Splunk Urges Australian Organisations to Secure LLMs
Tech Republic Security
SEPTEMBER 30, 2024
Prompt injection and data leakage are among the top threats posed by LLMs, but they can be mitigated using existing security logging technologies.

Tech Republic Security
SEPTEMBER 30, 2024
Prompt injection and data leakage are among the top threats posed by LLMs, but they can be mitigated using existing security logging technologies.
Penetration Testing
SEPTEMBER 30, 2024
A serious vulnerability, dubbed KartLANPwn (CVE-2024-45200), has been identified in the wildly popular Nintendo game Mario Kart 8 Deluxe, putting millions of players at risk of remote code execution (RCE)... The post KartLANPwn (CVE-2024-45200) Exploits Mario Kart 8 Deluxe LAN Play Feature for RCE appeared first on Cybersecurity News.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

Tech Republic Security
SEPTEMBER 30, 2024
Discover the best VoIP routers for businesses in 2024. Easily compare range, transfer rates, connectivity types, price, and more.

Security Affairs
SEPTEMBER 30, 2024
The Department of Justice charged a British national for hacking into the systems of five U.S. organizations. The Department of Justice charged the British national Robert Westbrook (39) for hacking into the systems of five U.S. companies. Westbrook was arrested in the United Kingdom this week with is awaiting extradition to the United States. “Robert Westbrook, 39, of London, United Kingdom, was arrested in the United Kingdom this week with a view towards extradition to the United States

Speaker: Erroll Amacker
Automation is transforming finance but without strong financial oversight it can introduce more risk than reward. From missed discrepancies to strained vendor relationships, accounts payable automation needs a human touch to deliver lasting value. This session is your playbook to get automation right. We’ll explore how to balance speed with control, boost decision-making through human-machine collaboration, and unlock ROI with fewer errors, stronger fraud prevention, and smoother operations.
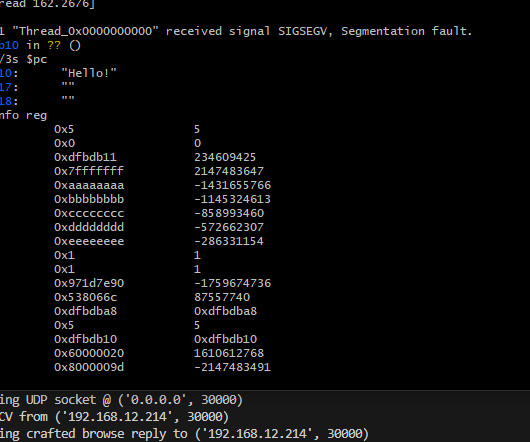
Penetration Testing
SEPTEMBER 30, 2024
A newly discovered critical vulnerability, CVE-2024-36435, has been uncovered in several Supermicro enterprise products, potentially exposing organizations to significant security risks. Discovered by Alexander Tereshkin from NVIDIA’s Offensive Security Research... The post Researcher Details RCE Flaw (CVE-2024-36435) in Supermicro BMC IPMI Firmware appeared first on Cybersecurity News.

Security Affairs
SEPTEMBER 30, 2024
Community Clinic of Maui experienced a data breach impacting over 120,000 people following a LockBit ransomware attack. In May, the Community Clinic of Maui experienced a major IT outage that impacted thousands of patients following a cyber attack. In June, the Lockbit ransomware gang took credit for the attack. LockBit breached the Community Healthcare Clinic of Maui as they are still rebuilding from the devastating fire last year.
Cyber Security Informer brings together the best content for cyber security professionals from the widest variety of industry thought leaders.

Security Boulevard
SEPTEMBER 30, 2024
Understand the overarching value of PAM, the use cases, the types of systems and how users will benefit from it, including proper contingency plans. The post The Path of Least Resistance to Privileged Access Management appeared first on Security Boulevard.
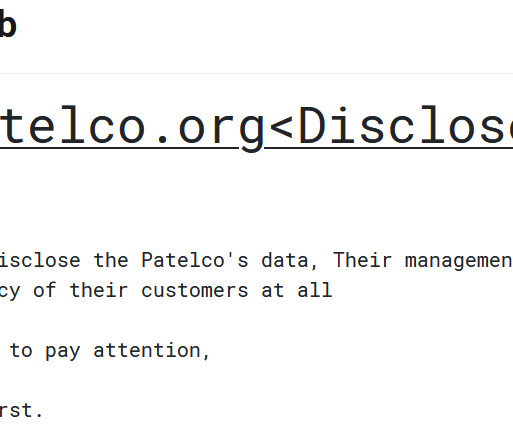
Security Affairs
SEPTEMBER 30, 2024
The ransomware attack on Patelco Credit Union this summer led to a data breach affecting over 1 million individuals, revealed the company. Patelco Credit Union is a member-owned, not-for-profit credit union that serves Northern California, particularly the San Francisco Bay Area. Founded in 1936, it is one of the oldest and largest credit unions in the country.

Security Boulevard
SEPTEMBER 30, 2024
Connected cars considered crud: Kia promises bug never exploited. But even 10-year-old cars were vulnerable. The post Kia’s Huge Security Hole: FIXED (Finally) appeared first on Security Boulevard.

The Hacker News
SEPTEMBER 30, 2024
Imagine a sophisticated cyberattack cripples your organization’s most critical productivity and collaboration tool — the platform you rely on for daily operations. In the blink of an eye, hackers encrypt your emails, files, and crucial business data stored in Microsoft 365, holding it hostage using ransomware.

Advertisement
Many cybersecurity awareness platforms offer massive content libraries, yet they fail to enhance employees’ cyber resilience. Without structured, engaging, and personalized training, employees struggle to retain and apply key cybersecurity principles. Phished.io explains why organizations should focus on interactive, scenario-based learning rather than overwhelming employees with excessive content.
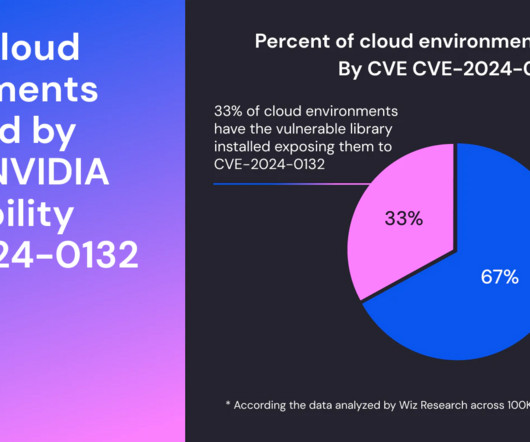
Security Affairs
SEPTEMBER 30, 2024
A critical vulnerability in the NVIDIA Container Toolkit could allow a container to escape and gain full access to the underlying host. Critical vulnerability CVE-2024-0132 (CVSS score 9.0) in the NVIDIA Container Toolkit could allow an attacker to escape the container and gain full access to the underlying host. The vulnerability is a Time-of-check Time-of-Use (TOCTOU) issue that impacts NVIDIA Container Toolkit 1.16.1 or earlier. “NVIDIA Container Toolkit 1.16.1 or earlier contains a Tim

The Hacker News
SEPTEMBER 30, 2024
The U.S. Department of Justice (DoJ) has charged a 39-year-old U.K. national for perpetrating a hack-to-trade fraud scheme that netted him nearly $3.75 million in illegal profits. Robert Westbrook of London was arrested last week and is expected to be extradited to the U.S. to face charges related to securities fraud, wire fraud, and five counts of computer fraud.

WIRED Threat Level
SEPTEMBER 30, 2024
Scamming operations that once originated in Southeast Asia are now proliferating around the world, likely raking in billions of dollars in the process.

The Hacker News
SEPTEMBER 30, 2024
Critical security vulnerabilities have been disclosed in six different Automatic Tank Gauge (ATG) systems from five manufacturers that could expose them to remote attacks.

Advertisement
The DHS compliance audit clock is ticking on Zero Trust. Government agencies can no longer ignore or delay their Zero Trust initiatives. During this virtual panel discussion—featuring Kelly Fuller Gordon, Founder and CEO of RisX, Chris Wild, Zero Trust subject matter expert at Zermount, Inc., and Principal of Cybersecurity Practice at Eliassen Group, Trey Gannon—you’ll gain a detailed understanding of the Federal Zero Trust mandate, its requirements, milestones, and deadlines.

Security Boulevard
SEPTEMBER 30, 2024
After putting its controversial AI-based Recall feature on hold in June, Microsoft rearchitected many of its features to address the security and privacy concerns that users and experts raised and will release it for the upcoming Windows Copilot+ PCs. The post Microsoft Readies a More Secure Recall Feature for Release appeared first on Security Boulevard.
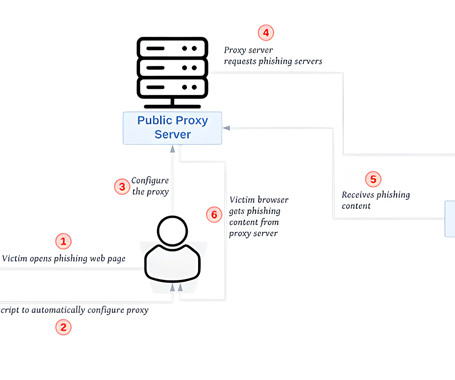
The Hacker News
SEPTEMBER 30, 2024
More than 140,000 phishing websites have been found linked to a phishing-as-a-service (PhaaS) platform named Sniper Dz over the past year, indicating that it's being used by a large number of cybercriminals to conduct credential theft.

Security Boulevard
SEPTEMBER 30, 2024
The financially motivated Storm-0501 threat group is attacking hybrid cloud environments in the United States by compromising on-prem systems first and moving laterally into the cloud, stealing data and credentials and dropping the Embargo ransomware along the way, Microsoft says. The post Storm-0501 Gang Targets US Hybrid Clouds with Ransomware appeared first on Security Boulevard.

Penetration Testing
SEPTEMBER 30, 2024
As the League of Legends (LoL) World Championship captivates fans worldwide, cybercriminals are seizing the opportunity to distribute malicious software. Bitdefender Labs has uncovered a sophisticated campaign targeting LoL enthusiasts... The post League of Legends Fans Targeted: Beware the Lumma Stealer Lurking in Fake Ads! appeared first on Cybersecurity News.

Speaker: Sierre Lindgren
Fraud is a battle that every organization must face – it’s no longer a question of “if” but “when.” Every organization is a potential target for fraud, and the finance department is often the bullseye. From cleverly disguised emails to fraudulent payment requests, the tactics of cybercriminals are advancing rapidly. Drawing insights from real-world cases and industry expertise, we’ll explore the vulnerabilities in your processes and how to fortify them effectively.

SecureWorld News
SEPTEMBER 30, 2024
Microsoft's Threat Intelligence team has uncovered a new ransomware threat actor, Storm-050, targeting various critical sectors in the U.S., including government, manufacturing, transportation, and law enforcement. The group is now expanding its operations by targeting U.S. hospitals, which raises serious concerns for both public safety and cybersecurity.

Penetration Testing
SEPTEMBER 30, 2024
The Taiwan Computer Emergency Response Team (TWCERT/CC) has released a series of security advisories highlighting critical vulnerabilities affecting various PLANET Technology switch models. These vulnerabilities range in severity, with potential... The post PLANET Technology Switches Face CVE-2024-8456 (CVSS 9.8), Urgent Firmware Updates Advised appeared first on Cybersecurity News.

The Hacker News
SEPTEMBER 30, 2024
Cybersecurity researchers have uncovered a new cryptojacking campaign targeting the Docker Engine API with the goal of co-opting the instances to join a malicious Docker Swarm controlled by the threat actor. This enabled the attackers to "use Docker Swarm's orchestration features for command-and-control (C2) purposes," Datadog researchers Matt Muir and Andy Giron said in an analysis.

Penetration Testing
SEPTEMBER 30, 2024
Human-operated ransomware represents a particularly insidious challenge, combining sophisticated techniques with manual execution to evade traditional security measures. A new report from the Japan Computer Emergency Response Team Coordination Center... The post Windows Event Logs: A Key to Unmasking Human-Operated Ransomware appeared first on Cybersecurity News.

Advertisement
Keeper Security is transforming cybersecurity for people and organizations around the world. Keeper’s affordable and easy-to-use solutions are built on a foundation of zero-trust and zero-knowledge security to protect every user on every device. Our next-generation privileged access management solution deploys in minutes and seamlessly integrates with any tech stack to prevent breaches, reduce help desk costs and ensure compliance.

The Hacker News
SEPTEMBER 30, 2024
Hold onto your hats, folks, because the cybersecurity world is anything but quiet! Last week, we dodged a bullet when we discovered vulnerabilities in CUPS that could've opened the door to remote attacks. Google's switch to Rust is paying off big time, slashing memory-related vulnerabilities in Android.

The Last Watchdog
SEPTEMBER 30, 2024
Cary, NC, Sept. 27, 2024, CyberNewswire — INE , a global leader in networking and cybersecurity training and certifications, is proud to announce they have earned 14 awards in G2’s Fall 2024 Report , including “Fastest Implementation” and “Most Implementable,” which highlight INE’s superior performance relative to competitors. “Best hands-on and real world scenario based curriculum,” raves small business user Satvik V. in a recent 5-star review. ”Their dedication towards improving the curr

Zero Day
SEPTEMBER 30, 2024
The iFixit Repair Business Toolkit got a refresh in 2023. I've been using the kit for over a year. Here's what I have inside the bag now.

Heimadal Security
SEPTEMBER 30, 2024
When it comes to threat detection, it’s important to get the right tools for the job. Unfortunately, that can be easier said than done. Whether it’s a SIEM, EDR, XDR, MDR, or any of a whole other range of confusing and overlapping terms – there are a lot of products on the market. EDR and […] The post EDR vs. SIEM: Key Differences, Features, Functionality Gaps, and More appeared first on Heimdal Security Blog.

Advertisement
Many software teams have migrated their testing and production workloads to the cloud, yet development environments often remain tied to outdated local setups, limiting efficiency and growth. This is where Coder comes in. In our 101 Coder webinar, you’ll explore how cloud-based development environments can unlock new levels of productivity. Discover how to transition from local setups to a secure, cloud-powered ecosystem with ease.

Zero Day
SEPTEMBER 30, 2024
After a lightning strike showered debris into my pool, the Beatbot Aquasense Pro pool cleaner tackled the mess with ease, proving its worth in extreme conditions.

Heimadal Security
SEPTEMBER 30, 2024
Patch management is stressful. In one of our Heimdal webinars, we ran a snap poll with sysadmins about how they find the patch management process. The results confirm what most of us already know: the vast majority (93%) have experienced stress around this issue. So, why is patch management such a source of grief for […] The post Zen and the Art of Modern Patch Management: How to Eliminate Stress, Improve Security, and Streamline IT Operations appeared first on Heimdal Security Blog.

Zero Day
SEPTEMBER 30, 2024
An Echo Pop is the perfect way to add a little pop of Alexa to your life this October Prime Day, pun intended.

Heimadal Security
SEPTEMBER 30, 2024
COPENHAGEN, Denmark, and Dubai, UAE, September 30, 2024 – Heimdal and emt Distribution announce a strategic partnership that combines Heimdal’s advanced cybersecurity solutions with emt Distribution’s deep market expertise. The collaboration will deliver sophisticated yet user friendly products to the Middle East. With Heimdal offering the widest cybersecurity stack in the world, and emt Distribution […] The post Heimdal and emt Distribution Aim to Dominate the Middle East Cybersecurity Ma

Advertisement
After a year of sporadic hiring and uncertain investment areas, tech leaders are scrambling to figure out what’s next. This whitepaper reveals how tech leaders are hiring and investing for the future. Download today to learn more!
Let's personalize your content