Apple’s Lockdown Mode
Schneier on Security
JULY 8, 2022
Apple has introduced lockdown mode for high-risk users who are concerned about nation-state attacks. It trades reduced functionality for increased security in a very interesting way.

Schneier on Security
JULY 8, 2022
Apple has introduced lockdown mode for high-risk users who are concerned about nation-state attacks. It trades reduced functionality for increased security in a very interesting way.

Tech Republic Security
JULY 8, 2022
The adoption of cloud was a necessity for many companies, but they are now facing security risks. The post Global cloud market to reach $1 trillion but 63% of leaders report lack of resources appeared first on TechRepublic.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.
Cisco Security
JULY 8, 2022
Managed services are an essential and fast-growing part of the security market, growing 14% annually. This opportunity presents new challenges MSPs must juggle day to day, including onboarding vendors and driving customer acquisition, all while making sure to provide robust IT solutions for your diverse set of clients. Clients are demanding more security and capabilities for a hybrid workforce, which provides a great opportunity for MSPs like you to grow your business.

Tech Republic Security
JULY 8, 2022
Only a quarter of the SMBs surveyed by the Cyber Readiness Institute require MFA among employees to sign into applications and devices. The post SMBs are behind in adopting multi-factor authentication appeared first on TechRepublic.

Speaker: Erroll Amacker
Automation is transforming finance but without strong financial oversight it can introduce more risk than reward. From missed discrepancies to strained vendor relationships, accounts payable automation needs a human touch to deliver lasting value. This session is your playbook to get automation right. We’ll explore how to balance speed with control, boost decision-making through human-machine collaboration, and unlock ROI with fewer errors, stronger fraud prevention, and smoother operations.

Malwarebytes
JULY 8, 2022
When content creators flag one of their own videos as inappropriate for children, we expect YouTube’s AI moderator to accept this and move on. But the video streaming bot doesn’t seem to get it. Not only can it prevent creators from correcting a miscategorization, its synthetic will is also final—no questions asked—unless the content creator appeals.

Graham Cluley
JULY 8, 2022
Things haven't gone as smoothly as Microsoft (and, indeed, the rest of us) might have hoped.
Cyber Security Informer brings together the best content for cyber security professionals from the widest variety of industry thought leaders.

eSecurity Planet
JULY 8, 2022
Disaster recovery (DR) and business continuity have been an essential aspect of enterprise IT for decades. Whether it’s earthquakes, floods, or power outages, DR is there to ensure operations can continue. But more recently, a lot more has been put on the DR plate. Ransomware has now emerged as one of the key reasons to have a DR plan and DR technology in place.
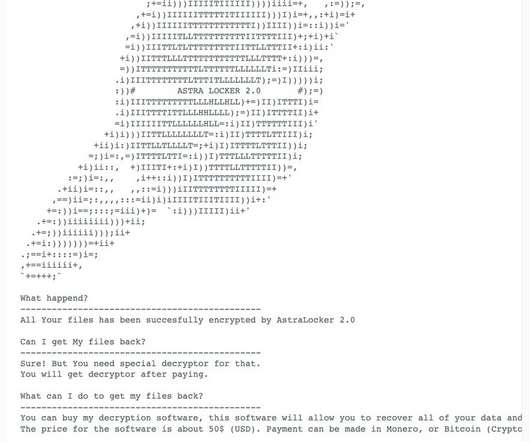
Security Affairs
JULY 8, 2022
Emsisoft has released a free decryption tool that allows victims of the AstraLocker and Yashma ransomware to recover their files without paying a ransom. Cybersecurity firm Emsisoft released a free decryptor tool that allows victims of the AstraLocker and Yashma ransomware to recover their files without paying a ransom. The security firm states that the AstraLocker decryptor works for ransomware versions based on the Babuk malware that appends the.Astra or.babyk extensions to the name of the enc

eSecurity Planet
JULY 8, 2022
A six-year quantum cryptography competition just ended, producing four new security standards selected by the U.S. Department of Commerce’s National Institute of Standards and Technology. The announcement comes on the heels of a few major strides in quantum computing accessibility and speed—and may hopefully stave off the growing quantum security threat.

Malwarebytes
JULY 8, 2022
Federal government organisations in Brazil may need to reassess their approach to cyberthreats, according to a new report by the country’s Federal Audit Court. It outlines multiple key areas of concern across 29 key areas of risk. One of the biggest problems in the cybercrime section of the report relates to backups. Specifically: The lack of backups when dealing with hacking incidents.

Advertisement
Many cybersecurity awareness platforms offer massive content libraries, yet they fail to enhance employees’ cyber resilience. Without structured, engaging, and personalized training, employees struggle to retain and apply key cybersecurity principles. Phished.io explains why organizations should focus on interactive, scenario-based learning rather than overwhelming employees with excessive content.

Security Affairs
JULY 8, 2022
Cisco fixed a critical vulnerability in the Cisco Expressway series and TelePresence Video Communication Server (VCS) products. Cisco released security patches to address a critical vulnerability, tracked as CVE-2022-20812 (CVSS score of 9.0), in the Expressway series and TelePresence Video Communication Server (VCS). A remote attacker can trigger the flaw to overwrite files on the underlying operating system with root privileges.

Security Boulevard
JULY 8, 2022
Normalyze has emerged from stealth with an agentless platform that employs graph technology to enable IT teams to discover data in the cloud, classify it and identify the most likely attack paths cybercriminals could use to access it. Fresh from raising an additional $22.2 million in Series A funding, Normalyze CEO Amer Deeba said the. The post Normalyze Emerges to Simplify Cloud Data Security appeared first on Security Boulevard.
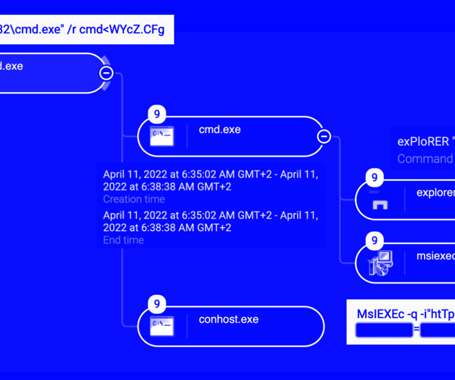
The Hacker News
JULY 8, 2022
Cybersecurity researchers are drawing attention to an ongoing wave of attacks linked to a threat cluster tracked as Raspberry Robin that's behind a Windows malware with worm-like capabilities. Describing it as a "persistent" and "spreading" threat, Cybereason said it observed a number of victims in Europe.

We Live Security
JULY 8, 2022
Scammers don't take the summer off – be on your guard when buying your Crit'Air sticker. The post Driving to France this summer? Watch out for scam websites before you go appeared first on WeLiveSecurity.

Advertisement
The DHS compliance audit clock is ticking on Zero Trust. Government agencies can no longer ignore or delay their Zero Trust initiatives. During this virtual panel discussion—featuring Kelly Fuller Gordon, Founder and CEO of RisX, Chris Wild, Zero Trust subject matter expert at Zermount, Inc., and Principal of Cybersecurity Practice at Eliassen Group, Trey Gannon—you’ll gain a detailed understanding of the Federal Zero Trust mandate, its requirements, milestones, and deadlines.
Security Boulevard
JULY 8, 2022
The cybersecurity skills shortage, the increasing number and sophistication of attacks and savvy and aggressive cybercriminal gangs have created a perfect storm for cybersecurity teams. Defending networks, endpoints and data seems like a Herculean task some days. The advent of artificial intelligence and machine learning (AI/ML) tools has offered some relief, and organizations have been.
Bleeping Computer
JULY 8, 2022
A new ransomware operation named '0mega' targets organizations worldwide in double-extortion attacks and demands millions of dollars in ransoms. [.].

Security Boulevard
JULY 8, 2022
Microsoft stunned security professionals by reversing a change that prevents Office from auto-running macros. The post STUPID Microsoft U-Turn: Unblocks Malicious Macros in Office appeared first on Security Boulevard.

We Live Security
JULY 8, 2022
Vacations are a great time to unwind, but if you're not careful, you may face a digital disaster. Here's how to keep your devices and data secure while you're on the move. The post Avoid travel digital disasters – Week in security with Tony Anscombe appeared first on WeLiveSecurity.

Speaker: Sierre Lindgren
Fraud is a battle that every organization must face – it’s no longer a question of “if” but “when.” Every organization is a potential target for fraud, and the finance department is often the bullseye. From cleverly disguised emails to fraudulent payment requests, the tactics of cybercriminals are advancing rapidly. Drawing insights from real-world cases and industry expertise, we’ll explore the vulnerabilities in your processes and how to fortify them effectively.

Security Boulevard
JULY 8, 2022
When you are hit with a ransomware attack, you typically have a few options. You can restore from backups (if you have backups). You can rebuild your network and all the devices on it. Or you can pay the ransom. Which of these tactics you decide to take is frequently dependent upon the cost of. The post States Prohibit Ransomware Payments appeared first on Security Boulevard.

Bleeping Computer
JULY 8, 2022
Onur Aksoy, the CEO of a group of dozens of companies, was indicted for allegedly selling more than $1 billion worth of counterfeit Cisco network equipment to customers worldwide, including health, military, and government organizations. [.].

Security Boulevard
JULY 8, 2022
A survey of 1,121 IT decision-makers at organizations with 100 to 2,500 employees that have more than 5TB of data found that as the volume of ransomware attacks rises, less than a quarter (23%) of respondents were confident in their ability to recover lost data. The survey, conducted by Dimensional Research on behalf of Arcserve, The post Survey Reveals Lack of Confidence in Ability to Recover Data appeared first on Security Boulevard.

Security Affairs
JULY 8, 2022
The operators behind the TrickBot malware are systematically targeting Ukraine since the beginning of the war in February 2022. IBM researchers collected evidence indicating that the Russia-based cybercriminal Trickbot group (aka Wizard Spider , DEV-0193, ITG23 ) has been systematically attacking Ukraine since the beginning of the Russian invasion of the country.

Advertisement
Keeper Security is transforming cybersecurity for people and organizations around the world. Keeper’s affordable and easy-to-use solutions are built on a foundation of zero-trust and zero-knowledge security to protect every user on every device. Our next-generation privileged access management solution deploys in minutes and seamlessly integrates with any tech stack to prevent breaches, reduce help desk costs and ensure compliance.

Security Boulevard
JULY 8, 2022
The modern world is data-driven. Consequently, thriving businesses have access to lots of data—financial data, logistic data, employee data, customer data and more. The way a business handles this enormous volume of data is an excellent indicator of success in the modern business landscape. Data privacy simply refers to how your business ensures that it.
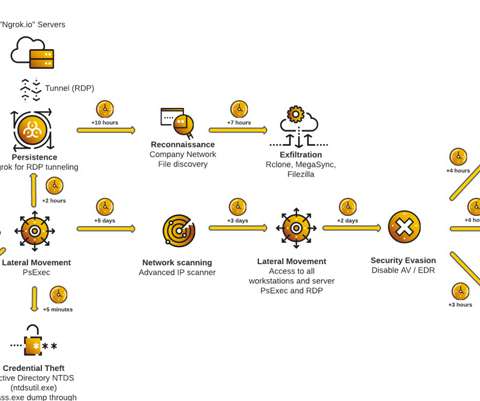
The Hacker News
JULY 8, 2022
LockBit ransomware attacks are constantly evolving by making use of a wide range of techniques to infect targets while also taking steps to disable endpoint security solutions. "The affiliates that use LockBit's services conduct their attacks according to their preference and use different tools and techniques to achieve their goal," Cybereason security analysts Loïc Castel and Gal Romano said.

Security Boulevard
JULY 8, 2022
New details emerge on China's colossal data breach, NIST announces four candidates for post-quantum cryptography algorithms, the most dangerous software weaknesses of 2022. The post Cybersecurity News Round-Up: Week of July 4, 2022 appeared first on Security Boulevard.

Bleeping Computer
JULY 8, 2022
Microsoft has fixed a known issue that was causing Office applications like Word and Excel to crash when working with cloud documents. [.].

Advertisement
Many software teams have migrated their testing and production workloads to the cloud, yet development environments often remain tied to outdated local setups, limiting efficiency and growth. This is where Coder comes in. In our 101 Coder webinar, you’ll explore how cloud-based development environments can unlock new levels of productivity. Discover how to transition from local setups to a secure, cloud-powered ecosystem with ease.

CSO Magazine
JULY 8, 2022
A cybersecurity advisory about the ransomware known as Maui has been issued by the FBI, CISA and U.S. Treasury Department. The agencies assert that North Korean state-sponsored cyber actors have used the malware since at least May 2021 to target healthcare and public health sector organizations. The FBI surmises that the threat actors are targeting healthcare organizations because those entities are critical to human life and health, so they're more likely to pay ransoms rather than risk disrupt
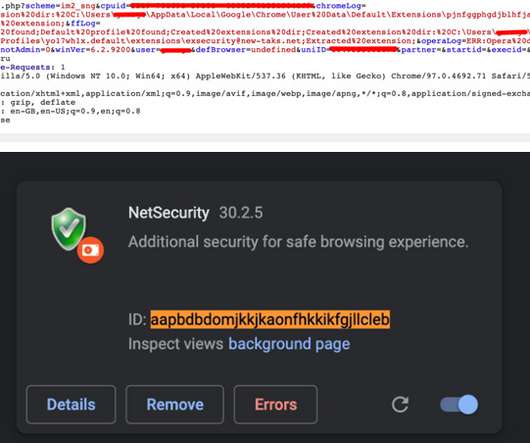
The Hacker News
JULY 8, 2022
A malicious browser extension with 350 variants is masquerading as a Google Translate add-on as part of an adware campaign targeting Russian users of Google Chrome, Opera, and Mozilla Firefox browsers.

CSO Magazine
JULY 8, 2022
In a move to broaden its portfolio of cybersecurity products, Boston-based threat intelligence collection and analysis firm Recorded Future has reached an agreement to purchase Dutch malware analysis company Hatching Recorded Future offers a wide range of different types of intelligence on digital threats, using proprietary predictive analytics to track public documents, potentially compromised credentials, and dark web traffic for insights into potential threats to client organizations.

Dark Reading
JULY 8, 2022
Dark Reading's digest of the other don't-miss stories of the week, including a new ransomware targeting QNAP gear, and a destructive attack against the College of the Desert that lingers on.

Advertisement
After a year of sporadic hiring and uncertain investment areas, tech leaders are scrambling to figure out what’s next. This whitepaper reveals how tech leaders are hiring and investing for the future. Download today to learn more!
Let's personalize your content