John Oliver on Data Brokers
Schneier on Security
APRIL 12, 2022
John Oliver has an excellent segment on data brokers and surveillance capitalism.

Schneier on Security
APRIL 12, 2022
John Oliver has an excellent segment on data brokers and surveillance capitalism.
Krebs on Security
APRIL 12, 2022
The U.S. Department of Justice (DOJ) said today it seized the website and user database for RaidForums , an extremely popular English-language cybercrime forum that sold access to more than 10 billion consumer records stolen in some of the world’s largest data breaches since 2015. The DOJ also charged the alleged administrator of RaidForums — 21-year-old Diogo Santos Coelho , of Portugal — with six criminal counts, including conspiracy, access device fraud and aggravated identi
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

Tech Republic Security
APRIL 12, 2022
Even among organizations rated highly for ransomware preparedness, many suffer a disruption to their operations in the wake of a ransomware attack, says Zerto. The post Report: Organizations are better prepared to fight ransomware, but gaps remain appeared first on TechRepublic.

Security Affairs
APRIL 12, 2022
The dark web marketplace RaidForums has been shut down and its infrastructure seized as a result of Operation TOURNIQUET. The illegal dark web marketplace RaidForums has been shut down and its infrastructure seized as a result of the international law enforcement Operation TOURNIQUET coordinated by Europol’s European Cybercrime Centre. Operation TOURNIQUET was conducted by law enforcement agencies from the United States, United Kingdom, Sweden, Portugal, and Romania.

Speaker: Erroll Amacker
Automation is transforming finance but without strong financial oversight it can introduce more risk than reward. From missed discrepancies to strained vendor relationships, accounts payable automation needs a human touch to deliver lasting value. This session is your playbook to get automation right. We’ll explore how to balance speed with control, boost decision-making through human-machine collaboration, and unlock ROI with fewer errors, stronger fraud prevention, and smoother operations.

Tech Republic Security
APRIL 12, 2022
Jack Wallen says these five password managers stand out as must-try in a very crowded field of players. The post 5 password managers built for teams appeared first on TechRepublic.

Malwarebytes
APRIL 12, 2022
Thanks to the Threat Intelligence team for their help with this article. Conti, the infamous ransomware created by a group of Russian and Eastern European cybercriminals, has again made headlines after a hacking group used its leaked source code to create another variant of the ransomware and target Russian businesses. The hacking group calls itself Network Battalion ’65 ( @xxNB65 ), and it is highly motivated by Russia’s invasion of Ukraine.
Cyber Security Informer brings together the best content for cyber security professionals from the widest variety of industry thought leaders.

We Live Security
APRIL 12, 2022
This ICS-capable malware targets a Ukrainian energy company. The post Industroyer2: Industroyer reloaded appeared first on WeLiveSecurity.

Tech Republic Security
APRIL 12, 2022
A key flaw nearly led to catastrophe for Fox, what can your organization learn from this leak? The post Fox configuration error leads to 13 million users’ data becoming public appeared first on TechRepublic.
Security Affairs
APRIL 12, 2022
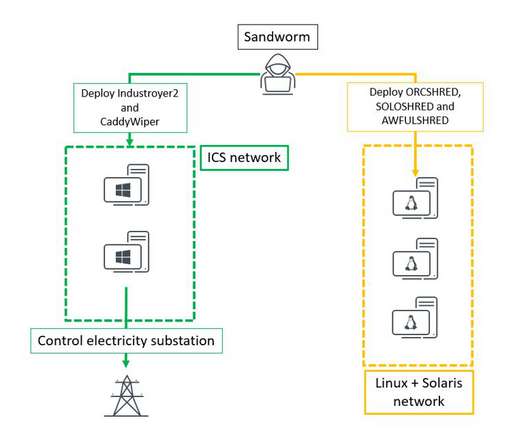
Russia-linked Sandworm APT group targeted energy facilities in Ukraine with INDUSTROYER2 and CADDYWIPER wipers. Russia-linked Sandworm threat actors targeted energy facilities in Ukraine with a new strain of the Industroyer ICS malware (INDUSTROYER2) and a new version of the CaddyWiper wiper. According to the CERT-UA, nation-state actors targeted high-voltage electrical substations with INDUSTROYER2, the variant analyzed by the researchers were customized to target respective substations.

Tech Republic Security
APRIL 12, 2022
If you're looking for a password manager that can be used for teams, there are plenty of options available. However, for Jack Wallen, these five stand out as must-try in a very crowded field of players. The post 5 password managers built for teams appeared first on TechRepublic.

Advertisement
Many cybersecurity awareness platforms offer massive content libraries, yet they fail to enhance employees’ cyber resilience. Without structured, engaging, and personalized training, employees struggle to retain and apply key cybersecurity principles. Phished.io explains why organizations should focus on interactive, scenario-based learning rather than overwhelming employees with excessive content.

CSO Magazine
APRIL 12, 2022
Almost all cloud users, roles, services, and resources grant excessive permissions leaving organizations vulnerable to attack expansion in the event of compromise, a new report from Palo Alto’s Unit 42 has revealed. The security vendor’s research discovered that misconfigured identity and access management (IAM) is opening the door to malicious actors that are targeting cloud infrastructure and credentials in attacks.

Dark Reading
APRIL 12, 2022
"Go patch your systems before" the exploit spreads more widely, ZDI warns.
The Hacker News
APRIL 12, 2022
Microsoft's Patch Tuesday updates for the month of April have addressed a total of 128 security vulnerabilities spanning across its software product portfolio, including Windows, Defender, Office, Exchange Server, Visual Studio, and Print Spooler, among others.

CyberSecurity Insiders
APRIL 12, 2022
United States government, in association with Europol, launched a secret operation named TOURNIQUET and as a part of this operation, it seized the IT infrastructure of the Raid-forums, a darknet website that sells and trades in stolen credentials from databases. News is out that a 14-year-old started RaidForums in 2015 and was arrested by the Europol in January this year.

Advertisement
The DHS compliance audit clock is ticking on Zero Trust. Government agencies can no longer ignore or delay their Zero Trust initiatives. During this virtual panel discussion—featuring Kelly Fuller Gordon, Founder and CEO of RisX, Chris Wild, Zero Trust subject matter expert at Zermount, Inc., and Principal of Cybersecurity Practice at Eliassen Group, Trey Gannon—you’ll gain a detailed understanding of the Federal Zero Trust mandate, its requirements, milestones, and deadlines.

The Hacker News
APRIL 12, 2022
The mass adoption of cloud infrastructure is fully justified by innumerable advantages. As a result, today, organizations' most sensitive business applications, workloads, and data are in the cloud. Hackers, good and bad, have noticed that trend and effectively evolved their attack techniques to match this new tantalizing target landscape.

SecureBlitz
APRIL 12, 2022
This post will show you how to secure your home construction site. According to the reports, job site theft is a widespread and rising problem that costs the construction sector more than $1 billion each year. However, the problem isn’t restricted to newly constructed homes; a home remodelling project is just as vulnerable. However, there. The post 6 Ways To Secure Your Home Construction Site appeared first on SecureBlitz Cybersecurity.

Heimadal Security
APRIL 12, 2022
Threat actors have been detected using the Spring4Shell vulnerability to install malware on victim PCs, according to security researchers. More Details on the Spring4Shell Vulnerability According to ZDNet, the Spring4Shell vulnerability, which has been assigned by security researchers CVE-2022-22965 is not considered to be as dangerous as the famous Log4Shell.

CSO Magazine
APRIL 12, 2022
Phishing definition. Phishing is a type of cyberattack that uses disguised email as a weapon. These attacks use social engineering techniques to trick the email recipient into believing that the message is something they want or need—a request from their bank, for instance, or a note from someone in their company—and to click a link or download an attachment.

Speaker: Sierre Lindgren
Fraud is a battle that every organization must face – it’s no longer a question of “if” but “when.” Every organization is a potential target for fraud, and the finance department is often the bullseye. From cleverly disguised emails to fraudulent payment requests, the tactics of cybercriminals are advancing rapidly. Drawing insights from real-world cases and industry expertise, we’ll explore the vulnerabilities in your processes and how to fortify them effectively.

CyberSecurity Insiders
APRIL 12, 2022
Ericsson, the Sweden-based Telecom Company that was involved in the 2019 money laundering case with a terrorist organization, seems to be serious about some of the internal documents being leaking to Swedish and international news outlets. According to a highly placed source the senior level management of the company is miffed with the reports claiming that the company was involved in channelizing money to the Islamic State (IS) Terrorist Group in Iraq making millions during suspicious transacti

IT Security Guru
APRIL 12, 2022
It’s unfortunate, but true: SaaS attacks continue to increase. You can’t get around it, COVID-19 accelerated the already exploding SaaS market and caused industries not planning on making a switch to embrace SaaS. With SaaS apps becoming the default system of record for organizations, it has left many struggling to secure their company’s SaaS estate.

Heimadal Security
APRIL 12, 2022
A major luxury menswear brand and one of the most known enterprises in Italy, the Ermenegildo Zegna Group, is comprised of the Ermenegildo Zegna and Zegna SpA companies. Zegna was founded by the young entrepreneur Ermenegildo Zegna, in Trivero, near the Biella Alps, in 1910 with a vision to ethically create the world’s finest textiles […].

Digital Shadows
APRIL 12, 2022
As the new year has reached the end of its first quarter, it’s time for us to go back and. The post Q1 2022 Ransomware Roundup first appeared on Digital Shadows.

Advertisement
Keeper Security is transforming cybersecurity for people and organizations around the world. Keeper’s affordable and easy-to-use solutions are built on a foundation of zero-trust and zero-knowledge security to protect every user on every device. Our next-generation privileged access management solution deploys in minutes and seamlessly integrates with any tech stack to prevent breaches, reduce help desk costs and ensure compliance.

Heimadal Security
APRIL 12, 2022
Fakecalls, an Android banking malware, has a powerful feature that allows it to hijack calls to a bank’s customer service number and connect the target directly with the malware’s operators. More on Fakecalls According to cybersecurity experts at Kaspersky, the Fakecalls malware first appeared last year and has been observed attacking users in South Korea, […].
Google Security
APRIL 12, 2022
Posted by Tom Hennen, Software Engineer, BCID & GOSST One of the great benefits of SLSA ( Supply-chain Levels for Software Artifacts ) is its flexibility. As an open source framework designed to improve the integrity of software packages and infrastructure, it is as applicable to small open source projects as to enterprise organizations. But with this flexibility can come a bewildering array of options for beginners—much like salsa dancing, someone just starting out might be left on the danc

Graham Cluley
APRIL 12, 2022
Same-day delivery firm CitySprint has warned couriers it has suffered a data breach that may have allowed hackers to access their sensitive personal data.

Naked Security
APRIL 12, 2022
Fortunately, we're not talking about a robot revolution, or about hospital AI run amuck. But these bugs could lead to ransomware, or worse.

Advertisement
Many software teams have migrated their testing and production workloads to the cloud, yet development environments often remain tied to outdated local setups, limiting efficiency and growth. This is where Coder comes in. In our 101 Coder webinar, you’ll explore how cloud-based development environments can unlock new levels of productivity. Discover how to transition from local setups to a secure, cloud-powered ecosystem with ease.

Dark Reading
APRIL 12, 2022
As the first step, make sure that all business-critical data across your organization is protected.

Heimadal Security
APRIL 12, 2022
During the April Patch Tuesday bout, Microsoft has released a total number of 26 fixes for common and less common vulnerabilities. Microsoft has also addressed five vulnerabilities that were labeled as important. Patch Tuesday April 2022 Roundup April’s Patch Tuesday has brought us numerous improvements and fixes for issues associated with Microsoft’s Chromium-based Edge browser. […].

Malwarebytes
APRIL 12, 2022
Dozens of apps were removed from the Google Play Store after they were found to be harvesting the data of device owners. The code in question—a software development kit (SDK)—was used inside apps which were downloaded over 10 million times. What happened? A wide range of Android apps were found to have this particular SDK lurking. There’s no obvious connection between the apps besides the SDK, as they’re all from different sources and developers.

CSO Magazine
APRIL 12, 2022
Rachel Wilson’s stellar security career has seen her hold several senior leadership positions at the National Security Agency (NSA) and become the first head of cybersecurity for Morgan Stanley Wealth Management and Investment Technology, where she now works to protect the organization’s systems and data and advises leadership on key cybersecurity issues.

Advertisement
After a year of sporadic hiring and uncertain investment areas, tech leaders are scrambling to figure out what’s next. This whitepaper reveals how tech leaders are hiring and investing for the future. Download today to learn more!
Let's personalize your content