Improving C++
Schneier on Security
MARCH 15, 2024
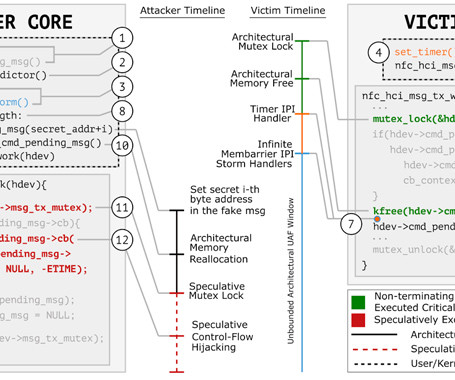
C++ guru Herb Sutter writes about how we can improve the programming language for better security. The immediate problem “is” that it’s Too Easy By Default™ to write security and safety vulnerabilities in C++ that would have been caught by stricter enforcement of known rules for type, bounds, initialization , and lifetime language safety.

































Let's personalize your content