings together the best content for cyber security professionals from the widest variety of industry thought leaders.

Trend Micro
MARCH 17, 2024
Since early 2022, we have been monitoring an APT campaign that targets several government entities worldwide, with a strong focus in Southeast Asia, but also seen targeting Europe, America, and Africa.
Security Affairs
MARCH 17, 2024
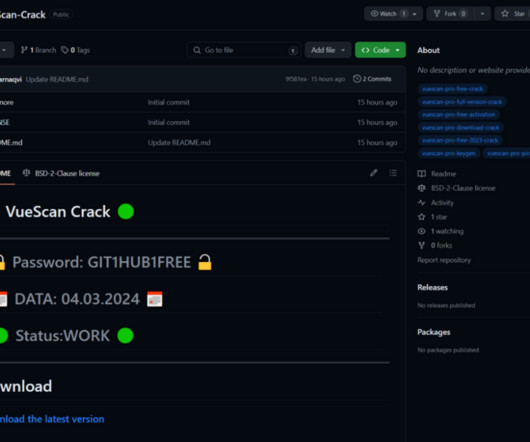
Cybersecurity researchers discovered multiple GitHub repositories hosting cracked software that are used to drop the RisePro info-stealer. G-Data researchers found at least 13 such Github repositories hosting cracked software designed to deliver the RisePro info-stealer. The experts noticed that this campaign was named “gitgub” by its operators. The researchers started the investigation following Arstechnica’s story about malicious Github repositories.

Bleeping Computer
MARCH 17, 2024
Researchers have demonstrated a new acoustic side-channel attack on keyboards that can deduce user input based on their typing patterns, even in poor conditions, such as environments with noise. [.

Security Affairs
MARCH 17, 2024
A new round of the weekly SecurityAffairs newsletter arrived! Every week the best security articles from Security Affairs are free for you in your email box. Enjoy a new round of the weekly SecurityAffairs newsletter, including the international press. France Travail data breach impacted 43 Million people Scranton School District in Pennsylvania suffered a ransomware attack Lazarus APT group returned to Tornado Cash to launder stolen funds Moldovan citizen sentenced in connection with the E-Root

Advertiser: Revenera
In a recent study, IDC found that 64% of organizations said they were already using open source in software development with a further 25% planning to in the next year. Most organizations are unaware of just how much open-source code is used and underestimate their dependency on it. As enterprises grow the use of open-source software, they face a new challenge: understanding the scope of open-source software that's being used throughout the organization and the corresponding exposure.

The Hacker News
MARCH 17, 2024
The Russia-linked threat actor known as APT28 has been linked to multiple ongoing phishing campaigns that employ lure documents imitating government and non-governmental organizations (NGOs) in Europe, the South Caucasus, Central Asia, and North and South America.

Penetration Testing
MARCH 17, 2024
A recent report by Cofense, an industry leader in email security, has uncovered two new alarming campaigns showcasing the rising threat of SVG files in the cybercrime world. SVG, which stands for Scalable Vector... The post SVG Files: The Emerging Vector of Cyber Threats appeared first on Penetration Testing.

Tech Republic Security
MARCH 17, 2024
Secure remote access to company systems and networks is now a way of life for most organizations. As corporate conglomerates, small businesses and brick-and-mortar shops fade away in favor of a distributed offsite workforce, companies and employees can profit from the greater convenience and efficiency provided by remote access. Combined with a bring your own.

Penetration Testing
MARCH 17, 2024
Cybersecurity researchers at Kroll have unveiled a worrisome advancement in the notorious SPARKRAT malware toolkit. A new, never-before-seen loader written in Golang is being actively used to sneak SPARKRAT onto targeted systems, allowing the... The post Stealthy New Loader Helps SPARKRAT Malware Evade Detection appeared first on Penetration Testing.

Advertisement
Within the past few years, ransomware attacks have turned to critical infrastructure, healthcare, and government entities. Attackers have taken advantage of the rapid shift to remote work and new technologies. Add to that hacktivism due to global conflicts and U.S. elections, and an increased focus on AI, and you have the perfect recipe for a knotty and turbulent 2024.
Security Boulevard
MARCH 17, 2024
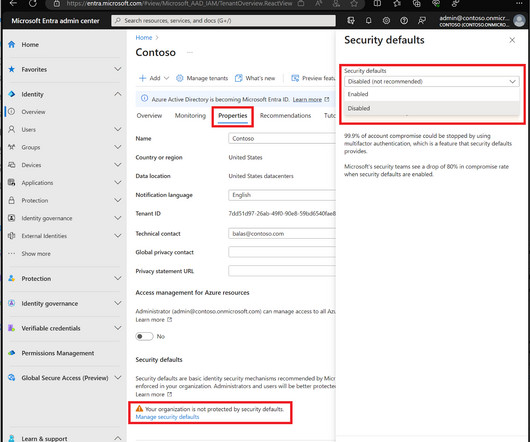
Here it is – everything you need to know about using Entra ID’s Conditional Access policies to boost your identity security posture. Microsoft Entra ID (formerly Azure Active Directory) is Microsoft’s cloud-based identity and access management service. It helps you manage and secure user identities, lets you synchronize legacy or on-premises identities to the cloud, The post Microsoft Entra ID: The Complete Guide to Conditional Access Policies appeared first on Rezonate.

Penetration Testing
MARCH 17, 2024
A disturbing new scam is exploiting the trust and warmth of senior citizens. Scammers are posing as wedding organizers and tricking victims into installing a dangerous app disguised as a “free wedding invite.” This... The post Urgent Alert: “Free Wedding Invite” Scam Targets Senior Citizens, Steals Sensitive Data appeared first on Penetration Testing.

Security Boulevard
MARCH 17, 2024
In this interview with white hat hacker Mishaal Khan, we learn about open source intelligence gathering and how to hack humans — or not. The post How to Think Like a Hacker — and Defend Your Data appeared first on Security Boulevard.

Trend Micro
MARCH 17, 2024
EU cybersecurity governing body European Union Agency for Cybersecurity (ENISA) recently named new DoS attack classifications in report after analyzing 310 attacks.

Advertisement
The healthcare industry has massively adopted web tracking tools, including pixels and trackers. Tracking tools on user-authenticated and unauthenticated web pages can access personal health information (PHI) such as IP addresses, medical record numbers, home and email addresses, appointment dates, or other info provided by users on pages and thus can violate HIPAA Rules that govern the Use of Online Tracking Technologies by HIPAA Covered Entities and Business Associates.

Security Boulevard
MARCH 17, 2024
Many thanks to USENIX for publishing their outstanding USENIX Security ’23 Presenter’s content, and the organizations strong commitment to Open Access. Originating from the conference’s events situated at the Anaheim Marriott ; and via the organizations YouTube channel. Permalink The post USENIX Security ’23 – Tanusree Sharma, Zhixuan Zhou, Andrew Miller, Yang Wang – A Mixed-Methods Study Of Security Practices Of Smart Contract Developers appeared first on Security Boulevard.

Security Boulevard
MARCH 17, 2024
I had the privilege of attending the Gartner IAM Summit in London. The conference focused on one of the most critical aspects of our digital world: identity-first security. After having some time to reflect, I’d like to share ten key takeaways from the event. Let’s dive in! The post 10 Takeaways from the 2024 Gartner IAM Summit UK appeared first on Rezonate.

Security Boulevard
MARCH 17, 2024
We've researched the top 5 OneTrust alternatives so you don't have to. Our list includes Scytale, Secureframe, AuditBoard, Drata, and Vanta. The post Top 5 Most Recommended OneTrust Alternatives appeared first on Scytale. The post Top 5 Most Recommended OneTrust Alternatives appeared first on Security Boulevard.

Security Boulevard
MARCH 17, 2024
In episode 321, the hosts discuss how connected cars are sharing driving data with insurance companies, potentially leading to increased rates for drivers. They also talk about the anti-TikTok bill passed by the House, which could force ByteDance to sell TikTok or face a ban in app stores. The episode also covers a significant update […] The post The TikTok Ban Bill, Your Car is Spying on You, Signal’s Username Update appeared first on Shared Security Podcast.

Advertisement
The losses companies suffered in 2023 ransomware attacks increased by 74% compared to those of the previous year, according to new data from the Federal Bureau of Investigation (FBI). The true figure is likely to be even higher, though, as many identity theft and phishing attacks go unreported. Ransomware attackers can potentially paralyze not just private sector organizations but also healthcare facilities, schools, and entire police departments.
Let's personalize your content