How Coinbase Phishers Steal One-Time Passwords
Krebs on Security
OCTOBER 13, 2021
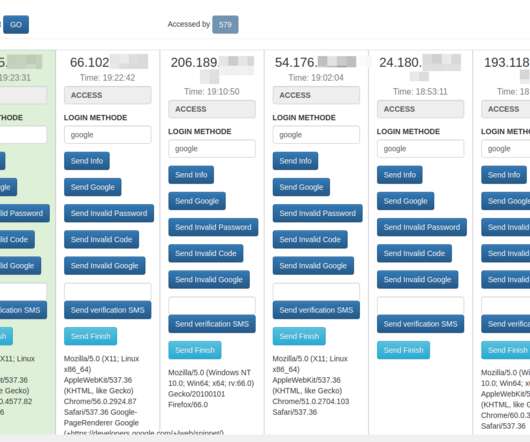
A recent phishing campaign targeting Coinbase users shows thieves are getting cleverer about phishing one-time passwords (OTPs) needed to complete the login process. It also shows that phishers are attempting to sign up for new Coinbase accounts by the millions as part of an effort to identify email addresses that are already associated with active accounts.










































Let's personalize your content