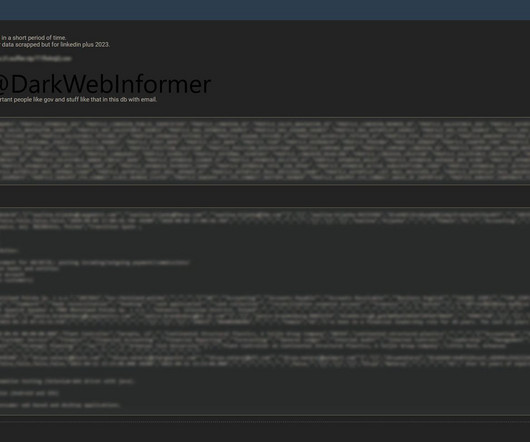
Hackers, Scrapers & Fakers: What's Really Inside the Latest LinkedIn Dataset
Troy Hunt
NOVEMBER 6, 2023
I like to think of investigating data breaches as a sort of scientific search for truth. You start out with a theory (a set of data coming from an alleged source), but you don't have a vested interested in whether the claim is true or not, rather you follow the evidence and see where it leads. Verification that supports the alleged source is usually quite straightforward , but disproving a claim can be a rather time consuming exercise, especially when a dataset contains fragments of truth m


















Let's personalize your content