How to safely access and navigate the Dark Web
Tech Republic Security
JULY 11, 2016
Is your business data on the Dark Web? Learn how to find out if you've been compromised in this step-by-step guide to accessing the underbelly of the internet.

Tech Republic Security
JULY 11, 2016
Is your business data on the Dark Web? Learn how to find out if you've been compromised in this step-by-step guide to accessing the underbelly of the internet.

Elie
JULY 11, 2016
Here are the 5 ways I bulletproof my credit cards against identity theft, and you can use them yourself very easily. As a bonus, at the end of the post I have added an experimental step to defend against the recent chip downgrading attack.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.
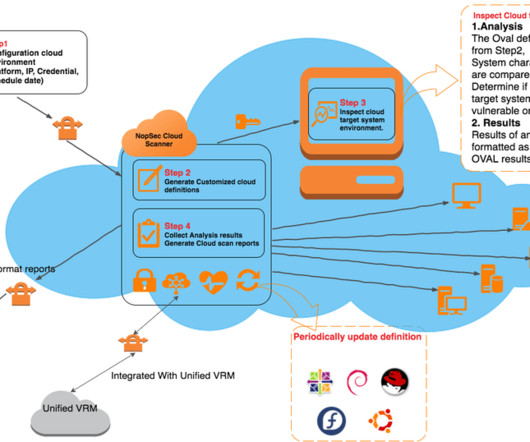
NopSec
JULY 13, 2016
Most organizations are currently migrating their computing infrastructure into the public cloud (AWS, Google, Azure) usually embracing a mixed private / public cloud model. Most SaaS solutions, including NopSec, already base their entire computing infrastructure on public clouds. This creates a unique challenge in terms of setting up proper vulnerability management processes to address the cloud environment’s peculiarities.

Kali Linux
JULY 10, 2016
The folks at Black Hat have been kind enough to invite us once again to deliver a Kali Dojo in Las Vegas this year. The event will be held on the 4th of August at the Mandalay Bay hotel, and will be open to all Black Hat pass types. This year our Dojo will be set up differently, allowing for a larger crowd and much more interaction. We are going to hold a full day event, featuring several main activity areas : Area 1: Customising Kali ISOs using live-build One to the most important aspects of Ka

Speaker: Erroll Amacker
Automation is transforming finance but without strong financial oversight it can introduce more risk than reward. From missed discrepancies to strained vendor relationships, accounts payable automation needs a human touch to deliver lasting value. This session is your playbook to get automation right. We’ll explore how to balance speed with control, boost decision-making through human-machine collaboration, and unlock ROI with fewer errors, stronger fraud prevention, and smoother operations.

Tech Republic Security
JULY 14, 2016
Microsoft recently won an appeal over a US search warrant that aimed to force the company to turn over data that was stored on foreign servers.

Privacy and Cybersecurity Law
JULY 13, 2016
The European Commission yesterday issued an adequacy decision adopting the EU-US Privacy Shield, which replaces Safe Harbor as a framework […].
Cyber Security Informer brings together the best content for cyber security professionals from the widest variety of industry thought leaders.

Tech Republic Security
JULY 13, 2016
Documentary filmmaker Yuval Orr interviewed cryptoanarchists, hackers, and security experts about why encryption and privacy are important. His new movie will make you see the Dark Web in a new light.

Tech Republic Security
JULY 12, 2016
Computer scientists enhance data security by simplifying the creation of truly random numbers used to build encryption keys.

Tech Republic Security
JULY 12, 2016
Analytics managers need to do two things to protect IoT-generated data from an often-overlooked threat.

Tech Republic Security
JULY 11, 2016
Privacy expert Susan Landau makes the case for keeping smartphones backdoor free, and for the FBI developing 21st century capabilities to conduct electronic surveillance.

Advertisement
Many cybersecurity awareness platforms offer massive content libraries, yet they fail to enhance employees’ cyber resilience. Without structured, engaging, and personalized training, employees struggle to retain and apply key cybersecurity principles. Phished.io explains why organizations should focus on interactive, scenario-based learning rather than overwhelming employees with excessive content.

Tech Republic Security
JULY 11, 2016
Malvertising is malware at its best, even catching security experts in its crosshairs. Learn how to fight back against these malware-infused ads.

Tech Republic Security
JULY 14, 2016
The UK government recently began a trial using blockchain technology to track the distribution of benefits, which has raised some privacy concerns.

Tech Republic Security
JULY 14, 2016
If you want to set up an in-house authentication system to use for ownCloud, WordPress, and the like, find out how to install privacyIDEA on your Ubuntu server.

Tech Republic Security
JULY 12, 2016
Gionee, a Chinese phone manufacturer, claims that its new smartphone uses an encrypted chip and could be the 'safest smartphone ever.

Advertisement
The DHS compliance audit clock is ticking on Zero Trust. Government agencies can no longer ignore or delay their Zero Trust initiatives. During this virtual panel discussion—featuring Kelly Fuller Gordon, Founder and CEO of RisX, Chris Wild, Zero Trust subject matter expert at Zermount, Inc., and Principal of Cybersecurity Practice at Eliassen Group, Trey Gannon—you’ll gain a detailed understanding of the Federal Zero Trust mandate, its requirements, milestones, and deadlines.

Tech Republic Security
JULY 11, 2016
At the 2016 Cisco Live event, the company announced new products to address network threats faster and help users more easily pinpoint advanced threats.

Tech Republic Security
JULY 11, 2016
Here's a quick tutorial on how to add a custom lock screen message to Mac devices running 10.7 to 10.11.

Tech Republic Security
JULY 11, 2016
The online black market is becoming a well-oiled and lucrative machine, thanks to the massive amount of stolen data flowing through the underground.

Tech Republic Security
JULY 14, 2016
Vulnerabilities are likely, even in the best software. Creating a bug bounty program is one way to find and fix them faster.

Advertisement
Keeper Security is transforming cybersecurity for people and organizations around the world. Keeper’s affordable and easy-to-use solutions are built on a foundation of zero-trust and zero-knowledge security to protect every user on every device. Our next-generation privileged access management solution deploys in minutes and seamlessly integrates with any tech stack to prevent breaches, reduce help desk costs and ensure compliance.

Tech Republic Security
JULY 14, 2016
Vulnerabilities are likely, even in the best software. Creating a bug bounty program is one way to find and fix them faster.

Tech Republic Security
JULY 13, 2016
Results of a recent Tech Pro Research survey suggest workers using unsupported mobile devices is a significant security risk.
Let's personalize your content