China Hacked Japan’s Military Networks
Schneier on Security
AUGUST 14, 2023
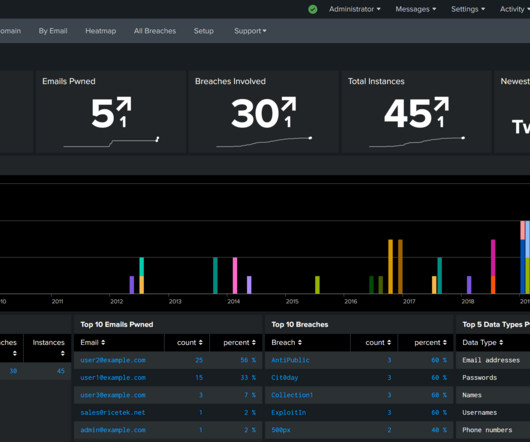
The NSA discovered the intrusion in 2020—we don’t know how—and alerted the Japanese. The Washington Post has the story : The hackers had deep, persistent access and appeared to be after anything they could get their hands on—plans, capabilities, assessments of military shortcomings, according to three former senior U.S. officials, who were among a dozen current and former U.S. and Japanese officials interviewed, who spoke on the condition of anonymity because of the matte


































Let's personalize your content