Major Cyber Insurance Overhaul Begins Now
Lohrman on Security
APRIL 9, 2023
From Lloyd’s of London to the new National Cybersecurity Strategy, the future of cyber insurance is evolving fast. What do you need to watch?

Lohrman on Security
APRIL 9, 2023
From Lloyd’s of London to the new National Cybersecurity Strategy, the future of cyber insurance is evolving fast. What do you need to watch?

Schneier on Security
APRIL 12, 2023
The FBI is warning people against using public phone-charging stations, worrying that the combination power-data port can be used to inject malware onto the devices: Avoid using free charging stations in airports, hotels, or shopping centers. Bad actors have figured out ways to use public USB ports to introduce malware and monitoring software onto devices that access these ports.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

Krebs on Security
APRIL 14, 2023
KrebsOnSecurity received a nice bump in traffic this week thanks to tweets from the Federal Bureau of Investigation (FBI) and the Federal Communications Commission (FCC) about “ juice jacking ,” a term first coined here in 2011 to describe a potential threat of data theft when one plugs their mobile device into a public charging kiosk. It remains unclear what may have prompted the alerts, but the good news is that there are some fairly basic things you can do to avoid having to worry

Anton on Security
APRIL 13, 2023
This is my completely informal, uncertified, unreviewed and otherwise completely unofficial blog inspired by my reading of our sixth Threat Horizons Report ( full version ) that we just released ( the official blog for #1 report , my unofficial blogs for #2 , #3 , #4 and #5 ). My favorite quotes from the report follow below: “Our research has shown that the most common vector used to compromise any network, including cloud instances is to take over an account’s credentials directly : either bec

Speaker: Erroll Amacker
Automation is transforming finance but without strong financial oversight it can introduce more risk than reward. From missed discrepancies to strained vendor relationships, accounts payable automation needs a human touch to deliver lasting value. This session is your playbook to get automation right. We’ll explore how to balance speed with control, boost decision-making through human-machine collaboration, and unlock ROI with fewer errors, stronger fraud prevention, and smoother operations.

Tech Republic Security
APRIL 14, 2023
A new report from cyberthreat intelligence company Cybersixgill sees threat actors swarming to digital bazaars to collaborate, buy and sell malware and credentials. The post For cybercriminal mischief, it’s dark web vs deep web appeared first on TechRepublic.

Schneier on Security
APRIL 11, 2023
Car thieves are injecting malicious software into a car’s network through wires in the headlights (or taillights) that fool the car into believing that the electronic key is nearby. News articles.
Cyber Security Informer brings together the best content for cyber security professionals from the widest variety of industry thought leaders.

The Last Watchdog
APRIL 10, 2023
Instilling a culture of cyber security at your organization requires your people to maintain a high level of knowledge and awareness about cyber security risks—and that takes an effective, impactful, and ongoing security awareness program. Related: Deploying employees as human sensors However, a security awareness program is only as good as its content.

Tech Republic Security
APRIL 13, 2023
Android infections are also prevalent on the dark web, according to Kaspersky. Learn how to keep your workforce safe from these mobile and BYOD security threats. The post Google Play threats on the dark web are big business appeared first on TechRepublic.

Schneier on Security
APRIL 10, 2023
Here’s an experiment being run by undergraduate computer science students everywhere: Ask ChatGPT to generate phishing emails, and test whether these are better at persuading victims to respond or click on the link than the usual spam. It’s an interesting experiment, and the results are likely to vary wildly based on the details of the experiment.

SecureList
APRIL 12, 2023
The Lazarus group is a high-profile Korean-speaking threat actor with multiple sub-campaigns. We have previously published information about the connections of each cluster of this group. In this blog, we’ll focus on an active cluster that we dubbed DeathNote because the malware responsible for downloading additional payloads is named Dn.dll or Dn64.dll.

Advertisement
Many cybersecurity awareness platforms offer massive content libraries, yet they fail to enhance employees’ cyber resilience. Without structured, engaging, and personalized training, employees struggle to retain and apply key cybersecurity principles. Phished.io explains why organizations should focus on interactive, scenario-based learning rather than overwhelming employees with excessive content.

The Last Watchdog
APRIL 12, 2023
At 10 am PDT, next Wednesday, April 19 th , I’ll have the privilege of appearing as a special guest panelist and spotlight speaker on Virtual Guardian’s monthly Behind the Shield cybersecurity podcast. Related: The Golden Age of cyber spying is upon us You can RSVP – and be part of the live audience – by signing up here. The moderator, Marco Estrela, does a terrific job highlighting current cybersecurity topics ripped from the headlines.

Tech Republic Security
APRIL 10, 2023
With PingOne Neo, PingIdentity aims to accelerate “speed to trust”, supercharge identity management and put control of a user’s identity in the user’s pocket. The post PingIdentity launches decentralized identity management appeared first on TechRepublic.

Schneier on Security
APRIL 14, 2023
You can beat the game without a computer : On a perfect [roulette] wheel, the ball would always fall in a random way. But over time, wheels develop flaws, which turn into patterns. A wheel that’s even marginally tilted could develop what Barnett called a ‘drop zone.’ When the tilt forces the ball to climb a slope, the ball decelerates and falls from the outer rim at the same spot on almost every spin.

SecureList
APRIL 11, 2023
In February 2023, Kaspersky technologies detected a number of attempts to execute similar elevation-of-privilege exploits on Microsoft Windows servers belonging to small and medium-sized businesses in the Middle East, in North America, and previously in Asia regions. These exploits were very similar to already known Common Log File System (CLFS) driver exploits that we analyzed previously, but we decided to double check and it was worth it – one of the exploits turned out to be a zero-day, suppo

Advertisement
The DHS compliance audit clock is ticking on Zero Trust. Government agencies can no longer ignore or delay their Zero Trust initiatives. During this virtual panel discussion—featuring Kelly Fuller Gordon, Founder and CEO of RisX, Chris Wild, Zero Trust subject matter expert at Zermount, Inc., and Principal of Cybersecurity Practice at Eliassen Group, Trey Gannon—you’ll gain a detailed understanding of the Federal Zero Trust mandate, its requirements, milestones, and deadlines.
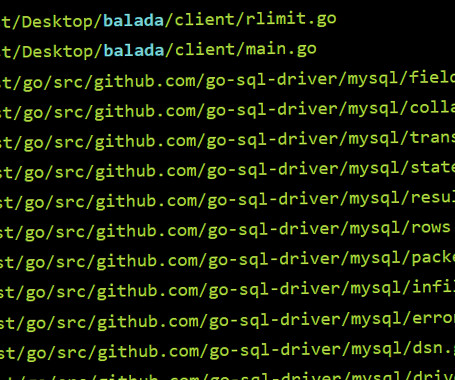
The Hacker News
APRIL 10, 2023
Over one million WordPress websites are estimated to have been infected by an ongoing campaign to deploy malware called Balada Injector since 2017. The massive campaign, per GoDaddy's Sucuri, "leverages all known and recently discovered theme and plugin vulnerabilities" to breach WordPress sites. The attacks are known to play out in waves once every few weeks.

Tech Republic Security
APRIL 12, 2023
Graymail, phishing, vendor impersonation, and other BECs clogging up security teams’ time. The post Cybersecurity leaders see risk from email attacks, hybrid work appeared first on TechRepublic.

Schneier on Security
APRIL 13, 2023
Thieves cut through the wall of a coffee shop to get to an Apple store, bypassing the alarms in the process. I wrote about this kind of thing in 2000, in Secrets and Lies (page 318): My favorite example is a band of California art thieves that would break into people’s houses by cutting a hole in their walls with a chainsaw. The attacker completely bypassed the threat model of the defender.

Security Boulevard
APRIL 12, 2023
Beware Fancy Bears Bearing Gifts: Confirms DCLeaks caper was by APT28. Also that APT28 is Russian military unit. The post ‘But His Emails!’ — Ukrainian Hackers Hack Hillary Hacker appeared first on Security Boulevard.

Advertisement
Keeper Security is transforming cybersecurity for people and organizations around the world. Keeper’s affordable and easy-to-use solutions are built on a foundation of zero-trust and zero-knowledge security to protect every user on every device. Our next-generation privileged access management solution deploys in minutes and seamlessly integrates with any tech stack to prevent breaches, reduce help desk costs and ensure compliance.

Bleeping Computer
APRIL 11, 2023
Microsoft and Citizen Lab discovered commercial spyware made by an Israel-based company QuaDream used to compromise the iPhones of high-risk individuals using a zero-click exploit named ENDOFDAYS. [.

Tech Republic Security
APRIL 12, 2023
In the face of growing risks from open-source software dependencies, Google Cloud is releasing its Assured Open Source Software (Assured OSS) service for Java and Python ecosystems at no cost. The post Google Cloud offers Assured Open Source Software for free appeared first on TechRepublic.

Schneier on Security
APRIL 14, 2023
This is a current list of where and when I am scheduled to speak: I’m speaking on “Cybersecurity Thinking to Reinvent Democracy” at RSA Conference 2023 in San Francisco, California, on Tuesday, April 25, 2023, at 9:40 AM PT. I’m speaking at IT-S Now 2023 in Vienna, Austria, on June 2, 2023 at 8:30 AM CEST. The list is maintained on this page.
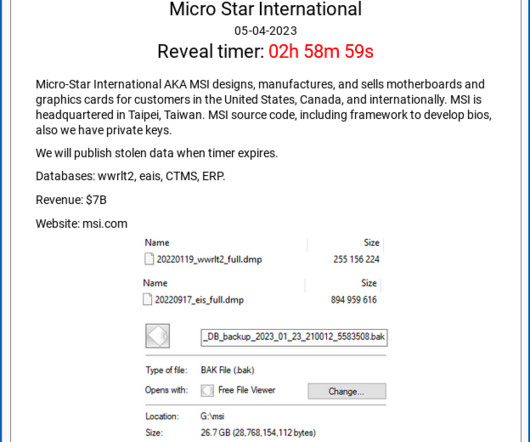
Naked Security
APRIL 11, 2023
Stealing private keys is like getting hold of a medieval monarch's personal signet ring. you get to put an official seal on treasonous material.

Speaker: Sierre Lindgren
Fraud is a battle that every organization must face – it’s no longer a question of “if” but “when.” Every organization is a potential target for fraud, and the finance department is often the bullseye. From cleverly disguised emails to fraudulent payment requests, the tactics of cybercriminals are advancing rapidly. Drawing insights from real-world cases and industry expertise, we’ll explore the vulnerabilities in your processes and how to fortify them effectively.

Bleeping Computer
APRIL 14, 2023
Google has released an emergency Chrome security update to address the first zero-day vulnerability exploited in attacks since the start of the year. [.

Tech Republic Security
APRIL 10, 2023
There are courses in this bundle for all skill levels; several require no previous tech background whatsoever. The post Learn what you need to protect your business with ethical hacking for just $45 appeared first on TechRepublic.

Schneier on Security
APRIL 14, 2023
Here’s a religious hack : You want to commit suicide, but it’s a mortal sin: your soul goes straight to hell, forever. So what you do is murder someone. That will get you executed, but if you confess your sins to a priest beforehand you avoid hell. Problem solved. This was actually a problem in the 17th and 18th centuries in Northern Europe, particularly Denmark.

Dark Reading
APRIL 13, 2023
There are plenty of AD objects and groups that should be considered tier zero in every environment, but some will vary among organizations.

Advertisement
Many software teams have migrated their testing and production workloads to the cloud, yet development environments often remain tied to outdated local setups, limiting efficiency and growth. This is where Coder comes in. In our 101 Coder webinar, you’ll explore how cloud-based development environments can unlock new levels of productivity. Discover how to transition from local setups to a secure, cloud-powered ecosystem with ease.

Graham Cluley
APRIL 14, 2023
Accountants are being warned to be on their guard from hackers, as cybercriminals exploit the rush to prepare tax returns for clients before the deadline of US Tax Day. Read more in my article on the Tripwire State of Security blog.
Tech Republic Security
APRIL 11, 2023
The service previously won the BestVPN.com Fastest VPN Award. The post Protect your company data with an Ivacy VPN lifetime subscription for $18 appeared first on TechRepublic.

Naked Security
APRIL 10, 2023
That double-whammy Apple browser-to-kernel spyware bug combo we wrote up last week? Turns out it applies to all supported Macs and iDevices - patch now!

WIRED Threat Level
APRIL 13, 2023
Security researchers are jailbreaking large language models to get around safety rules. Things could get much worse.

Advertisement
After a year of sporadic hiring and uncertain investment areas, tech leaders are scrambling to figure out what’s next. This whitepaper reveals how tech leaders are hiring and investing for the future. Download today to learn more!
Let's personalize your content