Generative AI: Rewards, Risks and New EU Legislation
Lohrman on Security
MAY 14, 2023
Depending on who you talk with or what stories you read, Open AI and ChatGPT may be the greatest things in the world — or the beginning of the end for humanity.

Lohrman on Security
MAY 14, 2023
Depending on who you talk with or what stories you read, Open AI and ChatGPT may be the greatest things in the world — or the beginning of the end for humanity.

Schneier on Security
MAY 14, 2023
This is a current list of where and when I am scheduled to speak: I’m speaking at IT-S Now 2023 in Vienna, Austria, on June 2, 2023 at 8:30 AM CEST. The list is maintained on this page.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

Bleeping Computer
MAY 14, 2023
Hackers are actively exploiting a recently fixed vulnerability in the WordPress Advanced Custom Fields plugin roughly 24 hours after a proof-of-concept (PoC) exploit was made public. [.

Trend Micro
MAY 14, 2023
Water Orthrus has been active recently with two new campaigns. CopperStealth uses a rootkit to install malware on infected systems, while CopperPhish steals credit card information. This blog will provide the structure of the campaign and how they work.

Advertisement
How many people would you trust with your house keys? Chances are, you have a handful of trusted friends and family members who have an emergency copy, but you definitely wouldn’t hand those out too freely. You have stuff that’s worth protecting—and the more people that have access to your belongings, the higher the odds that something will go missing.

CyberSecurity Insiders
MAY 14, 2023
The rise of cloud computing has provided individuals and businesses with a convenient way to store and access their data. However, with this convenience comes a concern about data security. Cloud storage services have become a target for hackers, and the theft of personal and sensitive information can have serious consequences. So, how is information stored in the cloud secured from hacks?
Security Affairs
MAY 14, 2023
FortiGuard Labs Researchers spotted new samples of the RapperBot botnet that support cryptojacking capabilities. FortiGuard Labs researchers have discovered new samples of the RapperBot bot that added cryptojacking capabilities. Researchers from FortiGuard Labs first discovered the previously undetected RapperBot IoT botnet in August, and reported that it is active since mid-June 2022.
Cyber Security Informer brings together the best content for cyber security professionals from the widest variety of industry thought leaders.

Security Affairs
MAY 14, 2023
A new round of the weekly SecurityAffairs newsletter arrived! Every week the best security articles from Security Affairs are free for you in your email box. We are in the final ! Please vote for Security Affairs ( [link] ) as the best European Cybersecurity Blogger Awards 2022 – VOTE FOR YOUR WINNERS Vote for me in the sections where is reported Securityaffairs or my name Pierluigi Paganini Please nominate Security Affairs as your favorite blog.

The Hacker News
MAY 14, 2023
A former employee of Ubiquiti has been sentenced to six years in jail after he pleaded guilty to posing as an anonymous hacker and a whistleblower in an attempt to extort almost $2 million worth of cryptocurrency while working at the company.

Security Affairs
MAY 14, 2023
UK outsourcing giant Capita is informing customers that their data may have been stolen in the cyberattack that hit the company in early April. In early April, the UK outsourcing giant Capita confirmed that its staff was locked out of their accounts on Friday after a cyber incident. Capita is one of the government’s biggest suppliers, with £6.5bn of public sector contracts, reported The Guardian.
WIRED Threat Level
MAY 14, 2023
A government effort to collect people’s internet records is moving beyond its test phase, but many details remain hidden from public view.

Advertiser: Revenera
In a recent study, IDC found that 64% of organizations said they were already using open source in software development with a further 25% planning to in the next year. Most organizations are unaware of just how much open-source code is used and underestimate their dependency on it. As enterprises grow the use of open-source software, they face a new challenge: understanding the scope of open-source software that's being used throughout the organization and the corresponding exposure.

Identity IQ
MAY 14, 2023
What Do I Do If My Social Security Card is Stolen? IdentityIQ When your Social Security card is stolen, it can be a major cause for concern. The primary concern with a stolen Social Security card is identity theft. With just your Social Security number, identity thieves can wreak havoc in your name, negatively impacting your credit, finances and even commit crimes in your name.

Heimadal Security
MAY 14, 2023
A remote code execution (RCE) attack consists of adversaries remotely running code on an enterprise`s assets. Threat actors remotely inject and execute code in the victim`s device or system by using local (LAN), or wide area networks (WAN). The code can access servers or software, open backdoors, compromise data, deploy ransomware, etc. Threat actors use […] The post What Is a Remote Code Execution Attack?

Security Boulevard
MAY 14, 2023
In today’s interconnected world, operational technology (OT) systems play a crucial role in industries such as manufacturing, energy, and transportation. However, with increased connectivity comes the risk of cyber threats targeting these critical infrastructures. To effectively safeguard OT systems, organizations must employ robust security measures, including threat intelligence.
WIRED Threat Level
MAY 14, 2023
The two-factor authentication tool got some serious upgrades that can help you bolster security for your online accounts.

Advertisement
Within the past few years, ransomware attacks have turned to critical infrastructure, healthcare, and government entities. Attackers have taken advantage of the rapid shift to remote work and new technologies. Add to that hacktivism due to global conflicts and U.S. elections, and an increased focus on AI, and you have the perfect recipe for a knotty and turbulent 2024.

Security Boulevard
MAY 14, 2023
In this episode we discuss a recent Twitter security incident that caused private tweets sent to Twitter Circles to become visible to unintended recipients. Next, we discuss the collaboration between Apple and Google to develop a specification for detecting and alerting users of unauthorized tracking using devices like AirTags. Finally, we explore the US government’s […] The post Private Tweets Exposed, Unauthorized Tracking Collaboration, AI Risks and Regulation appeared first on Shared Securit
Spinone
MAY 14, 2023
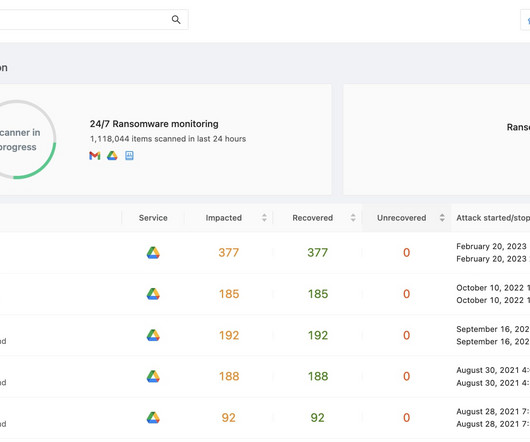
Ransomware is one of the biggest cyber threats to companies of any size. It has been evolving with computer technologies and even developed capabilities to infect SaaS collaboration tools like Google Workspace and Microsoft 365. Luckily, cybersecurity professionals came up with various methods of detecting and stopping ransomware in the cloud. In this article, we’ll […] The post Types of AI Ransomware Detection in SaaS Collaboration Tools first appeared on SpinOne.

Security Boulevard
MAY 14, 2023
Our thanks to USENIX for publishing their Presenter’s outstanding USENIX Enigma ’23 Conference content on the organization’s’ YouTube channel. Permalink The post USENIX Enigma 2023 – Kelly Shortridge – ‘The Very Hungry Defender: Metamorphosing Security Decision-Making By Incorporating Opportunity Cost’ appeared first on Security Boulevard.

Hacker's King
MAY 14, 2023
Cybersecurity has become an increasingly important field in today’s digital world. With businesses and individuals relying heavily on technology to store and process sensitive information, there is a growing need for cybersecurity professionals to protect these systems from cyber-attacks and data breaches. Many people are drawn to the cybersecurity field because of the high salaries and the potential for passive income.

Advertisement
The healthcare industry has massively adopted web tracking tools, including pixels and trackers. Tracking tools on user-authenticated and unauthenticated web pages can access personal health information (PHI) such as IP addresses, medical record numbers, home and email addresses, appointment dates, or other info provided by users on pages and thus can violate HIPAA Rules that govern the Use of Online Tracking Technologies by HIPAA Covered Entities and Business Associates.

SecureWorld News
MAY 14, 2023
WordPress is the undisputed champion in the area of content management systems (CMS), and for good reason. It boasts unparalleled flexibility and ease of use while supporting a slew of themes and plugins that extend various aspects of your website's functionality. Plus, it is readily available to anyone on an open-source basis. Unsurprisingly, this CMS is used by 43% of all sites in existence.

CyberSecurity Insiders
MAY 14, 2023
In January of this year, the UK police disclosed that some schools in Ghana were teaching school kids above the age of 10 to catfish single women from Britain and engage in romance scams with them, exploiting them for money exchange. The issue was brought to light when a team of journalists from a reputed daily engaged in an undercover operation to unravel the people behind catfishing.
Let's personalize your content