The Fake Browser Update Scam Gets a Makeover
Krebs on Security
OCTOBER 18, 2023
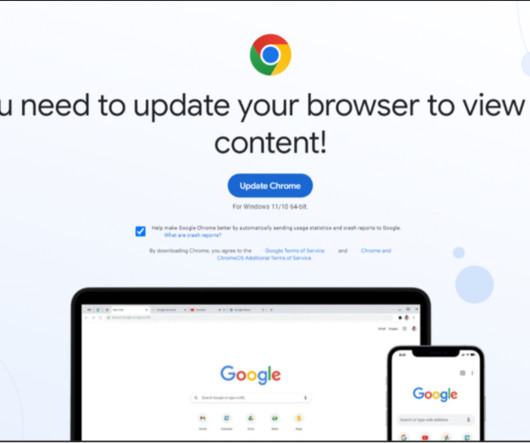
One of the oldest malware tricks in the book — hacked websites claiming visitors need to update their Web browser before they can view any content — has roared back to life in the past few months. New research shows the attackers behind one such scheme have developed an ingenious way of keeping their malware from being taken down by security experts or law enforcement: By hosting the malicious files on a decentralized, anonymous cryptocurrency blockchain.





































Let's personalize your content