Practical Ways Older Adults Can Manage Their Security Online
Lohrman on Security
JANUARY 31, 2021

Schneier on Security
JANUARY 26, 2021
I think this is the largest data breach of all time: 220 million people. ( Lots more stories are in Portuguese.).
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.
Daniel Miessler
JANUARY 25, 2021
There are recon tools, and there are recon tools. @tomnomnom —also called Tom Hudson—creates the latter. I have great respect for large, multi-use suites like Burp , Amass , and Spiderfoot , but I love tools with the Unix philosophy of doing one specific thing really well. I think this granular approach is especially useful in recon. Related Talk: Mechanizing the Methodology.

Joseph Steinberg
JANUARY 25, 2021
Long-time cybersecurity-industry veteran, Joseph Steinberg , has been appointed by CompTIA, the information technology (IT) industry’s nonprofit trade association that has issued more than 2-million vendor-neutral IT certifications to date, to its newly-formed Cybersecurity Advisory Council. The council, comprised of 16 experts with a diverse set of experience and backgrounds, will provide guidance on how technology companies can both address pressing cybersecurity issues and threats, as well as

Speaker: Erroll Amacker
Automation is transforming finance but without strong financial oversight it can introduce more risk than reward. From missed discrepancies to strained vendor relationships, accounts payable automation needs a human touch to deliver lasting value. This session is your playbook to get automation right. We’ll explore how to balance speed with control, boost decision-making through human-machine collaboration, and unlock ROI with fewer errors, stronger fraud prevention, and smoother operations.

Krebs on Security
JANUARY 7, 2021
The ongoing breach affecting thousands of organizations that relied on backdoored products by network software firm SolarWinds may have jeopardized the privacy of countless sealed court documents on file with the U.S. federal court system, according to a memo released Wednesday by the Administrative Office (AO) of the U.S. Courts. The judicial branch agency said it will be deploying more stringent controls for receiving and storing sensitive documents filed with the federal courts, following a d
Troy Hunt
JANUARY 1, 2021
It's a new year! With lots of breaches to discuss already ? Ok, so these may not be 2021 breaches but I betcha that by next week's update there'll be brand new ones from the new year to discuss. I managed to get enough connectivity in the middle of the Australian outback in front of Uluru to do the live stream this week, plus talk a bunch more about what we've been doing on our epic Australian journey.
Cyber Security Informer brings together the best content for cyber security professionals from the widest variety of industry thought leaders.

Schneier on Security
JANUARY 7, 2021
Researchers have been able to find all sorts of personal information within GPT-2. This information was part of the training data, and can be extracted with the right sorts of queries. Paper: “ Extracting Training Data from Large Language Models.” Abstract: It has become common to publish large (billion parameter) language models that have been trained on private datasets.

The Last Watchdog
JANUARY 25, 2021
SolarWinds and Mimecast are long-established, well-respected B2B suppliers of essential business software embedded far-and-wide in company networks. Related: Digital certificates destined to play key role in securing DX. Thanks to a couple of milestone hacks disclosed at the close of 2020 and start of 2021, they will forever be associated with putting supply-chain vulnerabilities on the map.

Joseph Steinberg
JANUARY 7, 2021
While much of the security-oriented focus regarding the storming of the Capitol building by protesters yesterday has rightfully been on the failure of the Capitol Police to prevent the breach of security, the country also faces a potentially serious cyber-threat as a result of the incident. Laptops, smartphones, printers, and other computing devices that were left behind in offices and other areas by elected officials, staffers, and others as they retreated from the advancing protesters all must
Krebs on Security
JANUARY 11, 2021
Ubiquiti , a major vendor of cloud-enabled Internet of Things (IoT) devices such as routers, network video recorders, security cameras and access control systems, is urging customers to change their passwords and enable multi-factor authentication. The company says an incident at a third-party cloud provider may have exposed customer account information and credentials used to remotely manage Ubiquiti gear.

Advertisement
Many cybersecurity awareness platforms offer massive content libraries, yet they fail to enhance employees’ cyber resilience. Without structured, engaging, and personalized training, employees struggle to retain and apply key cybersecurity principles. Phished.io explains why organizations should focus on interactive, scenario-based learning rather than overwhelming employees with excessive content.

Troy Hunt
JANUARY 28, 2021
Well, it kinda feels like we're back to the new normal that is 2021. I'm home, the kids are back at school and we're all still getting breached. We're breached so much that even when we're not breached but someone says we're breached, it genuinely looks like we're breached. Ok, that's a bit wordy but the Exodus thing earlier today was frustrating, not because a screen cap of an alleged breach notice was indistinguishable from a phish, but because of the way some people chose to react when I shar

Schneier on Security
JANUARY 4, 2021
From an interview with an Amazon Web Services security engineer: So when you use AWS, part of what you’re paying for is security. Right; it’s part of what we sell. Let’s say a prospective customer comes to AWS. They say, “I like pay-as-you-go pricing. Tell me more about that.” We say, “Okay, here’s how much you can use at peak capacity.

Adam Shostack
JANUARY 28, 2021
For Data Breach Today, I spoke with Anna Delaney about threat modeling for issues that are in the news right now: “Does your organization have a plan in place if one of your employees is accused via Twitter of being an insurrectionist? If your software was being used to spread plans for a riot, could you detect that? Threat modeling expert Adam Shostack discusses how companies should be prepared to respond to issues in the news.” Threat Modeling for Social Issues.

Advertisement
The DHS compliance audit clock is ticking on Zero Trust. Government agencies can no longer ignore or delay their Zero Trust initiatives. During this virtual panel discussion—featuring Kelly Fuller Gordon, Founder and CEO of RisX, Chris Wild, Zero Trust subject matter expert at Zermount, Inc., and Principal of Cybersecurity Practice at Eliassen Group, Trey Gannon—you’ll gain a detailed understanding of the Federal Zero Trust mandate, its requirements, milestones, and deadlines.

Joseph Steinberg
JANUARY 19, 2021
Last week, shortly before Amazon took the Parler social network offline by terminating the latter’s hosting services, a hacker allegedly facilitated a download of the social media site’s data. Many media outlets soon published stories effectively celebrating the hacker’s accomplishment – at least one outlet even referred to her as a “security researcher,” and another as a “benevolent hacker.
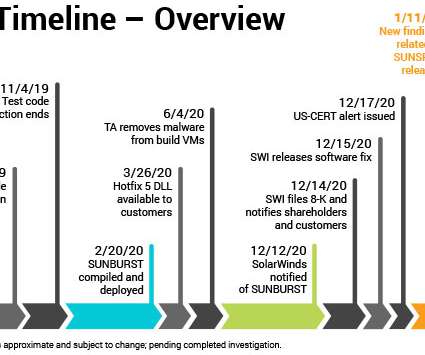
Krebs on Security
JANUARY 12, 2021
New research into the malware that set the stage for the megabreach at IT vendor SolarWinds shows the perpetrators spent months inside the company’s software development labs honing their attack before inserting malicious code into updates that SolarWinds then shipped to thousands of customers. More worrisome, the research suggests the insidious methods used by the intruders to subvert the company’s software development pipeline could be repurposed against many other major software p

Troy Hunt
JANUARY 25, 2021
I had this idea out of nowhere the other day that I should have a visual display somewhere in my office showing how many active Have I Been Pwned (HIBP) subscribers I presently have. Why? I'm not sure exactly, it just seemed like a good idea at the time. Perhaps in this era of remoteness I just wanted something a little more. present. More tangible than occasionally running a SQL query.

Advertisement
Keeper Security is transforming cybersecurity for people and organizations around the world. Keeper’s affordable and easy-to-use solutions are built on a foundation of zero-trust and zero-knowledge security to protect every user on every device. Our next-generation privileged access management solution deploys in minutes and seamlessly integrates with any tech stack to prevent breaches, reduce help desk costs and ensure compliance.

Schneier on Security
JANUARY 14, 2021
Security researcher Ahmed Hassan has shown that spoofing the Android’s “People Nearby” feature allows him to pinpoint the physical location of Telegram users: Using readily available software and a rooted Android device, he’s able to spoof the location his device reports to Telegram servers. By using just three different locations and measuring the corresponding distance reported by People Nearby, he is able to pinpoint a user’s precise location. […].

Tech Republic Security
JANUARY 29, 2021
By knowing the different types of data, it can help your company protect itself from breaches and better recover from a cyberattack.

Joseph Steinberg
JANUARY 28, 2021
Hands-free car-entry systems that allow people to unlock their car doors without the need to push any buttons on the fob or car provide great convenience; at least during the winter, many people even store key fobs in their coats and do not even physically handle the fobs on a regular basis. Cars that allow such access typically utilize proximity to determine when to let people open their doors; when a corresponding fob (and, ostensibly the car’s owner) is close to a locked vehicle that ve
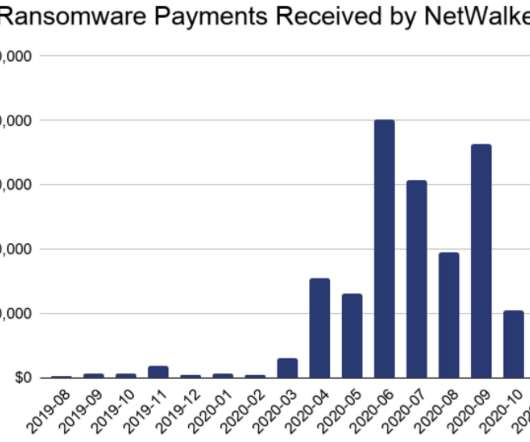
Krebs on Security
JANUARY 27, 2021
U.S. and Bulgarian authorities this week seized the darkweb site used by the NetWalker ransomware cybercrime group to publish data stolen from its victims. In connection with the seizure, a Canadian national suspected of extorting more than $27 million through the spreading of NetWalker was charged in a Florida court. The victim shaming site maintained by the NetWalker ransomware group, after being seized by authorities this week.

Advertisement
Many software teams have migrated their testing and production workloads to the cloud, yet development environments often remain tied to outdated local setups, limiting efficiency and growth. This is where Coder comes in. In our 101 Coder webinar, you’ll explore how cloud-based development environments can unlock new levels of productivity. Discover how to transition from local setups to a secure, cloud-powered ecosystem with ease.
Troy Hunt
JANUARY 9, 2021
And we're finally home. After 8,441km of driving finished off by a comfy flight home whilst the car catches a ride on a carrier, we're done. I talk about why we didn't finish the drive in the latter part of this week's video (basically boiled down to border uncertainties due to COVID outbreaks), but we still did all the big things we'd hoped for on this holiday.

Schneier on Security
JANUARY 4, 2021
The NSA has just declassified and released a redacted version of Military Cryptanalytics , Part III, by Lambros D. Callimahos, October 1977. Parts I and II, by Lambros D. Callimahos and William F. Friedman, were released decades ago — I believe repeatedly, in increasingly unredacted form — and published by the late Wayne Griswold Barker’s Agean Park Press.

Tech Republic Security
JANUARY 29, 2021
This comprehensive guide covers different types of denial of service attacks, DDoS protection strategies, as well as why it matters for business.

Advertisement
How many people would you trust with your house keys? Chances are, you have a handful of trusted friends and family members who have an emergency copy, but you definitely wouldn’t hand those out too freely. You have stuff that’s worth protecting—and the more people that have access to your belongings, the higher the odds that something will go missing.

Joseph Steinberg
JANUARY 12, 2021
In the context of cybersecurity, threat intelligence refers to information about hostile actors and/or the threats that they pose; cyber-defenders who arm themselves with such information can often dramatically improve their chances of preventing a breach. Of course, the concept of knowing your enemy is not knew – Sun Tzu speaks about its importance in The Art of War , written almost 2,500 years ago.

Krebs on Security
JANUARY 19, 2021
A hacker serving a 20-year sentence for stealing personal data on 1,300 U.S. military and government employees and giving it to an Islamic State hacker group in 2015 has been charged once again with fraud and identity theft. The new charges have derailed plans to deport him under compassionate release because of the COVID-19 pandemic. Ardit Ferizi , a 25-year-old citizen of Kosovo, was slated to be sent home earlier this month after a federal judge signed an order commuting his sentence to time

Troy Hunt
JANUARY 22, 2021
I'm back into a normal home routine and it's business as usual again. You know, stuff like data breaches, new tech toys and having your genitalia locked in an vulnerable IoT device and held for ransom. Just normal stuff like that ?? References Turing Tumble is a really neat game for kids (it's a "marble powered computer") I bought a LaMetric display (I'll probably plug that into an API to track HIBP subscriber signups) Imagine an IoT chastity belt. with a security vulnerability. that locks your

Speaker: Sierre Lindgren
Fraud is a battle that every organization must face – it’s no longer a question of “if” but “when.” Every organization is a potential target for fraud, and the finance department is often the bullseye. From cleverly disguised emails to fraudulent payment requests, the tactics of cybercriminals are advancing rapidly. Drawing insights from real-world cases and industry expertise, we’ll explore the vulnerabilities in your processes and how to fortify them effectively.
Let's personalize your content