Analysis of the FBI’s Anom Phone
Schneier on Security
JULY 12, 2021
Motherboard got its hands on one of those Anom phones that were really FBI honeypots. The details are interesting.

Schneier on Security
JULY 12, 2021
Motherboard got its hands on one of those Anom phones that were really FBI honeypots. The details are interesting.

Tech Republic Security
JULY 12, 2021
Dubbed Modipwn, the vulnerability affects a wide variety of Modicon programmable logic controllers used in manufacturing, utilities, automation and other roles.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

Security Boulevard
JULY 12, 2021
With the rise of IoT technology across every aspect of business, security convergence is quickly becoming the new norm. In a world where just about everything is connected to the internet and to other devices, old strategies are becoming obsolete. Treating IT and physical security as separate entities and ignoring physical security’s impact on cybersecurity.

Tech Republic Security
JULY 12, 2021
Messaging apps are becoming some of the most popular smartphone programs in the world, and that means more attempts to phish their users, Kaspersky finds.

Advertisement
How many people would you trust with your house keys? Chances are, you have a handful of trusted friends and family members who have an emergency copy, but you definitely wouldn’t hand those out too freely. You have stuff that’s worth protecting—and the more people that have access to your belongings, the higher the odds that something will go missing.

Security Boulevard
JULY 12, 2021
Data compromises have increased every month this year except May. If that trend continues, or even if there is only an average of 141 new compromises per month for the next six months, the total will still exceed the previous high of 1,632 breaches set in 2017. These were among the findings of the nonprofit. The post Phishing, Ransomware Driving Wave of Data Breaches appeared first on Security Boulevard.

Bleeping Computer
JULY 12, 2021
Interpol (International Criminal Police Organisation) Secretary General Jürgen Stock urged police agencies and industry partners to work together to prevent what looks like a future ransomware pandemic. [.].
Cyber Security Informer brings together the best content for cyber security professionals from the widest variety of industry thought leaders.

CSO Magazine
JULY 12, 2021
Several programmable logic controllers (PLCs) from Schneider Electric’s Modicon series that automate industrial processes in factories, energy utilities, HVAC systems and other installations are impacted by a flaw that could allow hackers to bypass their authentication mechanism and execute malicious code. According to researchers from security firm Armis, who found and reported the vulnerability, attackers with network access to impacted controllers could exploit the issue to install malware th
Security Affairs
JULY 12, 2021
Researchers from Cyber News Team have spotted threat actors offering for sale 600 million LinkedIn profiles scraped from the platform, again. Original post: [link]. For the third time in the past four months, LinkedIn seems to have experienced another massive data scrape conducted by a malicious actor. Once again, an archive of data collected from hundreds of millions of LinkedIn user profiles surfaced on a hacker forum, where it’s currently being sold for an undisclosed sum.

CSO Magazine
JULY 12, 2021
Despite the hype and gnashing of teeth over its hardware requirements, Windows 11 fundamentally shifts how Microsoft approaches both consumer and enterprise security. Even though the upgrade process from Windows 10 will be minor and more like a feature release of Windows 10, hardware requirements draw lines in the sand to make Windows more secure. The decision to move to Windows 11 will be different for each organization.

Graham Cluley
JULY 12, 2021
Clients of Spreadshirt, Spreadshop, and TeamShirts have been warned of a data breach which has seen the details of customers, partners, and employees fall into the lap of cybercriminals.

Advertiser: Revenera
In a recent study, IDC found that 64% of organizations said they were already using open source in software development with a further 25% planning to in the next year. Most organizations are unaware of just how much open-source code is used and underestimate their dependency on it. As enterprises grow the use of open-source software, they face a new challenge: understanding the scope of open-source software that's being used throughout the organization and the corresponding exposure.

Bleeping Computer
JULY 12, 2021
American fashion brand and retailer Guess is notifying affected customers of a data breach following a February ransomware attack that led to data theft. [.].
The Hacker News
JULY 12, 2021
Cybersecurity researchers are warning about a new malware that's striking online gambling companies in China via a watering hole attack to deploy either Cobalt Strike beacons or a previously undocumented Python-based backdoor called BIOPASS RAT that takes advantage of Open Broadcaster Software (OBS) Studio's live-streaming app to capture the screen of its victims to attackers.
Security Boulevard
JULY 12, 2021
The Cloud Impacts Application Security. Organizations everywhere are making their way into the cloud with some form of digital transformation initiative. As a part of these efforts, organizations usually have multiple strategies to execute as they move through their cloud journey, which includes focusing on delivering more value to their customers while positioning themselves for future investments in order to gain market share across their respective verticals.

CyberSecurity Insiders
JULY 12, 2021
German has declared the country’s first cyber catastrophe yesterday by stating that a cyber attack hit almost all the computer systems in the municipality of Anhalt Bitterfeld in the state of Saxony-Anhalt and disrupted completely. Authorities are unsure when the offices will reopen to the public and expect to resolve the issue within next 15 days. As the municipality was using obsolete hardware and software in the office, hackers easily gained access into the network and disrupted the digital o

Advertisement
Within the past few years, ransomware attacks have turned to critical infrastructure, healthcare, and government entities. Attackers have taken advantage of the rapid shift to remote work and new technologies. Add to that hacktivism due to global conflicts and U.S. elections, and an increased focus on AI, and you have the perfect recipe for a knotty and turbulent 2024.

Security Boulevard
JULY 12, 2021
Remember WYSIWYG? What you see is what you get. That was a simpler time in technology; you knew what the end result would be during the development stage. There were no surprises. Technology moved on, though. Now, the mantra should be, “don’t automatically believe what you see.” Deep fakes, propaganda, misinformation and disinformation campaigns are.
Security Affairs
JULY 12, 2021
Researchers spotted a new malware, dubbed BIOPASS, that sniffs victim’s screen by abusing the framework of Open Broadcaster Software (OBS) Studio. Researchers from Trend Micro spotted a new malware, dubbed BIOPASS, that sniffs the victim’s screen by abusing the framework of Open Broadcaster Software (OBS) Studio. Threat actors behind the new malware planted a malicious JavaScript code on support chat pages of Chinese gambling-related sites to redirect visitors to pages offering the malicious ins

Dark Reading
JULY 12, 2021
Microsoft Active Directory, ubiquitous across enterprises, has long been a primary target for attackers seeking network access and sensitive data.

Malwarebytes
JULY 12, 2021
Elon Musk is an incredibly popular target for scammers and spammers on social media. Attach his name to something he has no involvement in and watch it fly. Verified accounts on Twitter continue to be favourites for account compromise / fake Elon scams. Those often turn out to be Bitcoin related. Sometimes, it’s on a grand scale. There are other Elon scams out there, though.

Advertisement
The healthcare industry has massively adopted web tracking tools, including pixels and trackers. Tracking tools on user-authenticated and unauthenticated web pages can access personal health information (PHI) such as IP addresses, medical record numbers, home and email addresses, appointment dates, or other info provided by users on pages and thus can violate HIPAA Rules that govern the Use of Online Tracking Technologies by HIPAA Covered Entities and Business Associates.
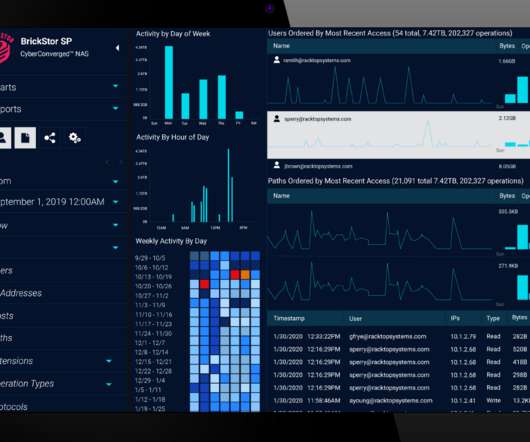
eSecurity Planet
JULY 12, 2021
While many cybersecurity vendors approach zero trust from the perspective of microsegmentation , shrinking the network as much as possible, one startup thinks security needs to be as close to the data as possible and is thus focused on data storage. Maryland-based RackTop Systems boasts a Department of Defense (DoD) pedigree, giving its founders a vantage point into the challenges that high-security environments face.

Security Boulevard
JULY 12, 2021
Preventing cyberattacks isn’t easy. If it were, there wouldn’t be a continuous stream of ransomware attacks dominating news feeds, nor would the president of the United States feel compelled to issue executive orders on cybersecurity or to declare that ransomware attacks should be treated like terrorism. While preventing cyberattacks isn’t easy, avoiding one is a.
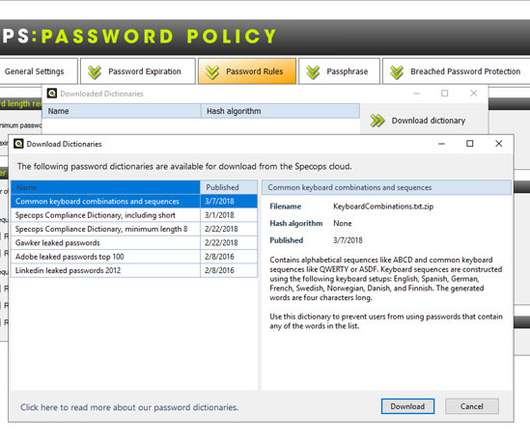
The Hacker News
JULY 12, 2021
Modern password policies are comprised of many different elements that contribute to its effectiveness. One of the components of an effective current password policy makes use of what is known as a custom dictionary that filters out certain words that are not allowed as passwords in the environment.

CSO Magazine
JULY 12, 2021
Databases hold vast amounts of personal information including some very sensitive tidbits, creating headaches for the companies that must curate them. Now, sophisticated tools and technologies are making it possible for database developers to have their cake and, to stay in metaphor, not count the calories by keeping the information private.

Advertisement
The losses companies suffered in 2023 ransomware attacks increased by 74% compared to those of the previous year, according to new data from the Federal Bureau of Investigation (FBI). The true figure is likely to be even higher, though, as many identity theft and phishing attacks go unreported. Ransomware attackers can potentially paralyze not just private sector organizations but also healthcare facilities, schools, and entire police departments.

Security Boulevard
JULY 12, 2021
Constella Regional Director, Lindsay Whyte, offers his 5 key takeaways from the event. The post ‘Shocking If True…’: 5 Takeaways from Tackling Misinformation 2021 appeared first on Constella. The post ‘Shocking If True…’: 5 Takeaways from Tackling Misinformation 2021 appeared first on Security Boulevard.

Tech Republic Security
JULY 12, 2021
Proofpoint security analysis details the latest attack that uses the lure of speaking at a conference to steal credentials.

SC Magazine
JULY 12, 2021
Medical staff members work in the COVID-19 ward nursing station at the United Memorial Medical Center on Dec. 29, 2020, in Houston. One CEO says allowlisting is ideal for health care security stacks. (Photo: Go Nakamura/Getty Images). A recent IDC report confirmed the health care sector is more vulnerable to the consequences of cyberattacks than other industries and the most likely to suffer application downtime, with 53% of covered entities reporting downtime after an attack.
Security Affairs
JULY 12, 2021
Magecart hackers continuously improve their exfiltration techniques to evade detection, they are hiding stolen credit card data into images. Magecart hackers have devised a new technique to obfuscating the malware within comment blocks and hide stolen credit card data into images evading detection. Hacker groups under the Magecart umbrella continue to target e-stores to steal payment card data with software skimmers.

Speaker: Blackberry, OSS Consultants, & Revenera
Software is complex, which makes threats to the software supply chain more real every day. 64% of organizations have been impacted by a software supply chain attack and 60% of data breaches are due to unpatched software vulnerabilities. In the U.S. alone, cyber losses totaled $10.3 billion in 2022. All of these stats beg the question, “Do you know what’s in your software?

CyberSecurity Insiders
JULY 12, 2021
Microsoft, the Tech giant from America has made it official that it is planning to acquire Cloud based Cyber Threat Detection offering business RiskIQ for an undisclosed amount. By gaining RiskIQ, Microsoft hopes to strengthen its position in cloud security business making companies gain better visibility and exposure to the internet. According to a report published in Bloomberg, the Satya Nadella led company is likely to invest $500 million appx to gain the entire business of RiskIQ and it will

Cisco Security
JULY 12, 2021
Chief Information Security Officers (CISOs) across the Global 2000 and Fortune 1000 are obsessed with protecting the workforce endpoints as critical vulnerabilities in the cybersecurity and risk management posture of their enterprises. CISOs focus on cybersecurity controls that operate mostly transparently and are focused on mitigating the potential risks to the computing infrastructure’s susceptibility to being breached as a result of actions taken by users, such as clicking on a malicious hype

SC Magazine
JULY 12, 2021
Jared Polis, at the time Colorado’s governor-elect, speaks at a 2018 election night rally. Governor Polis last week signed the Colorado Privacy Act into law. (Photo by Rick T. Wilking/Getty Images). Following in the footsteps of California and Virginia, Colorado last week became the third U.S. state to officially pass a comprehensive consumer privacy law.
Malwarebytes
JULY 12, 2021
Firefox recently announced that it will be rolling out DNS-over-HTTPS (or DoH) soon to one percent of its Canadian users as part of its partnership with CIRA (the Canadian Internet Registration Authority), the Ontario-based organization responsible for managing the.ca top-level domain for Canada and a local DoH provider. The rollout will begin on 20 July until every Firefox Canada user is reached in late September 2021.

Speaker: Erika R. Bales, Esq.
When we talk about “compliance and security," most companies want to ensure that steps are being taken to protect what they value most – people, data, real or personal property, intellectual property, digital assets, or any other number of other things - and it’s more important than ever that safeguards are in place. Let’s step back and focus on the idea that no matter how complicated the compliance and security regime, it should be able to be distilled down to a checklist.
Let's personalize your content