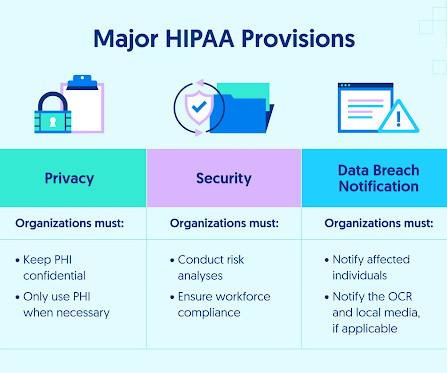
NIST Releases Cybersecurity Framework 2.0: What’s Next?
Lohrman on Security
MARCH 10, 2024
Many global cyber teams are analyzing cyber defense gaps now that the NIST Cybersecurity Framework 2.0 has been released. How will this guidance move the protection needle?

























Let's personalize your content