Microsoft Zero-Days Sold and then Used
Schneier on Security
JULY 29, 2022
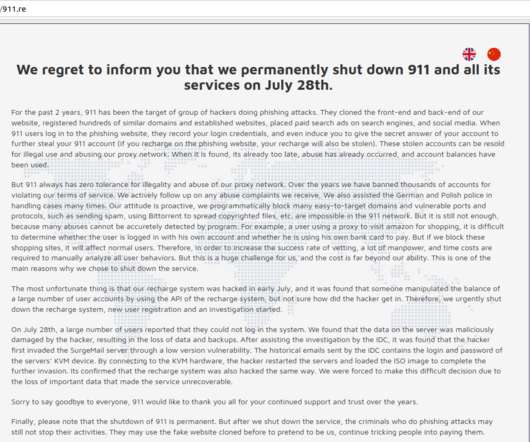
Yet another article about cyber-weapons arms manufacturers and their particular supply chain. This one is about Windows and Adobe Reader zero-day exploits sold by an Austrian company named DSIRF. There’s an entire industry devoted to undermining all of our security. It needs to be stopped.








































Let's personalize your content