Why Should You Merge Physical Security and Cybersecurity?
Lohrman on Security
SEPTEMBER 5, 2021
For more than a decade there have been calls to merge physical and cybersecurity in global organizations. Is this the right time? What are the benefits?

Lohrman on Security
SEPTEMBER 5, 2021
For more than a decade there have been calls to merge physical and cybersecurity in global organizations. Is this the right time? What are the benefits?

Troy Hunt
SEPTEMBER 6, 2021
For the last few years, I've been welcome national governments to Have I Been Pwned (HIBP) and granting them full and free access to domain-level searches via a dedicated API. Today, I'm very happy to welcome the Czech Republic's National Cyber and Information Security Agency who can now query their government domains along with the 26 other nations that have come before them.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

Krebs on Security
SEPTEMBER 8, 2021
Microsoft Corp. warns that attackers are exploiting a previously unknown vulnerability in Windows 10 and many Windows Server versions to seize control over PCs when users open a malicious document or visit a booby-trapped website. There is currently no official patch for the flaw, but Microsoft has released recommendations for mitigating the threat.

Schneier on Security
SEPTEMBER 7, 2021
Normal-looking cables (USB-C, Lightning, and so on) that exfiltrate data over a wireless network. I blogged about a previous prototype here.

Speaker: Erroll Amacker
Automation is transforming finance but without strong financial oversight it can introduce more risk than reward. From missed discrepancies to strained vendor relationships, accounts payable automation needs a human touch to deliver lasting value. This session is your playbook to get automation right. We’ll explore how to balance speed with control, boost decision-making through human-machine collaboration, and unlock ROI with fewer errors, stronger fraud prevention, and smoother operations.

Tech Republic Security
SEPTEMBER 9, 2021
IT teams are experiencing employee pushback due to remote work policies and many feel like cybersecurity is a "thankless task" and that they're the "bad guys" for implementing these rules.

Troy Hunt
SEPTEMBER 10, 2021
An early one today as I made space in the schedule to get out on the water 😎 I'm really liking the new Apple AirTags, I'm disliking some of the international media coverage about Australia's COVID situation, another gov onto HIBP and a blog post I've wanted to write for a long time on biometrics. That last one in particularly I felt was really important as time and time again, I hear these irrational statements from people about the perceived "risks" of biomet
Cyber Security Informer brings together the best content for cyber security professionals from the widest variety of industry thought leaders.

Schneier on Security
SEPTEMBER 10, 2021
After being compelled by a Swiss court to monitor IP logs for a particular user, ProtonMail no longer claims that “we do not keep any IP logs.

Tech Republic Security
SEPTEMBER 9, 2021
Cyberattacks have surged during the coronavirus pandemic as criminals rake in bountiful ransomware payouts. Malicious office docs have been on the rise for months, per a new report.
Security Affairs
SEPTEMBER 9, 2021
The massive DDoS attack that has been targeting the internet giant Yandex was powered b a completely new botnet tracked as M?ris. The Russian Internet giant Yandex has been targeting by the largest DDoS attack in the history of Runet, the Russian Internet designed to be independent of the world wide web and ensure the resilience of the country to an internet shutdown.

Krebs on Security
SEPTEMBER 6, 2021
In May 2015, KrebsOnSecurity briefly profiled “ The Manipulaters ,” the name chosen by a prolific cybercrime group based in Pakistan that was very publicly selling spam tools and a range of services for crafting, hosting and deploying malicious email. Six years later, a review of the social media postings from this group shows they are prospering, while rather poorly hiding their activities behind a software development firm in Lahore that has secretly enabled an entire generation of

Advertisement
Many cybersecurity awareness platforms offer massive content libraries, yet they fail to enhance employees’ cyber resilience. Without structured, engaging, and personalized training, employees struggle to retain and apply key cybersecurity principles. Phished.io explains why organizations should focus on interactive, scenario-based learning rather than overwhelming employees with excessive content.

Schneier on Security
SEPTEMBER 9, 2021
We knew the basics of this story , but it’s good to have more detail. Here’s me in 2015 about this Juniper hack. Here’s me in 2007 on the NSA backdoor.

Tech Republic Security
SEPTEMBER 8, 2021
Only 33% of users surveyed by NordPass changed the default passwords on their IoT devices, leaving the rest susceptible to attack.

Trend Micro
SEPTEMBER 9, 2021
Microsoft has disclosed the existence of a new zero-day vulnerability that affects multiple versions of Windows. This vulnerability (designated as CVE-2021-40444) is currently delivered via malicious Office 365 documents and requires user input to open the file to trigger.

Bleeping Computer
SEPTEMBER 8, 2021
A threat actor has leaked a list of almost 500,000 Fortinet VPN login names and passwords that were allegedly scraped from exploitable devices last summer. [.].

Advertisement
The DHS compliance audit clock is ticking on Zero Trust. Government agencies can no longer ignore or delay their Zero Trust initiatives. During this virtual panel discussion—featuring Kelly Fuller Gordon, Founder and CEO of RisX, Chris Wild, Zero Trust subject matter expert at Zermount, Inc., and Principal of Cybersecurity Practice at Eliassen Group, Trey Gannon—you’ll gain a detailed understanding of the Federal Zero Trust mandate, its requirements, milestones, and deadlines.

Schneier on Security
SEPTEMBER 8, 2021
Isracard used a single cell phone to communicate with credit card clients, and receive documents via WhatsApp. An employee stole the phone. He reformatted the SIM, which was oddly the best possible outcome, given the circumstances. Using the data to steal money would have been much worse. Here’s a link to an archived version.

Tech Republic Security
SEPTEMBER 9, 2021
Some of these phrasings are standard day-to-day subject lines, but as one expert explained, "the attacker wants you to be moving too fast to stop and question if it's legitimate.

CSO Magazine
SEPTEMBER 7, 2021
COVID-19 has changed the face of security forever. The perimeter defense model, which had been slowly crumbling, has now been shattered. Employees are working from home, many of them permanently. Applications are shifting to the cloud at an accelerating pace. Enterprise security today is all about secure remote access and protecting cloud-based assets.

Graham Cluley
SEPTEMBER 7, 2021
The Ragnar Locker group, a gang of cybercriminals behind a series of costly ransomware attacks against companies, has warned victims that they should not seek the assistance of law enforcement agencies.

Advertisement
Keeper Security is transforming cybersecurity for people and organizations around the world. Keeper’s affordable and easy-to-use solutions are built on a foundation of zero-trust and zero-knowledge security to protect every user on every device. Our next-generation privileged access management solution deploys in minutes and seamlessly integrates with any tech stack to prevent breaches, reduce help desk costs and ensure compliance.

Schneier on Security
SEPTEMBER 6, 2021
Yet another article on the privacy risks of static MAC addresses and always-on Bluetooth connections. This one is about wireless headphones. The good news is that product vendors are fixing this: Several of the headphones which could be tracked over time are for sale in electronics stores, but according to two of the manufacturers NRK have spoken to, these models are being phased out. “The products in your line-up, Elite Active 65t, Elite 65e and Evolve 75e, will be going out of production
Tech Republic Security
SEPTEMBER 8, 2021
Supervised and unsupervised machine learning are good ways to detect threats. But what's the difference?
Cisco Security
SEPTEMBER 8, 2021
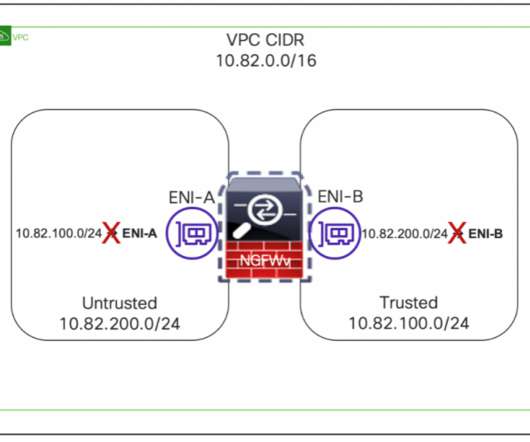
Cisco Secure Firewall provides industry-leading firewall capabilities for Amazon Virtual Private Cloud (VPC)and resources deployed inside. Customers use these firewalls to protect north-south and east-west traffic. Typically, we provide north-south traffic inspection in AWS infrastructure by deploying a load balancer and adding firewalls behind it. Another approach uses Amazon VPC Ingress Routing to steer traffic to Cisco Secure Firewalls.

Security Affairs
SEPTEMBER 10, 2021
Microsoft has fixed the Azurescape issue, a flaw in Azure Container Instances that allows to take over containers of other platform users. Microsoft has addressed a vulnerability in Azure Container Instances (ACI) called Azurescape that could have allowed a malicious container to take over containers belonging to other users. An attacker could exploit the vulnerability to execute commands in the containers of other users and access to their data.

Speaker: Sierre Lindgren
Fraud is a battle that every organization must face – it’s no longer a question of “if” but “when.” Every organization is a potential target for fraud, and the finance department is often the bullseye. From cleverly disguised emails to fraudulent payment requests, the tactics of cybercriminals are advancing rapidly. Drawing insights from real-world cases and industry expertise, we’ll explore the vulnerabilities in your processes and how to fortify them effectively.

The Hacker News
SEPTEMBER 4, 2021
The U.S. Cyber Command on Friday warned of ongoing mass exploitation attempts in the wild targeting a now-patched critical security vulnerability affecting Atlassian Confluence deployments that could be abused by unauthenticated attackers to take control of a vulnerable system.

Tech Republic Security
SEPTEMBER 8, 2021
Technology is not the only answer: An expert suggests improving the human cyber capacity of a company's workforce plus cybersecurity technology offers a better chance of being safe.

Bleeping Computer
SEPTEMBER 7, 2021
ug in the McDonald's Monopoly VIP game in the United Kingdom caused the login names and passwords for the game's database to be sent to all winners. [.].
Security Affairs
SEPTEMBER 6, 2021
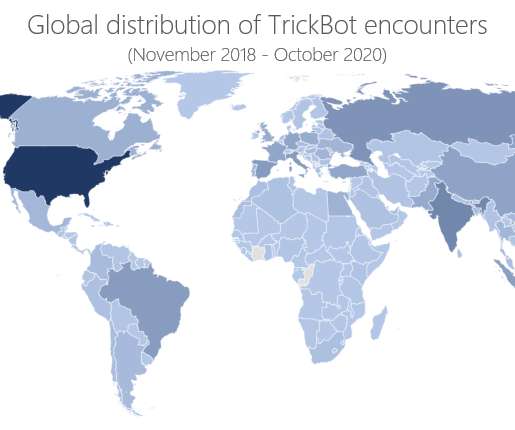
A Russian man accused of being a member of the infamous TrickBot gang was arrested while trying to leave South Korea. A Russian man accused of being a member of the TrickBot gang was arrested last week at the Seoul international airport. The man has remained stuck in the Asian country since February 2020 due to the COVID-19 lockdown imposed by the local government and the cancelation of international travel.

Advertisement
Many software teams have migrated their testing and production workloads to the cloud, yet development environments often remain tied to outdated local setups, limiting efficiency and growth. This is where Coder comes in. In our 101 Coder webinar, you’ll explore how cloud-based development environments can unlock new levels of productivity. Discover how to transition from local setups to a secure, cloud-powered ecosystem with ease.

We Live Security
SEPTEMBER 9, 2021
The university suffered a ransomware attack, however there is no evidence so far of data being accessed or stolen. The post Howard University suffers cyberattack, suspends online classes in aftermath appeared first on WeLiveSecurity.

Tech Republic Security
SEPTEMBER 8, 2021
Making predictions about data is the next frontier in terms of identifying risk in your infrastructure, expert says. But is it right for your organization?
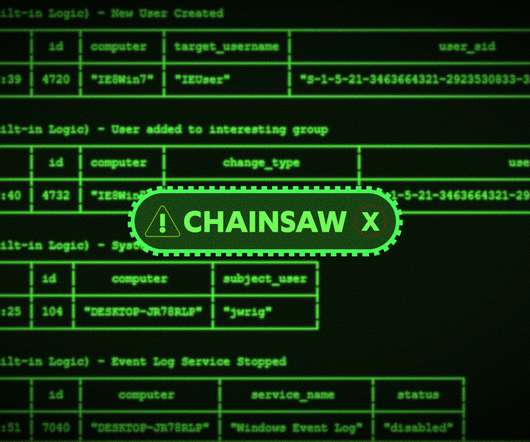
Bleeping Computer
SEPTEMBER 6, 2021
Incident responders and blue teams have a new tool called Chainsaw that speeds up searching through Windows event log records to identify threats. [.].
Security Affairs
SEPTEMBER 5, 2021
The Irish Data Protection Commission has fined WhatsApp €225 million over data sharing transparency for European Union users’ data with Facebook. The Irish Data Protection Commission has fined WhatsApp €225 million for the lack of transparency on how it shares European Union users’ data with Facebook companies. The instant messaging company violated the actual General Data Protection Regulation (GDPR). “The Data Protection Commission (DPC) has today announced a conclusion to a

Advertisement
After a year of sporadic hiring and uncertain investment areas, tech leaders are scrambling to figure out what’s next. This whitepaper reveals how tech leaders are hiring and investing for the future. Download today to learn more!
Let's personalize your content