Account Hijacking Site OGUsers Hacked, Again
Krebs on Security
DECEMBER 2, 2020
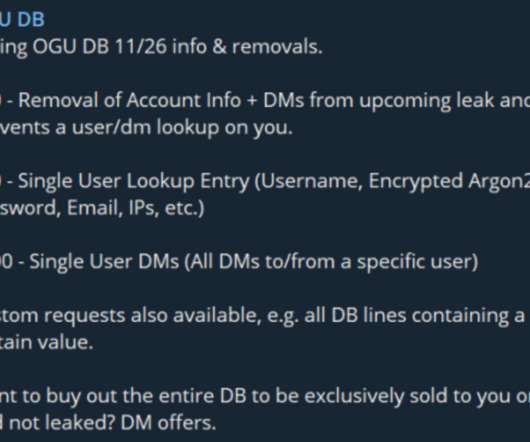
For at least the third time in its existence, OGUsers — a forum overrun with people looking to buy, sell and trade access to compromised social media accounts — has been hacked. An offer by the apparent hackers of OGUsers, offering to remove account information from the eventual database leak in exchange for payment. Roughly a week ago, the OGUsers homepage was defaced with a message stating the forum’s user database had been compromised.



































Let's personalize your content