New 0-Day Attacks Linked to China’s ‘Volt Typhoon’
Krebs on Security
AUGUST 27, 2024
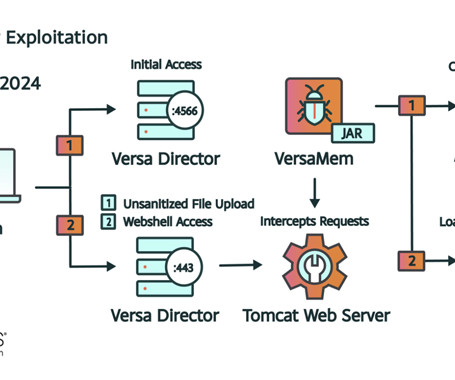
Malicious hackers are exploiting a zero-day vulnerability in Versa Director , a software product used by many Internet and IT service providers. Researchers believe the activity is linked to Volt Typhoon , a Chinese cyber espionage group focused on infiltrating critical U.S. networks and laying the groundwork for the ability to disrupt communications between the United States and Asia during any future armed conflict with China.









































Let's personalize your content