Leaked Signing Keys Are Being Used to Sign Malware
Schneier on Security
DECEMBER 8, 2022
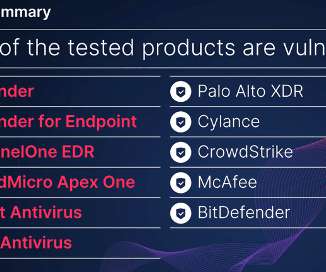
A bunch of Android OEM signing keys have been leaked or stolen, and they are actively being used to sign malware. Łukasz Siewierski, a member of Google’s Android Security Team, has a post on the Android Partner Vulnerability Initiative (AVPI) issue tracker detailing leaked platform certificate keys that are actively being used to sign malware.










































Let's personalize your content