Two U.S. Men Charged in 2022 Hacking of DEA Portal
Krebs on Security
MARCH 14, 2023
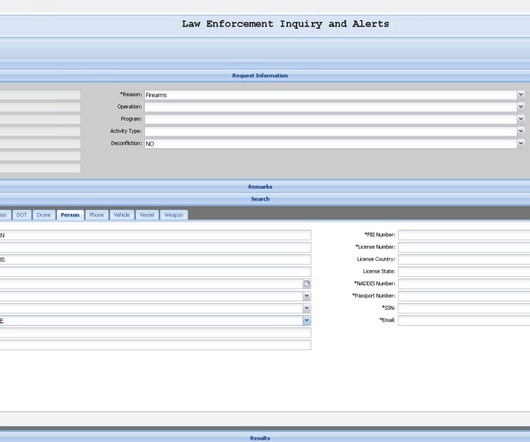
Two U.S. men have been charged with hacking into a U.S. Drug Enforcement Agency (DEA) online portal that taps into 16 different federal law enforcement databases. Both are alleged to be part of a larger criminal organization that specializes in using fake emergency data requests from compromised police and government email accounts to publicly threaten and extort their victims.
















Let's personalize your content