ChatGPT Privacy Flaw
Schneier on Security
MARCH 22, 2023
OpenAI has disabled ChatGPT’s privacy history, almost certainly because they had a security flaw where users were seeing each others’ histories.

Schneier on Security
MARCH 22, 2023
OpenAI has disabled ChatGPT’s privacy history, almost certainly because they had a security flaw where users were seeing each others’ histories.

Krebs on Security
MARCH 20, 2023
A new breach involving data from nine million AT&T customers is a fresh reminder that your mobile provider likely collects and shares a great deal of information about where you go and what you do with your mobile device — unless and until you affirmatively opt out of this data collection. Here’s a primer on why you might want to do that, and how.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

Tech Republic Security
MARCH 23, 2023
Microsoft has already seen millions of phishing emails sent every day by attackers using this phishing kit. Learn how to protect your business from this AitM campaign. The post Massive adversary-in-the-middle phishing campaign bypasses MFA and mimics Microsoft Office appeared first on TechRepublic.

Bleeping Computer
MARCH 24, 2023
Consumer goods giant Procter & Gamble has confirmed a data breach affecting an undisclosed number of employees after its GoAnywhere MFT secure file-sharing platform was compromised in early February. [.

Speaker: Speakers:
In today's digital age, having an untrained workforce can be a significant risk to your business. Cyber threats are evolving; without proper training, your employees could be the weakest link in your defense. This webinar empowers leaders like you with the tools and strategies needed to transform your employees into a robust frontline defense against cyber attacks.

Schneier on Security
MARCH 24, 2023
In case you don’t have enough to worry about, people are hiding explosives —actual ones—in USB sticks: In the port city of Guayaquil, journalist Lenin Artieda of the Ecuavisa private TV station received an envelope containing a pen drive which exploded when he inserted it into a computer, his employer said. Artieda sustained slight injuries to one hand and his face, said police official Xavier Chango.

CyberSecurity Insiders
MARCH 22, 2023
Cybercriminals are smarter, faster, and more relentless in their attacks than in times past. Data breaches are a serious threat to organizations, but vulnerability management automation can help reduce the number of incidents businesses face each year. Managing vulnerabilities is difficult in an increasingly connected cyber environment. Companies have their own networks, networks connected to their supply chains, vendor access, remote workers, and other entry points, all creating security gaps.
Cyber Security Informer brings together the best content for cyber security professionals from the widest variety of industry thought leaders.

Bleeping Computer
MARCH 23, 2023
The U.S. Cybersecurity & Infrastructure Security Agency (CISA) has released a new open-source incident response tool that helps detect signs of malicious activity in Microsoft cloud environments. [.

CSO Magazine
MARCH 20, 2023
The emergence of effective natural language processing tools such as ChatGPT means it's time to begin understanding how to harden against AI-enabled cyberattacks. The natural language generation capabilities of large language models (LLMs) are a natural fit for one of cybercrime’s most important attack vectors: phishing. Phishing relies on fooling people and the ability to generate effective language and other content at scale is a major tool in the hacker’s kit.

CyberSecurity Insiders
MARCH 19, 2023
After the release of ChatGPT in November 2022, the OpenAI CEO and the people behind the conversational chatbot launch say that they are equally scared of the negative consequences that the newly developed technology can fetch in the future. Sam Altman, the tech brain leading the company, now owned by Microsoft, spoke a few words about what the world was intending to say about the tech.

Tech Republic Security
MARCH 20, 2023
Learn how this cryptocurrency campaign operates and its scope. Then, get tips on protecting vulnerable Kubernetes instances from this cybersecurity threat. The post First Dero cryptojacking campaign targets unprotected Kubernetes instances appeared first on TechRepublic.

Advertisement
How many people would you trust with your house keys? Chances are, you have a handful of trusted friends and family members who have an emergency copy, but you definitely wouldn’t hand those out too freely. You have stuff that’s worth protecting—and the more people that have access to your belongings, the higher the odds that something will go missing.
Dark Reading
MARCH 24, 2023
In two days, ethical researchers from 10 countries have unearthed more than 22 zero-day bugs in a wide range of technologies at the annual hacking contest.

Bleeping Computer
MARCH 22, 2023
A new credit card stealing hacking campaign is doing things differently than we have seen in the past by hiding their malicious code inside the 'Authorize.net' payment gateway module for WooCommcerce, allowing the breach to evade detection by security scans. [.

CSO Magazine
MARCH 23, 2023
The US Cybersecurity and Infrastructure Security Agency (CISA) has issued advisories on 49 vulnerabilities in eight industrial control systems (ICS) this week, which are used across multiple critical infrastructure sectors. The vulnerabilities identified by CISA were tracked in products from ICS providers including Siemens, Hitachi, Rockwell, Delta Electronics, VISAM, and Keysight.
Tech Republic Security
MARCH 24, 2023
Addressing cybersecurity can be a challenge when the focus is on speed in software development and production life cycles. The post DevSecOps puts security in the software cycle appeared first on TechRepublic.

Advertiser: Revenera
In a recent study, IDC found that 64% of organizations said they were already using open source in software development with a further 25% planning to in the next year. Most organizations are unaware of just how much open-source code is used and underestimate their dependency on it. As enterprises grow the use of open-source software, they face a new challenge: understanding the scope of open-source software that's being used throughout the organization and the corresponding exposure.

Heimadal Security
MARCH 21, 2023
On March 20th, Ferrari announced they were victims of a cyberattack that could result in customers` data leakage. Threat actors claimed to have breached some of the Ferrari IT systems and sent a ransom demand. Ferrari N.V. announces that Ferrari S.p.A., its wholly-owned Italian subsidiary, was recently contacted by a threat actor with a ransom […] The post Ferrari Announces Data Breach.

Bleeping Computer
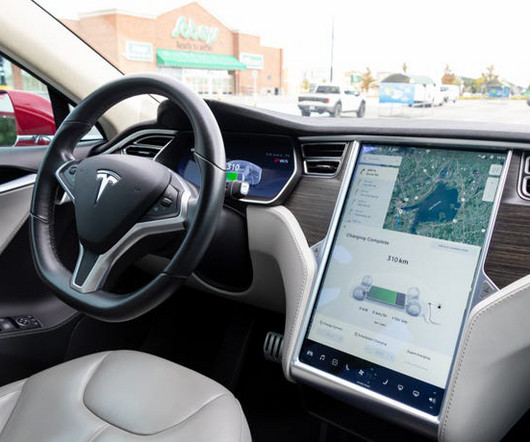
MARCH 22, 2023
On the first day of Pwn2Own Vancouver 2023, security researchers successfully demoed Tesla Model 3, Windows 11, and macOS zero-day exploits and exploit chains to win $375,000 and a Tesla Model 3. [.

Dark Reading
MARCH 24, 2023
GitHub hastens to replace its RSA SSH host key after an exposure mishap threatens users with man-in-the-middle attacks and organization impersonation.

Tech Republic Security
MARCH 21, 2023
The harassment reported by Palo Alto Networks Unit 42 typically takes the form of phone calls and emails directed toward employees, C-suite executives and even customers. The post Ransomware gangs’ harassment of victims is increasing appeared first on TechRepublic.

Advertisement
The healthcare industry has massively adopted web tracking tools, including pixels and trackers. Tracking tools on user-authenticated and unauthenticated web pages can access personal health information (PHI) such as IP addresses, medical record numbers, home and email addresses, appointment dates, or other info provided by users on pages and thus can violate HIPAA Rules that govern the Use of Online Tracking Technologies by HIPAA Covered Entities and Business Associates.

CyberSecurity Insiders
MARCH 22, 2023
Is your organization doing enough to protect its environment from hackers? In 2021, U.S. companies lost nearly $7 billion to phishing scams, malware, malvertising, and other cybercrimes. Experts estimate that by 2025, such schemes will cost businesses worldwide more than $10.5 trillion annually. Given those figures, it’s clear that companies can’t afford to ignore the threat hackers pose to their bottom line.

Security Boulevard
MARCH 23, 2023
It has been almost a year since Russia first invaded Ukraine, and the war has resulted in a massive rise in both physical and digital attacks. Since the invasion, Russian cyberattacks have skyrocketed and any country or business that has allied with Ukraine, or opposed the war, has become a target. As these attacks have. The post Using Deception to Learn About Russian Threat Actors appeared first on Security Boulevard.
Naked Security
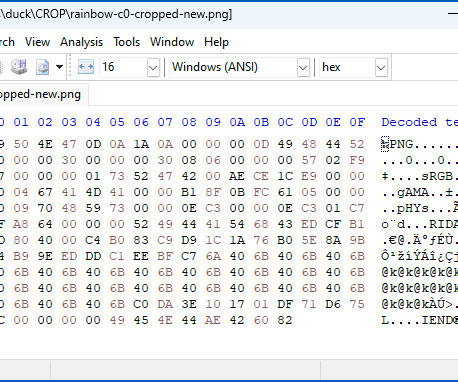
MARCH 22, 2023
Turns out that the Windows 11 Snipping Tool has the same "aCropalypse" data leakage bug as Pixel phones. Here's how to work around the problem.

Tech Republic Security
MARCH 20, 2023
A look at 4th quarter 2022, data suggests that new threat surfaces notwithstanding, low-code cybersecurity business email compromises including phishing, as well as MFA bombing are still the prevalent exploits favored by threat actors. The post BECs double in 2022, overtaking ransomware appeared first on TechRepublic.

Speaker: Blackberry, OSS Consultants, & Revenera
Software is complex, which makes threats to the software supply chain more real every day. 64% of organizations have been impacted by a software supply chain attack and 60% of data breaches are due to unpatched software vulnerabilities. In the U.S. alone, cyber losses totaled $10.3 billion in 2022. All of these stats beg the question, “Do you know what’s in your software?

CyberSecurity Insiders
MARCH 20, 2023
Google’s dedicated team of cybersecurity researchers from ‘Project Zero’ have found a flaw in Samsung Exynos Modems that can give unauthorized data access to hackers, without the knowledge of users. And it’s discovered that the vulnerability allows a cyber criminal to compromise a smart phone at the Internet-to-baseband remote code execution level, giving access to sensitive data such as contacts, messages and even photos.

Heimadal Security
MARCH 22, 2023
A new campaign is deploying variants of the ShellBot malware, specifically targeting poorly maintained Linux SSH servers. It seems the threat actors use scanner malware to find systems that have SSH port 22 open and proceed to install ShellBot on the servers that have weak credentials. ShellBot, also known as PerlBot, is a DDoS Bot […] The post ShellBot DDoS Malware Targets Poorly Managed Linux Servers appeared first on Heimdal Security Blog.

Bleeping Computer
MARCH 18, 2023
The Emotet malware is now distributed using Microsoft OneNote email attachments, aiming to bypass Microsoft security restrictions and infect more targets. [.
Tech Republic Security
MARCH 20, 2023
Learn about Microsoft's WordPress on Azure App Service, as well as an interesting alternative from WP Engine. The post Running WordPress on Azure for secure, fast and global content delivery appeared first on TechRepublic.

Advertisement
Within the past few years, ransomware attacks have turned to critical infrastructure, healthcare, and government entities. Attackers have taken advantage of the rapid shift to remote work and new technologies. Add to that hacktivism due to global conflicts and U.S. elections, and an increased focus on AI, and you have the perfect recipe for a knotty and turbulent 2024.

Security Through Education
MARCH 22, 2023
What does a government scam, an IT support scam and a romance scam have in common? They all use psychology and social engineering skills to convince their victims to take an action that is detrimental to them. It’s easy to think “I know better” or “that will never happen to me.” The truth is, being human is enough for anyone to fall victim to a scammer’s tactics.

CyberSecurity Insiders
MARCH 23, 2023
AT&T Alien Labs researchers have discovered a new variant of BlackGuard stealer in the wild, infecting using spear phishing attacks. The malware evolved since its previous variant and now arrives with new capabilities. Key takeaways: BlackGuard steals user sensitive information from a wide range of applications and browsers. The malware can hijack crypto wallets copied to clipboard.

Bleeping Computer
MARCH 22, 2023
A trojanized version of the legitimate ChatGPT extension for Chrome is gaining popularity on the Chrome Web Store, accumulating over 9,000 downloads while stealing Facebook accounts. [.

Tech Republic Security
MARCH 22, 2023
New report says far too many firms have too many IT assets they cannot see or aren’t using, with some Windows servers lacking endpoint protection and patch management. The post Report: Too many enterprises have shadow IT – unlocked doors with no cameras appeared first on TechRepublic.

Speaker: Erika R. Bales, Esq.
When we talk about “compliance and security," most companies want to ensure that steps are being taken to protect what they value most – people, data, real or personal property, intellectual property, digital assets, or any other number of other things - and it’s more important than ever that safeguards are in place. Let’s step back and focus on the idea that no matter how complicated the compliance and security regime, it should be able to be distilled down to a checklist.
Let's personalize your content