How to safely access and navigate the Dark Web
Tech Republic Security
JULY 11, 2016
Is your business data on the Dark Web? Learn how to find out if you've been compromised in this step-by-step guide to accessing the underbelly of the internet.

Tech Republic Security
JULY 11, 2016
Is your business data on the Dark Web? Learn how to find out if you've been compromised in this step-by-step guide to accessing the underbelly of the internet.

Elie
JULY 11, 2016
Here are the 5 ways I bulletproof my credit cards against identity theft, and you can use them yourself very easily. As a bonus, at the end of the post I have added an experimental step to defend against the recent chip downgrading attack.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.
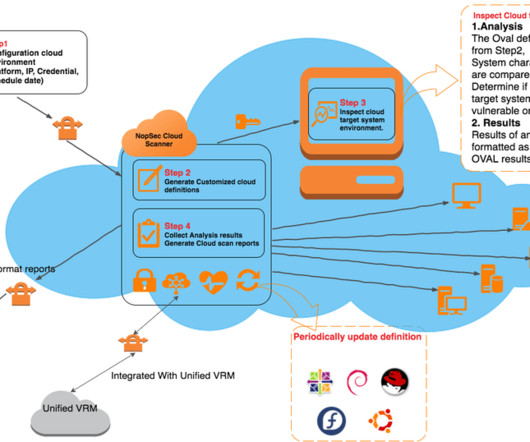
NopSec
JULY 13, 2016
Most organizations are currently migrating their computing infrastructure into the public cloud (AWS, Google, Azure) usually embracing a mixed private / public cloud model. Most SaaS solutions, including NopSec, already base their entire computing infrastructure on public clouds. This creates a unique challenge in terms of setting up proper vulnerability management processes to address the cloud environment’s peculiarities.

Kali Linux
JULY 10, 2016
The folks at Black Hat have been kind enough to invite us once again to deliver a Kali Dojo in Las Vegas this year. The event will be held on the 4th of August at the Mandalay Bay hotel, and will be open to all Black Hat pass types. This year our Dojo will be set up differently, allowing for a larger crowd and much more interaction. We are going to hold a full day event, featuring several main activity areas : Area 1: Customising Kali ISOs using live-build One to the most important aspects of Ka

Advertisement
How many people would you trust with your house keys? Chances are, you have a handful of trusted friends and family members who have an emergency copy, but you definitely wouldn’t hand those out too freely. You have stuff that’s worth protecting—and the more people that have access to your belongings, the higher the odds that something will go missing.

Tech Republic Security
JULY 13, 2016
Documentary filmmaker Yuval Orr interviewed cryptoanarchists, hackers, and security experts about why encryption and privacy are important. His new movie will make you see the Dark Web in a new light.

Privacy and Cybersecurity Law
JULY 13, 2016
The European Commission yesterday issued an adequacy decision adopting the EU-US Privacy Shield, which replaces Safe Harbor as a framework […].
Cyber Security Informer brings together the best content for cyber security professionals from the widest variety of industry thought leaders.

Tech Republic Security
JULY 13, 2016
Encrypting your email is a great step towards more secure communication. Gmail, Mailvelope, and Virtru can help streamline your encrypted email efforts.

Tech Republic Security
JULY 14, 2016
Microsoft recently won an appeal over a US search warrant that aimed to force the company to turn over data that was stored on foreign servers.

Tech Republic Security
JULY 11, 2016
Malvertising is malware at its best, even catching security experts in its crosshairs. Learn how to fight back against these malware-infused ads.

Tech Republic Security
JULY 12, 2016
Computer scientists enhance data security by simplifying the creation of truly random numbers used to build encryption keys.

Advertiser: Revenera
In a recent study, IDC found that 64% of organizations said they were already using open source in software development with a further 25% planning to in the next year. Most organizations are unaware of just how much open-source code is used and underestimate their dependency on it. As enterprises grow the use of open-source software, they face a new challenge: understanding the scope of open-source software that's being used throughout the organization and the corresponding exposure.

Tech Republic Security
JULY 14, 2016
The UK government recently began a trial using blockchain technology to track the distribution of benefits, which has raised some privacy concerns.

Tech Republic Security
JULY 12, 2016
Analytics managers need to do two things to protect IoT-generated data from an often-overlooked threat.

Tech Republic Security
JULY 14, 2016
If you want to set up an in-house authentication system to use for ownCloud, WordPress, and the like, find out how to install privacyIDEA on your Ubuntu server.

Tech Republic Security
JULY 11, 2016
At the 2016 Cisco Live event, the company announced new products to address network threats faster and help users more easily pinpoint advanced threats.

Advertisement
The healthcare industry has massively adopted web tracking tools, including pixels and trackers. Tracking tools on user-authenticated and unauthenticated web pages can access personal health information (PHI) such as IP addresses, medical record numbers, home and email addresses, appointment dates, or other info provided by users on pages and thus can violate HIPAA Rules that govern the Use of Online Tracking Technologies by HIPAA Covered Entities and Business Associates.

Tech Republic Security
JULY 11, 2016
The online black market is becoming a well-oiled and lucrative machine, thanks to the massive amount of stolen data flowing through the underground.

Tech Republic Security
JULY 12, 2016
Gionee, a Chinese phone manufacturer, claims that its new smartphone uses an encrypted chip and could be the 'safest smartphone ever.

Tech Republic Security
JULY 14, 2016
Vulnerabilities are likely, even in the best software. Creating a bug bounty program is one way to find and fix them faster.

Tech Republic Security
JULY 14, 2016
Vulnerabilities are likely, even in the best software. Creating a bug bounty program is one way to find and fix them faster.

Speaker: Blackberry, OSS Consultants, & Revenera
Software is complex, which makes threats to the software supply chain more real every day. 64% of organizations have been impacted by a software supply chain attack and 60% of data breaches are due to unpatched software vulnerabilities. In the U.S. alone, cyber losses totaled $10.3 billion in 2022. All of these stats beg the question, “Do you know what’s in your software?

Tech Republic Security
JULY 11, 2016
Here's a quick tutorial on how to add a custom lock screen message to Mac devices running 10.7 to 10.11.

Tech Republic Security
JULY 13, 2016
Results of a recent Tech Pro Research survey suggest workers using unsupported mobile devices is a significant security risk.
Let's personalize your content