Patch ‘Em or Weep: Study Reveals Most Vulnerable IoT, Connected Assets
Tech Republic Security
SEPTEMBER 7, 2023
Phones, tablets and workstations with unpatched CVEs are a clear and present danger. New Armis study lists the most vulnerable.
Tech Republic Security
SEPTEMBER 7, 2023
Phones, tablets and workstations with unpatched CVEs are a clear and present danger. New Armis study lists the most vulnerable.

WIRED Threat Level
SEPTEMBER 7, 2023
And the first case on the docket may well be Russia’s cyberattacks against civilian critical infrastructure in Ukraine.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

Graham Cluley
SEPTEMBER 7, 2023
A Texas court has heard how last month a gang of men used a Raspberry Pi device to steal thousands of dollars from ATMs. Read more in my article on the Tripwire State of Security blog.
The Hacker News
SEPTEMBER 7, 2023
Microsoft on Wednesday revealed that a China-based threat actor known as Storm-0558 acquired the inactive consumer signing key to forge tokens and access Outlook by compromising an engineer’s corporate account. This enabled the adversary to access a debugging environment that contained information pertaining to a crash of the consumer signing system and steal the key.

Speaker: Erroll Amacker
Automation is transforming finance but without strong financial oversight it can introduce more risk than reward. From missed discrepancies to strained vendor relationships, accounts payable automation needs a human touch to deliver lasting value. This session is your playbook to get automation right. We’ll explore how to balance speed with control, boost decision-making through human-machine collaboration, and unlock ROI with fewer errors, stronger fraud prevention, and smoother operations.

Bleeping Computer
SEPTEMBER 7, 2023
Citizen Lab says two zero-days fixed by Apple today in emergency security updates were actively abused as part of a zero-click exploit chain (dubbed BLASTPASS) to deploy NSO Group's Pegasus commercial spyware onto fully patched iPhones. [.
The Hacker News
SEPTEMBER 7, 2023
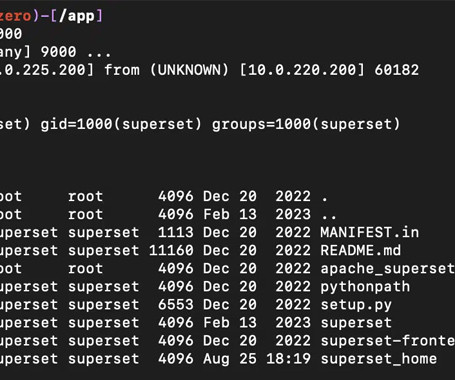
Patches have been released to address two new security vulnerabilities in Apache Superset that could be exploited by an attacker to gain remote code execution on affected systems. The update (version 2.1.1) plugs CVE-2023-39265 and CVE-2023-37941, which make it possible to conduct nefarious actions once a bad actor is able to gain control of Superset’s metadata database.
Cyber Security Informer brings together the best content for cyber security professionals from the widest variety of industry thought leaders.
The Hacker News
SEPTEMBER 7, 2023
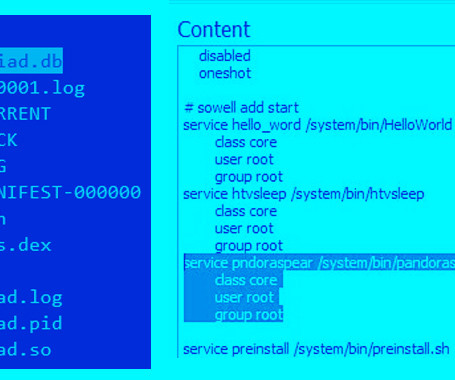
A Mirai botnet variant called Pandora has been observed infiltrating inexpensive Android-based TV sets and TV boxes and using them as part of a botnet to perform distributed denial-of-service (DDoS) attacks. Doctor Web said the compromises are likely to occur either during malicious firmware updates or when applications for viewing pirated video content are installed.
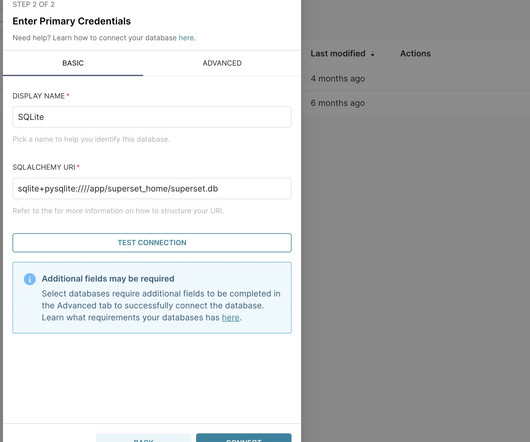
Security Affairs
SEPTEMBER 7, 2023
A couple of security vulnerabilities in Apache SuperSet could be exploited by an attacker to gain remote code execution on vulnerable systems. Apache Superset is an open-source Data Visualization and Data Exploration Platform, it is written in Python and based on the Flask web framework. Version 2.1.1 addressed two vulnerabilities, respectively tracked as CVE-2023-39265 and CVE-2023-37941 , that could be exploited to take control of Superset’s metadata database.
The Hacker News
SEPTEMBER 7, 2023
A new malvertising campaign has been observed distributing an updated version of a macOS stealer malware called Atomic Stealer (or AMOS), indicating that it’s being actively maintained by its author. An off-the-shelf Golang malware available for $1,000 per month, Atomic Stealer first came to light in April 2023.

Malwarebytes
SEPTEMBER 7, 2023
An investigation by Microsoft has finally revealed how China-based hackers circumvented the protections of a "highly isolated and restricted production environment" in May 2023 to unlock sensitive email accounts belonging to US government agencies. The attack was first reported by Microsoft in July , in an article that left some important questions unanswered.

Advertisement
Many cybersecurity awareness platforms offer massive content libraries, yet they fail to enhance employees’ cyber resilience. Without structured, engaging, and personalized training, employees struggle to retain and apply key cybersecurity principles. Phished.io explains why organizations should focus on interactive, scenario-based learning rather than overwhelming employees with excessive content.

The Hacker News
SEPTEMBER 7, 2023
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) on Thursday warned that multiple nation-state actors are exploiting security flaws in Fortinet FortiOS SSL-VPN and Zoho ManageEngine ServiceDesk Plus to gain unauthorized access and establish persistence on compromised systems.

Security Affairs
SEPTEMBER 7, 2023
Citizen Lab reported that the actively exploited zero-days fixed by Apple are being used in Pegasus spyware attacks Researchers at Citizen Lab reported that the actively exploited zero-day flaws (CVE-2023-41064 and CVE-2023-41061) fixed by Apple are being used to infect devices with NSO Group ’s Pegasus spyware. According to the researchers, the two vulnerabilities were chained as part of a zero-click exploit, named BLASTPASS, used in attacks on iPhones running the latest version of iOS (16.6).

WIRED Threat Level
SEPTEMBER 7, 2023
Here's how to request that your personal information not be used to train Meta's AI model. "Request" is the operative word here.
Security Affairs
SEPTEMBER 7, 2023
Researchers spotted a new malvertising campaign targeting Mac users with a new version of the macOS stealer Atomic Stealer. Malwarebytes researchers have observed a new malvertising campaign distributing an updated version of the popular Atomic Stealer (AMOS) for Mac. The Atomic Stealer first appeared in the threat landscape in April 2023. In April Cyble Research and Intelligence Labs (CRIL) discovered a Telegram channel advertising a new information-stealing malware, named Atomic macOS Stealer

Advertisement
The DHS compliance audit clock is ticking on Zero Trust. Government agencies can no longer ignore or delay their Zero Trust initiatives. During this virtual panel discussion—featuring Kelly Fuller Gordon, Founder and CEO of RisX, Chris Wild, Zero Trust subject matter expert at Zermount, Inc., and Principal of Cybersecurity Practice at Eliassen Group, Trey Gannon—you’ll gain a detailed understanding of the Federal Zero Trust mandate, its requirements, milestones, and deadlines.

Dark Reading
SEPTEMBER 7, 2023
Researchers at Citizen Lab recommend immediately updating any iPhones and iPads to the latest OSes.

Webroot
SEPTEMBER 7, 2023
When it comes to keeping sensitive data safe, email encryption is a necessity. But it doesn’t have to be a necessary evil. Too many employees and IT experts have experienced the pain of trying to use a needlessly complicated email encryption solution. There’s the endless steps, the hard-to-navigate portals, and the time-consuming processes that add up to a frustrating experience for most.

The Hacker News
SEPTEMBER 7, 2023
By the end of 2024, the number of MSPs and MSSPs offering vCISO services is expected to grow by almost 5 fold, as can be seen in figure 1. This incredible surge reflects the growing business demand for specialized cybersecurity expertise and the lucrative opportunities for MSPs and MSSPs in vCISO services.

Webroot
SEPTEMBER 7, 2023
Cybercrime is on the rise. The number of ransomware attacks has increased by 18% , while the worldwide volume of phishing attacks doubled to 500 million in 2022. Depending on the size of the business, one-third to two-thirds of businesses suffer malware attacks in any given year. And those attacks are costing companies a lot of money. In 2022, American businesses lost $10.3 billion to data breaches and cybercrime.

Speaker: Sierre Lindgren
Fraud is a battle that every organization must face – it’s no longer a question of “if” but “when.” Every organization is a potential target for fraud, and the finance department is often the bullseye. From cleverly disguised emails to fraudulent payment requests, the tactics of cybercriminals are advancing rapidly. Drawing insights from real-world cases and industry expertise, we’ll explore the vulnerabilities in your processes and how to fortify them effectively.

eSecurity Planet
SEPTEMBER 7, 2023
Much like the rest of technology, merger and acquisition (M&A) activity for cybersecurity companies has been in a slump this year. There are a number of reasons why that won’t last, but still, the decline has been noteworthy. For the first seven months of this year, there were a mere 34 startups that got acquired, according to data from Crunchbase.

Heimadal Security
SEPTEMBER 7, 2023
ASUS routers have come under the spotlight due to three critical remote code execution vulnerabilities. These vulnerabilities pose a significant threat, with all three receiving a CVSS v3.1 score of 9.8 out of 10.0. They can be exploited remotely and without authentication, potentially leading to remote code execution, service interruptions, and unauthorized operations on the […] The post Vulnerabilities Uncovered: Critical Remote Code Execution Risks in ASUS Routers appeared first on Heim

Bleeping Computer
SEPTEMBER 7, 2023
Google announced today that it is bringing additional security to the Google Chrome standard Safe Browsing feature by enabling real-time phishing protection for all users. [.

Dark Reading
SEPTEMBER 7, 2023
Putting the top 10 generative AI tools to the ethical test reveals more about humanity than artificial intelligence.

Advertisement
Keeper Security is transforming cybersecurity for people and organizations around the world. Keeper’s affordable and easy-to-use solutions are built on a foundation of zero-trust and zero-knowledge security to protect every user on every device. Our next-generation privileged access management solution deploys in minutes and seamlessly integrates with any tech stack to prevent breaches, reduce help desk costs and ensure compliance.

WIRED Threat Level
SEPTEMBER 7, 2023
Authorities have sanctioned 11 alleged members of the cybercriminal groups, while the US Justice Department unsealed three federal indictments against nine people accused of being members.

Bleeping Computer
SEPTEMBER 7, 2023
State-backed hacking groups have breached a U.S. aeronautical organization using exploits targeting critical Zoho and Fortinet vulnerabilities, a joint advisory published by CISA, the FBI, and the United States Cyber Command (USCYBERCOM) revealed on Thursday. [.

Dark Reading
SEPTEMBER 7, 2023
Securities and Exchange Commission rules elevate cybersecurity to a critical strategic concern and compel businesses to prioritize cyber resilience.

Anton on Security
SEPTEMBER 7, 2023
Detection Engineering is Painful — and It Shouldn’t Be (Part 1) This blog series was written jointly with Amine Besson, Principal Cyber Engineer, Behemoth CyberDefence and one more anonymous collaborator. This post is our first installment in the “Threats into Detections — The DNA of Detection Engineering” series, where we explore opportunities and shortcomings in the brand new world of Detection Engineering.

Advertisement
Many software teams have migrated their testing and production workloads to the cloud, yet development environments often remain tied to outdated local setups, limiting efficiency and growth. This is where Coder comes in. In our 101 Coder webinar, you’ll explore how cloud-based development environments can unlock new levels of productivity. Discover how to transition from local setups to a secure, cloud-powered ecosystem with ease.

SecureWorld News
SEPTEMBER 7, 2023
"Preparing for a Post-Quantum World" is the topic of a panel presentation at SecureWorld Denver on September 19, and with good reason. Quantum computing poses a potential threat to current cybersecurity practices, which are based on encryption algorithms that can be broken by quantum computers. Quantum computing uses the principles of quantum mechanics to perform calculations that are exponentially faster than what is possible with traditional computers.

Heimadal Security
SEPTEMBER 7, 2023
Minneapolis Public Schools (MPS) recently disclosed the full extent of a data breach from earlier this year, affecting more than 105,000 individuals. The breach, initially attributed to the Medusa ransomware group, compromised a wide range of personal information. The Breach and Investigation The incident, which began on February 6, 2023, and lasted until at least […] The post Minneapolis School District Reveals Full Extent of Data Breach appeared first on Heimdal Security Blog.

SecureWorld News
SEPTEMBER 7, 2023
The digital age has brought unprecedented opportunities and profound challenges in an increasingly interconnected world, particularly privacy and data protection. As institutions and corporations store vast amounts of personal information, incidents of data breaches and privacy violations have spurred a legal response that often takes the form of class-action lawsuits.

Dark Reading
SEPTEMBER 7, 2023
China's Storm-0558 accessed user emails at some 25 enterprise organizations earlier this year using forged tokens.

Advertisement
After a year of sporadic hiring and uncertain investment areas, tech leaders are scrambling to figure out what’s next. This whitepaper reveals how tech leaders are hiring and investing for the future. Download today to learn more!
Let's personalize your content