Security Risks of New.zip and.mov Domains
Schneier on Security
MAY 19, 2023
Researchers are worried about Google’s.zip and.mov domains, because they are confusing. Mistaking a URL for a filename could be a security vulnerability.

Schneier on Security
MAY 19, 2023
Researchers are worried about Google’s.zip and.mov domains, because they are confusing. Mistaking a URL for a filename could be a security vulnerability.

Tech Republic Security
MAY 19, 2023
New BEC cyberattacks use phishing with a legitimate Dropbox link as a lure for malware and credentials theft. The post How business email compromise attacks emulate legitimate web services to lure clicks appeared first on TechRepublic.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

Bleeping Computer
MAY 19, 2023
ASUS has apologized to its customers for a server-side security maintenance error that has caused a wide range of impacted router models to lose network connectivity. [.

Security Boulevard
MAY 19, 2023
Om Nom Nom Nom Nom: Privacy Sandbox inching towards reality. But concerns remain. The post Google Chrome 3rd Party Cookies Crumbling — Finally! appeared first on Security Boulevard.

Speaker: Erroll Amacker
Automation is transforming finance but without strong financial oversight it can introduce more risk than reward. From missed discrepancies to strained vendor relationships, accounts payable automation needs a human touch to deliver lasting value. This session is your playbook to get automation right. We’ll explore how to balance speed with control, boost decision-making through human-machine collaboration, and unlock ROI with fewer errors, stronger fraud prevention, and smoother operations.

Graham Cluley
MAY 19, 2023
A joint alert has been issued by US government agencies, advising organisations of the steps they should take to mitigate the threat posed by BianLian ransomware attacks.

Bleeping Computer
MAY 19, 2023
CISA warned today of a security vulnerability affecting Samsung devices used in attacks to bypass Android address space layout randomization (ASLR) protection. [.
Cyber Security Informer brings together the best content for cyber security professionals from the widest variety of industry thought leaders.
The Hacker News
MAY 19, 2023
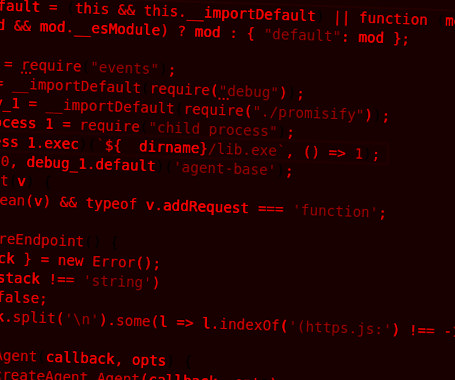
Two malicious packages discovered in the npm package repository have been found to conceal an open source information stealer malware called TurkoRat. The packages – named nodejs-encrypt-agent and nodejs-cookie-proxy-agent – were collectively downloaded approximately 1,200 times and were available for more than two months before they were identified and taken down.

Security Boulevard
MAY 19, 2023
This blog post explores the DevSecOps best practices that development teams can use to ensure that security is ingrained in the development process. The post 7 Essential DevSecOps Best Practices Every Development Team Should Implement appeared first on Security Boulevard.

The Hacker News
MAY 19, 2023
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) warned of active exploitation of a medium-severity flaw affecting Samsung devices. The issue, tracked as CVE-2023-21492 (CVSS score: 4.4), impacts select Samsung devices running Android versions 11, 12, and 13.

Bleeping Computer
MAY 19, 2023
Luxottica has confirmed one of its partners suffered a data breach in 2021 that exposed the personal information of 70 million customers after a database was posted this month for free on hacking forums. [.

Advertisement
Many cybersecurity awareness platforms offer massive content libraries, yet they fail to enhance employees’ cyber resilience. Without structured, engaging, and personalized training, employees struggle to retain and apply key cybersecurity principles. Phished.io explains why organizations should focus on interactive, scenario-based learning rather than overwhelming employees with excessive content.

CyberSecurity Insiders
MAY 19, 2023
By Aaron Sandeen, CEO and co-founder at Securin Since June 2021, Hive Ransomware has been dominating the ransomware scene. Their reach has affected more than 1,500 organizations resulting in Hive receiving ransom payments totaling $100 million. With all the buzz they have created, it’s no wonder they have earned the title of one of the most prolific ransomware groups.

The Last Watchdog
MAY 19, 2023
The ransomware plague endures — and has arisen as a potent weapon in geopolitical conflicts. Related: The Golden Age of cyber espionage Cyber extortion remains a material threat to organizations of all sizes across all industries. Ransomware purveyors have demonstrated their capability to endlessly take advantage of a vastly expanded network attack surface – one that will only continue to expand as the shift to massively interconnected digital services accelerates.

CSO Magazine
MAY 19, 2023
The UK National Cyber Security Centre (NCSC) has urged businesses and security leaders to make accessibility a cybersecurity priority to help make systems more secure and human errors/workarounds less likely. It can also aid in meeting legal requirements, delivering better operational outcomes, and attracting and retaining more diverse talent, according to the NCSC.

Dark Reading
MAY 19, 2023
As we share an increasing amount of personal information online, we create more opportunities for threat actors to steal our identities.

Advertisement
The DHS compliance audit clock is ticking on Zero Trust. Government agencies can no longer ignore or delay their Zero Trust initiatives. During this virtual panel discussion—featuring Kelly Fuller Gordon, Founder and CEO of RisX, Chris Wild, Zero Trust subject matter expert at Zermount, Inc., and Principal of Cybersecurity Practice at Eliassen Group, Trey Gannon—you’ll gain a detailed understanding of the Federal Zero Trust mandate, its requirements, milestones, and deadlines.

CSO Magazine
MAY 19, 2023
Cybercrime gang Lemon Group has managed to get malware known as Guerrilla preinstalled on about 8.9 million Android-based smartphones, watches, TVs, and TV boxes globally, according to Trend Micro. The Guerilla malware can load additional payloads, intercept one-time passwords (OTPs) from SMS texts, set up a reverse proxy from the infected device, and infiltrate WhatsApp sessions.

The Hacker News
MAY 19, 2023
The notorious cybercrime group known as FIN7 has been observed deploying Cl0p (aka Clop) ransomware, marking the threat actor's first ransomware campaign since late 2021. Microsoft, which detected the activity in April 2023, is tracking the financially motivated actor under its new taxonomy Sangria Tempest.

Security Boulevard
MAY 19, 2023
It’s no secret that sensitive data management is a top priority for security teams, particularly during periods of widespread workforce changes like layoffs and pay reductions. But workforce volatility has made it increasingly difficult for organizations to prevent and resolve issues of insider threat and data loss. Without the proper workflows (backed by powerful tools […] The post How Companies Should Protect Sensitive Data: 6 Practical Tips appeared first on Code42.

CyberSecurity Insiders
MAY 19, 2023
Over the past couple of years, a peculiar social media trend known as the Kia Challenge has gained traction on various platforms such as Facebook, Twitter, Telegram, and WhatsApp. This challenge involves a group of thieves called the Kia Boyz, who promote an instructional video link guiding viewers to YouTube and TikTok. The video provides instructions on how to bypass the security systems of Hyundai and Kia cars using a basic USB cable that can be easily obtained from online platforms like Amaz

Speaker: Sierre Lindgren
Fraud is a battle that every organization must face – it’s no longer a question of “if” but “when.” Every organization is a potential target for fraud, and the finance department is often the bullseye. From cleverly disguised emails to fraudulent payment requests, the tactics of cybercriminals are advancing rapidly. Drawing insights from real-world cases and industry expertise, we’ll explore the vulnerabilities in your processes and how to fortify them effectively.

Security Boulevard
MAY 19, 2023
Insight #1 " Be extremely careful of ChatGPT lookalikes and fakes as scammers are taking advantage of the buzz and tricking victims into biting." Insight #2 " There is no need for.zip or.mov top-level domains (TLD) unless you are a malicious actor. These should be removed immediately." Insight #3 " Burnout is a real problem in security. As security leaders, we need to figure out how to put out the fire before more great people leave the industry.

We Live Security
MAY 19, 2023
Don't download software from non-reputable websites and sketchy links – you might be in for more than you bargained for The post The real cost of a free lunch – Week in security with Tony Anscombe appeared first on WeLiveSecurity

Security Boulevard
MAY 19, 2023
It’s popular because it’s profitable and it’s been a big moment for ransomware around the planet over the past few weeks. At Banyan, we decided to assemble the latest ransomware news for a mid-May Ransomware Threat Update (because there’s been enough of it to warrant its own blog). Ransomware has become ever more targeted, with […] The post Banyan Ransomware Threat Update – May 2023 first appeared on Banyan Security.

CSO Magazine
MAY 19, 2023
Despite efforts taken in recent years to proactively monitor public software repositories for malicious code, packages that bundle malware continue to routinely pop up in such places. Researchers recently identified two legitimate looking packages that remained undetected for over two months and deployed an open-source information stealing trojan called TurkoRat.

Advertisement
Keeper Security is transforming cybersecurity for people and organizations around the world. Keeper’s affordable and easy-to-use solutions are built on a foundation of zero-trust and zero-knowledge security to protect every user on every device. Our next-generation privileged access management solution deploys in minutes and seamlessly integrates with any tech stack to prevent breaches, reduce help desk costs and ensure compliance.
The Hacker News
MAY 19, 2023
Google has announced plans to officially flip the switch on its twice-delayed Privacy Sandbox initiatives as it slowly works its way to deprecate support for third-party cookies in Chrome browser. To that end, the search and advertising giant said it intends to phase out third-party cookies for 1% of Chrome users globally in the first quarter of 2024.

eSecurity Planet
MAY 19, 2023
Application security tools and software solutions are designed to identify and mitigate vulnerabilities and threats in software applications. Their main purpose is to protect applications from unauthorized access, data breaches, and malicious attacks. These tools play a vital role in ensuring the security, integrity, and confidentiality of sensitive information, such as personal data and financial records.

Dark Reading
MAY 19, 2023
In an advisory released by the company, Apple revealed patches for three previously unknown bugs it says may already have been used by attackers.

Bleeping Computer
MAY 19, 2023
Dish Network, an American television provider, most likely paid a ransom after being hit by a ransomware attack in February based on the wording used in data breach notification letters sent to impacted employees. [.

Advertisement
Many software teams have migrated their testing and production workloads to the cloud, yet development environments often remain tied to outdated local setups, limiting efficiency and growth. This is where Coder comes in. In our 101 Coder webinar, you’ll explore how cloud-based development environments can unlock new levels of productivity. Discover how to transition from local setups to a secure, cloud-powered ecosystem with ease.

Dark Reading
MAY 19, 2023
The data shows how most cyberattacks start, so basic steps can help organizations avoid becoming the latest statistic.

Security Affairs
MAY 19, 2023
Vesuvius, a leader in molten metal flow engineering and technology, revealed that the February cyber incident will cost it £3.5 million Vesuvius is a global leader in molten metal flow engineering and technology, it employs more than 10,000 people and is listed on the London Stock Exchange. In February the company disclosed a security breach and revealed that it discovered unauthorized access to its systems.

Heimadal Security
MAY 19, 2023
Nearly 9 million Android-based smartphones, watches, TVs, and TV boxes have been infected with the “Guerrilla” malware, pre-installed on the devices by Lemon Group. The threat actors use the malware to load additional payloads, intercept one-time passwords from SMS, set up reverse proxy from the infected device, hijack WhatsApp sessions, and more. Cybersecurity researchers identified […] The post Lemon Gang Pre-Infects 9 Million Android Devices With Malware appeared first on Heimdal Securi

Security Affairs
MAY 19, 2023
The Lemon Group cybercrime ring has reportedly pre-installed malware known as Guerilla on almost 9 million Android devices. A cybercrime group tracked has Lemon Group has reportedly pre-installed malware known as Guerilla on almost 9 million Android devices. Infected devices were used for multiple malicious activities, including traffic redirections through mobile proxies, info-stealing, click fraud, and social media and online messaging accounts and monetization via advertisements.

Advertisement
After a year of sporadic hiring and uncertain investment areas, tech leaders are scrambling to figure out what’s next. This whitepaper reveals how tech leaders are hiring and investing for the future. Download today to learn more!
Let's personalize your content