On Cell Phone Metadata
Schneier on Security
NOVEMBER 2, 2021
Interesting Twitter thread on how cell phone metadata can be used to identify and track people who don’t want to be identified and tracked.

Schneier on Security
NOVEMBER 2, 2021
Interesting Twitter thread on how cell phone metadata can be used to identify and track people who don’t want to be identified and tracked.
Krebs on Security
NOVEMBER 2, 2021
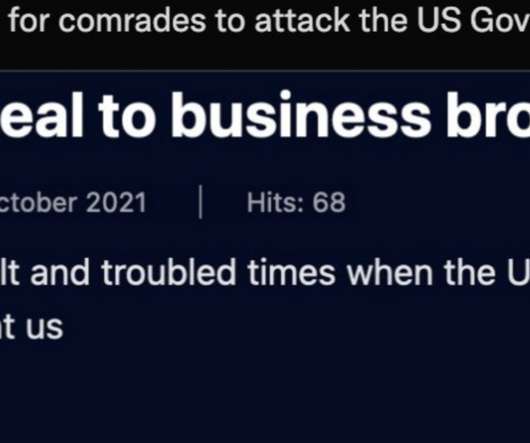
A number of publications in September warned about the emergence of “ Groove ,” a new ransomware group that called on competing extortion gangs to unite in attacking U.S. government interests online. It now appears that Groove was all a big hoax designed to toy with security firms and journalists. “An appeal to business brothers!” reads the Oct. 22 post from Groove calling for attacks on the United States government sector.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

Javvad Malik
NOVEMBER 2, 2021
We were told that by now, we would live in a perfect world with flying cars. But that hasn’t arrived yet. We also believed that cybersecurity would be a problem that would have been solved, but it just seems to be getting worse. But what if the problem isn’t getting worse. What if we have solved cybersecurity and we do have flying cars – we’re just not looking at things in the right way.

Thales Cloud Protection & Licensing
NOVEMBER 2, 2021
Quantum Resistant Encryption – Are You Ready? madhav. Tue, 11/02/2021 - 09:10. . Some good news and a couple of tips for being prepared. Over the past few months, a handful of Thales CPL clients have mentioned their concern regarding the future threat of quantum computing to their data security frameworks. If you take a good hard look at the risks arising from Quantum, there is bad news and good news.

Advertisement
How many people would you trust with your house keys? Chances are, you have a handful of trusted friends and family members who have an emergency copy, but you definitely wouldn’t hand those out too freely. You have stuff that’s worth protecting—and the more people that have access to your belongings, the higher the odds that something will go missing.
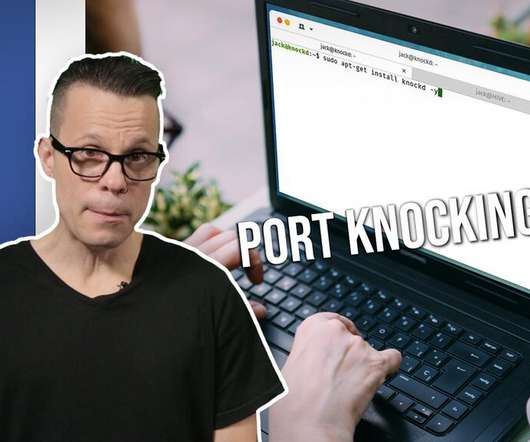
Tech Republic Security
NOVEMBER 2, 2021
You need to lock down your servers so that only you have access via SSH. One way to help that is with knockd. Jack Wallen shows you how.

Security Boulevard
NOVEMBER 2, 2021
Trojan Source “threatens the security of all code,” screams a widely shared article. Poppycock. There’s nothing new here. The post ‘Trojan Source’ Makes Scary Headlines—But it’s Not New appeared first on Security Boulevard.
Cyber Security Informer brings together the best content for cyber security professionals from the widest variety of industry thought leaders.

CSO Magazine
NOVEMBER 2, 2021
Cybersecurity buzzwords and buzz phrases are a dime a dozen. Used to simplify complex terminology or boost sales and marketing campaigns, buzzwords are an inescapable reality for an innovative and fast-paced industry like information security. However, such terms are not always helpful and can be inaccurate, outdated, misleading, or even risk causing harm.

Quick Heal Antivirus
NOVEMBER 2, 2021
What is WSL? The Windows Subsystem for Linux (WSL) is a resource inside the Windows operating system that. The post Stay Alert – Malware Authors Deploy ELF as Windows Loaders to Exploit WSL feature appeared first on Quick Heal Blog | Latest computer security news, tips, and advice.

Security Affairs
NOVEMBER 2, 2021
Researchers warn of a now-fixed critical remote code execution (RCE) vulnerability in GitLab ‘s web interface actively exploited in the wild. Cybersecurity researchers warn of a now-patched critical remote code execution (RCE) vulnerability, tracked as CVE-2021-22205 , in GitLab’s web interface that has been actively exploited in the wild.

CSO Magazine
NOVEMBER 2, 2021
The Google Play store has become better in recent years at policing malware, raising the bar for attackers, but well-crafted stealthy Trojans continue to slip in from time to time. Such is the case of AbstractEmu, a recently discovered threat masquerading as utility apps and capable of gaining full control over devices through root exploits. "This is a significant discovery because widely distributed malware with root capabilities have become rare over the past five years," researchers from secu

Advertiser: Revenera
In a recent study, IDC found that 64% of organizations said they were already using open source in software development with a further 25% planning to in the next year. Most organizations are unaware of just how much open-source code is used and underestimate their dependency on it. As enterprises grow the use of open-source software, they face a new challenge: understanding the scope of open-source software that's being used throughout the organization and the corresponding exposure.

Bleeping Computer
NOVEMBER 2, 2021
The Federal Bureau of Investigation (FBI) warns that ransomware gangs are targeting companies involved in "time-sensitive financial events" such as corporate mergers and acquisitions to make it easier to extort their victims. [.].

CSO Magazine
NOVEMBER 2, 2021
The smartphone revolution was supposed to provide a second chance for the tech industry to roll out a secure computing platform. These new devices were purported to be locked down and immune to malware, unlike buggy PCs and vulnerable servers. But it turns out that phones are still computers and their users are still people, and computers and people will always be weak links.
Security Affairs
NOVEMBER 2, 2021
Google’s Android November 2021 security updates address a zero-day vulnerability in the Kernel that is actively exploited in the wild. Google’s Android November 2021 security updates addressed 18 vulnerabilities in the framework and system components and 18 issues in the kernel and vendor components. One of these issues, tracked as CVE-2021-1048, is a use-after-free (UAF) vulnerability in the kernel that could be exploited for privilege escalation.

CSO Magazine
NOVEMBER 2, 2021
Endpoints have become the preferred target for cybercriminals today, as more corporate users and devices operate at home and beyond the protection of traditional security controls. In fact, according to a 2020 Ponemon Institute study , 68% of organizations reported that the volume of endpoint-specific attacks increased over the previous year. While useful for preventing known threats and malicious activity, legacy endpoint protection platform (EPP) solutions alone are simply no longer fit for th

Advertisement
Within the past few years, ransomware attacks have turned to critical infrastructure, healthcare, and government entities. Attackers have taken advantage of the rapid shift to remote work and new technologies. Add to that hacktivism due to global conflicts and U.S. elections, and an increased focus on AI, and you have the perfect recipe for a knotty and turbulent 2024.

Malwarebytes
NOVEMBER 2, 2021
Weeks ago, we talked about the one effective lure that could get a Discord user to consider clicking on a scam link they were generously given, either by a random user or a legitimate contact who also happened to have fallen for the same ploy: free Discord Nitro subscriptions. And similar to how scammers repeatedly prey on Discord users, they also prey on Steam users (Remember that “I accidentally reported you” scam?).

Bleeping Computer
NOVEMBER 2, 2021
Google has released the Android November 2021 security updates, which address 18 vulnerabilities in the framework and system components, and 18 more flaws in the kernel and vendor components. [.].

Malwarebytes
NOVEMBER 2, 2021
The news is currently jam-packed with tales of Facebook’s Meta project. Of particular interest to me is Facebook’s long-stated desire to introduce adverts into the VR space, and what this may mean for Meta too. I’ve talked about the privacy and legal aspects of adverts in gaming and other tech activities many times down the years. An advert in every home.

Security Affairs
NOVEMBER 2, 2021
Google is going to increase the bounty for finding and exploiting privilege escalation vulnerabilities in the Linux kernel. Good news for white hat hackers, Google is going to increase the bounty for demonstrating privilege escalation vulnerabilities in the Linux kernel. The payouts for privilege escalation exploits using a known vulnerability will be up to US$31,337, while zero-day exploits will be awarded a payout of $50,337.

Advertisement
The healthcare industry has massively adopted web tracking tools, including pixels and trackers. Tracking tools on user-authenticated and unauthenticated web pages can access personal health information (PHI) such as IP addresses, medical record numbers, home and email addresses, appointment dates, or other info provided by users on pages and thus can violate HIPAA Rules that govern the Use of Online Tracking Technologies by HIPAA Covered Entities and Business Associates.

CyberSecurity Insiders
NOVEMBER 2, 2021
A recent study made by Javelin Strategy & Research says that the annual loss incurred through Child Identity Theft and Fraud in United States is $1 billion worth. Authored by Tracy Kitten, the report states that those children who are using Twitch, Twitter and Facebook are most likely being hit by a cyber attack, exposing their personal data through a data breach.

InfoWorld on Security
NOVEMBER 2, 2021
Containers, certainly containers running on public clouds, are really old hat by now. These self-contained, lightweight software packages come with their own runtime environment and are relocatable from platform to platform, typically without significant changes to code. Containers include an application as well as its dependencies, such as libraries, other binaries, and configuration files needed to run them.
CyberSecurity Insiders
NOVEMBER 2, 2021
Facebook has proclaimed that it will stop autonomous identification of faces of its users by putting an end to its in-house Facial Recognition (FR) Program. The decision was taken after over 639 million active users opted out of the service. From now on, the Mark Zuckerberg’s led company faced a lawsuit against its facial recognition related data collection early this year.

Security Boulevard
NOVEMBER 2, 2021
Considering that 40% of organizations have fallen victim to a cloud-based breach in the last year, it would seem they would put a premium on safeguarding their data in the cloud. But the 2021 Thales Global Cloud Security says differently. Most—a whopping 83%—have failed to encrypt even half the sensitive data they have tucked away. The post Companies Fail to Encrypt, Protect Data in the Cloud appeared first on Security Boulevard.

Advertisement
The losses companies suffered in 2023 ransomware attacks increased by 74% compared to those of the previous year, according to new data from the Federal Bureau of Investigation (FBI). The true figure is likely to be even higher, though, as many identity theft and phishing attacks go unreported. Ransomware attackers can potentially paralyze not just private sector organizations but also healthcare facilities, schools, and entire police departments.

We Live Security
NOVEMBER 2, 2021
On top of illegally streaming sports games for profit, the man is also believed to have attempted to extort MLB for $150,000. The post Man charged with hacking major US sports leagues to illegally stream games appeared first on WeLiveSecurity.

The Hacker News
NOVEMBER 2, 2021
A now-patched critical remote code execution (RCE) vulnerability in GitLab's web interface has been detected as actively exploited in the wild, cybersecurity researchers warn, rendering a large number of internet-facing GitLab instances susceptible to attacks. Tracked as CVE-2021-22205, the issue relates to an improper validation of user-provided images that results in arbitrary code execution.

Bleeping Computer
NOVEMBER 2, 2021
Facebook announced today that they will no longer use the Face Recognition system on their platform and will be deleting over 1 billion people's facial recognition profiles. [.].

CyberSecurity Insiders
NOVEMBER 2, 2021
COVID-19 has accelerated a consumer shift online, urging people to rethink the way they purchase goods and services. Lockdowns and heightened concerns around health and safety have resulted in soaring numbers of consumers (62%) opting to shop online in the past 18 months (see figure below). Yet, despite this boom in digital commerce, the checkout process remains a significant source of friction for customers.

Speaker: Blackberry, OSS Consultants, & Revenera
Software is complex, which makes threats to the software supply chain more real every day. 64% of organizations have been impacted by a software supply chain attack and 60% of data breaches are due to unpatched software vulnerabilities. In the U.S. alone, cyber losses totaled $10.3 billion in 2022. All of these stats beg the question, “Do you know what’s in your software?

Bleeping Computer
NOVEMBER 2, 2021
A growing number of Mac and Macbook owners report that their devices become unbootable after attempting to update to the latest version of macOS, codenamed 'Monterey.' [.].

Malwarebytes
NOVEMBER 2, 2021
What browser do you use? There’s a good chance—roughly one in seven—that it’s Google Chrome. And even if you prefer a different browser, there’s a good chance that you’re using something that’s based on Google Chrome, such as Edge, Vivaldi, Chromium, Brave, or Opera. After a decade and and a half of relatively healthy competition between vendors, the World Wide Web is trending towards a browser monoculture.
Bleeping Computer
NOVEMBER 2, 2021
A critical unauthenticated, remote code execution GitLab flaw fixed on April 14, 2021, remains exploitable, with over 50% of deployments remaining unpatched. [.].

Cisco Security
NOVEMBER 2, 2021
When we look at our strategic initiatives across Cisco, nothing says “customer-driven,” like what we are doing to support each customer’s unique cloud strategy. Cloud isn’t something we are pushing; it is from listening to customers and their business needs. But this journey, which has been accelerated in response to the global pandemic, is unique for each organization.

Speaker: Erika R. Bales, Esq.
When we talk about “compliance and security," most companies want to ensure that steps are being taken to protect what they value most – people, data, real or personal property, intellectual property, digital assets, or any other number of other things - and it’s more important than ever that safeguards are in place. Let’s step back and focus on the idea that no matter how complicated the compliance and security regime, it should be able to be distilled down to a checklist.
Let's personalize your content