How to Tell a Job Offer from an ID Theft Trap
Krebs on Security
MAY 21, 2021
One of the oldest scams around — the fake job interview that seeks only to harvest your personal and financial data — is on the rise, the FBI warns.
Krebs on Security
MAY 21, 2021
One of the oldest scams around — the fake job interview that seeks only to harvest your personal and financial data — is on the rise, the FBI warns.
Tech Republic Security
MAY 24, 2021
While many employers are tapping technologies to monitor workflows, a new report highlights potential drawbacks and even resentment among surveilled employees
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.
The Last Watchdog
MAY 20, 2021
One of the hottest topics at RSA Conference 2021 taking place virtually this week is the Secure Access Services Edge ( SASE ) security framework. Related: Cybersecurity experts react to Biden’s EO. SASE (pronounced sassy) essentially is a roadmap for infusing privacy and security deeply into the software coding that gives life to our smartphones, IoT devices and cloud infrastructure, i.e. at the “services edge,” where all the action is taking place.
Doctor Chaos
MAY 2, 2021
Cyber security compliance is more important than ever. With new technologies and digital connections happening every day, small and medium-sized businesses (SMBs) must properly comply with cyber security regulations across the board. Which ones, though, should you focus on the most?

Speaker: P. Andrew Sjogren, Sr. Product Marketing Manager at Very Good Security, Matt Doka, Co-Founder and CTO of Fivestars, and Steve Andrews, President & CEO of the Western Bankers Association
In this webinar, we have a great set of panelists who will take you through how Zero Data strategies can be used as part of a well-rounded compliance and security approach, and get you to market much sooner by also allowing for payment optimization. They’ll share how to grow your business faster and minimize costs for both security and compliance
The Hacker News
MAY 10, 2021
An unknown threat actor managed to control more than 27% of the entire Tor network exit capacity in early February 2021, a new study on the dark web infrastructure revealed.
Cyber Security Informer brings together the best content for cyber security professionals from the widest variety of industry thought leaders.
Krebs on Security
MAY 14, 2021
The DarkSide ransomware affiliate program responsible for the six-day outage at Colonial Pipeline this week that led to fuel shortages and price spikes across the country is running for the hills.
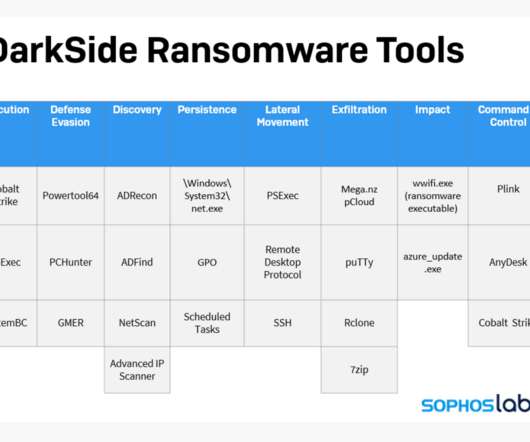
Adam Shostack
MAY 15, 2021
The Colonial Pipeline shutdown story is interesting in all sorts of ways, and I can’t delve into all of it. I did want to talk about one small aspect, which is the way responders talk about Darkside. Blog posts from Sophos and Mandiant seem really useful!

Lohrman on Security
MAY 23, 2021
Artificial intelligence is slowly transforming many areas of life — and fast — but we all need to pay attention. Reactions are all over the map, and AI will be used for both good and evil.
Troy Hunt
MAY 27, 2021
I've got 2 massive things to announce today that have been a long time in the works and by pure coincidence, have aligned such that I can share them together here today. One you would have been waiting for and one totally out of left field.

Speaker: Mike Cramer, Director of HIPAA & Data Security at The Word & Brown Companies
Now that companies are slowly allowing employees to return to work at the office, it's time to re-evaluate your company’s posture towards privacy and security. Join Mike Cramer, Director of HIPAA & Data Security at The Word & Brown Companies, for a discussion that will focus on compliance and the types of privacy and security measures your company should be aware of, as well as tips and methods for implementing these measures.
Adam Levin
MAY 14, 2021
Colonial Pipeline paid roughly $5 million to the ransomware group responsible for hacking its systems, contradicting earlier claims. . Bloomberg News reported that the company paid the ransom in cryptocurrency hours after the May 7 cyberattack that shut down the country’s largest fuel pipeline.
Schneier on Security
MAY 10, 2021
This is a newly unclassified NSA history of its reaction to academic cryptography in the 1970s: “ New Comes Out of the Closet: The Debate over Public Cryptography in the Inman Era ,” Cryptographic Quarterly , Spring 1996, author still classified.
Krebs on Security
MAY 11, 2021
The FBI confirmed this week that a relatively new ransomware group known as DarkSide is responsible for an attack that caused Colonial Pipeline to shut down 5,550 miles of pipe , stranding countless barrels of gasoline, diesel and jet fuel on the Gulf Coast.

The Last Watchdog
MAY 18, 2021
Keeping up with the pace of technology, information, and the evolving threat landscape is a challenge for all enterprises. Related: DHS launches 60-day cybersecurity sprints. To make matters more difficult, implementing new security software and processes to address these issues is another big hurdle, often causing disruption—and not the good kind.
Lohrman on Security
MAY 2, 2021
What is the future of passwords? More urgently, how are you doing with using (or reusing) passwords now? Here are some helpful tips ahead of World Password Day on May 6
Troy Hunt
MAY 18, 2021
Today I'm very happy to welcome the 16th government to Have I Been Pwned, Sweden.
Adam Levin
MAY 19, 2021
The credit reporting bureau Experian is facing a backlash for its recent failures to protect customer data. . An undergraduate student at Rochester Institute of Technology named Bill Demirkapi discovered the most recent security failure.
Schneier on Security
MAY 4, 2021
This is an impressive hack: Security researchers Ralf-Philipp Weinmann of Kunnamon, Inc.

The Last Watchdog
MAY 25, 2021
Resilience was the theme of RSA Conference 2021 which took place virtually last week. Related: Web attacks spike 62 percent in 2020. I’ve been covering this cybersecurity gathering since 2004 and each year cybersecurity materially advances. By the same token, the difficulties of defending modern IT systems has redoubled as organizations try to balance security and productivity. The outside pressures are indeed as daunting as ever.

Adam Shostack
MAY 6, 2021
Apple has released (or I’ve just come across) a document Device and Data Access when Personal Safety is At Risk. Apple makes it easy to connect and share your life with the people closest to you. What you share, and whom you share it with, is up to you — including the decision to make changes to better protect your information or personal safety.
Troy Hunt
MAY 24, 2021
Today I'm very happy to welcome the first Caribbean government to Have I Been Pwned, Trinidad & Tobago.
Lohrman on Security
MAY 30, 2021
The Department of Homeland Security is mandating that pipeline companies report cyber breaches to federal authorities within 12 hours of an incident, and the list of organizations who must do the same will likely grow
Krebs on Security
MAY 19, 2021
Many online services allow users to reset their passwords by clicking a link sent via SMS, and this unfortunately widespread practice has turned mobile phone numbers into de facto identity documents.

The Last Watchdog
MAY 12, 2021
A permissions glut is giving rise to an explosion of new exposures in modern business networks. Related: Securing digital identities. Companies are adopting multi-cloud and hybrid cloud infrastructures and relying on wide-open app development like never before. In doing so, permissions to make myriad software connections are proliferating. Taken together these man-to-machine and machine-to-machine connections result in cool new digital services.

Anton on Security
MAY 27, 2021
A SOC Tried To Detect Threats in the Cloud … Your Won’t Believe What Happened Next Now, we all agree that various cloud technologies such as SaaS SIEM help your Security Operations Center (SOC). However, there’s also a need to talk about how traditional SOCs are challenged by the need to monitor cloud computing environments for threats. In this post, I wanted to quickly touch on this very topic and refresh some past analysis of this (and perhaps reminisce on how sad things were in 2012 ).
Troy Hunt
MAY 28, 2021
This week is the culmination of planning that began all the way back in August last year when I announced the intention to start open sourcing the HIBP code base. Today, it's finally happened with Pwned Passwords now completely open to all.
Lohrman on Security
MAY 16, 2021
America finally woke up to the reality that we have a ransomware emergency worthy of real attention. How did events unfold and what will happen next?
Schneier on Security
MAY 28, 2021
Russia’s Sunburst cyberespionage campaign , discovered late last year, impacted more than 100 large companies and US federal agencies, including the Treasury, Energy, Justice, and Homeland Security departments.
Krebs on Security
MAY 5, 2021
Phishers targeting Microsoft Office 365 users increasingly are turning to specialized links that take users to their organization’s own email login page.

The Last Watchdog
MAY 17, 2021
A greater good has come from Capital One’s public pillaging over losing credit application records for 100 million bank customers. Related: How credential stuffing fuels account takeovers.
Adam Shostack
MAY 20, 2021
Threat model Thursday is not just back, but live again! This week is my Using Threat Modeling to Improve Compliance at RSAC 2021. The video replay is available if you have an RSA pass, and the slides are available to all. Threat Model Thursdays threat modeling
Troy Hunt
MAY 8, 2021
A fairly hectic week this one, in a large part due to chasing down really flakey network issues that are causing devices (namely Shelly relays) to be inaccessible. I suspect it's ARP related and as of now, it's still not fully resolved.
Lohrman on Security
MAY 9, 2021
The Biden administration has proposed a bold new infrastructure plan that includes road, bridges, airports, broadband, people and more. What’s in the plan — and what’s next
Let's personalize your content