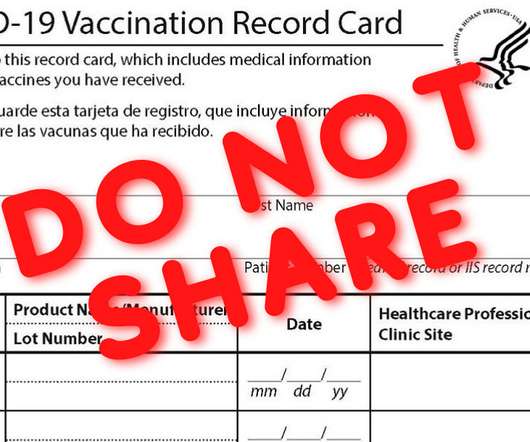
Do Not Post Your COVID-19 Vaccination Card On Social Media
Joseph Steinberg
FEBRUARY 11, 2021
It seems like every day that I see social media posts in which people share photos of the official COVID-19 vaccine card that they have received after being vaccinated against the novel coronavirus that has inflicted tremendous suffering worldwide over the past year.





 262
262 





Let's personalize your content