Top 5: Things to know about cloud security
Tech Republic Security
JULY 13, 2017
Knowing the basics of cloud security can help you pick a better cloud provider. Here are five bits of important information.

Tech Republic Security
JULY 13, 2017
Knowing the basics of cloud security can help you pick a better cloud provider. Here are five bits of important information.

Elie
JULY 13, 2017
This post looks at how and why people are using the private browsing mode. Private Browsing. , also known as. InPrivate. in Internet Explorer and. Incognito mode. in Google Chrome, is a special mode where the browser doesn’t record the browsing activity on the local device. The promise made to the user is that when the private windows are closed, no trace will be left on the computer.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

Privacy and Cybersecurity Law
JULY 13, 2017
Last month, after the WannaCry ransomware attack infected 230,000 computers in 150 countries, the US Department of Health and Human […].
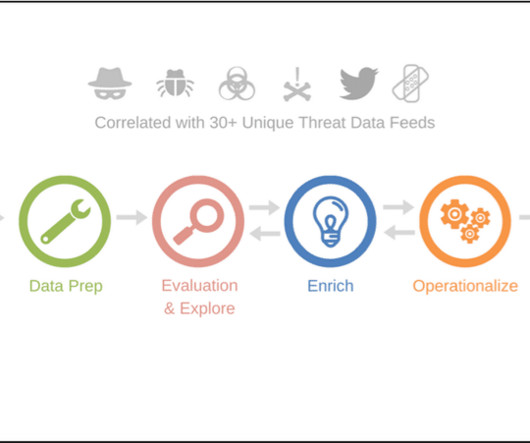
NopSec
JULY 11, 2017
Data is power virtually everywhere, and it’s all about how you utilize that information. In business, you can use data to grow your company, stay ahead of your competitors, develop new products, and more. In sports, data means the ability to efficiently identify the weaknesses of your opponents, develop better plays, and optimize practice and overall fitness regimens of your team among other things.

Speaker: Erroll Amacker
Automation is transforming finance but without strong financial oversight it can introduce more risk than reward. From missed discrepancies to strained vendor relationships, accounts payable automation needs a human touch to deliver lasting value. This session is your playbook to get automation right. We’ll explore how to balance speed with control, boost decision-making through human-machine collaboration, and unlock ROI with fewer errors, stronger fraud prevention, and smoother operations.

Tech Republic Security
JULY 10, 2017
VMware's NSX hypervisor provides a platform to manage virtualized network deployments. Learn more about the network virtualization platform in this resource guide.

Elie
JULY 13, 2017
In-depth research publications, industry talks and blog posts about Google security, research at Google and cybersecurity in general in open-access.
Cyber Security Informer brings together the best content for cyber security professionals from the widest variety of industry thought leaders.

Tech Republic Security
JULY 14, 2017
Proofpoint security researchers examined the Ovidiy Stealer malware, which steals credentials and operates primarily in Russian-speaking regions.

Tech Republic Security
JULY 14, 2017
Often thought of as impenetrable, macOS is falling prey to a sneaky malware that's stealing bank credentials, bypassing Gatekeeper, and disabling attempts to remove it. Find out more here.

Tech Republic Security
JULY 10, 2017
Uninformed or careless employees are one of the top causes of a cybersecurity incident, according to a Kaspersky Lab report.

Tech Republic Security
JULY 12, 2017
New research from SiteLock reveals that no website is too small to hack. Here is the data showing who is most vulnerable, and what mediums cybercriminals use to compromise sites.

Advertisement
Many cybersecurity awareness platforms offer massive content libraries, yet they fail to enhance employees’ cyber resilience. Without structured, engaging, and personalized training, employees struggle to retain and apply key cybersecurity principles. Phished.io explains why organizations should focus on interactive, scenario-based learning rather than overwhelming employees with excessive content.

Tech Republic Security
JULY 10, 2017
An expert panel at the Global Cybersecurity Summit in Kiev, Ukraine, discussed various devices that could be connected in the future, and how they might impact consumers, governments, and industries.

Tech Republic Security
JULY 13, 2017
To be safe with cloud storage, you need to know how it works. Here are five basic issues to look for.

Tech Republic Security
JULY 13, 2017
An IT employee was recently almost fired for storing documents on Dropbox. Here's how the employee and the company could have prevented that situation.

Tech Republic Security
JULY 12, 2017
Microsoft has ended support for Windows Phone 8.1, meaning users will no longer receive important updates. Here's how your business can respond.

Advertisement
The DHS compliance audit clock is ticking on Zero Trust. Government agencies can no longer ignore or delay their Zero Trust initiatives. During this virtual panel discussion—featuring Kelly Fuller Gordon, Founder and CEO of RisX, Chris Wild, Zero Trust subject matter expert at Zermount, Inc., and Principal of Cybersecurity Practice at Eliassen Group, Trey Gannon—you’ll gain a detailed understanding of the Federal Zero Trust mandate, its requirements, milestones, and deadlines.

Tech Republic Security
JULY 11, 2017
The Electronic Frontier Foundation's Who Has Your Back report takes a look at how tech companies share user data with the government. Here are the lowest performers.

Tech Republic Security
JULY 11, 2017
July brought to a drastic reduction in critical-level vulnerabilities found in Android. Get the highlights.

Tech Republic Security
JULY 10, 2017
Trend Micro's cybersecurity solutions are coming to VMware Workspace ONE and VMware AirWatch to help IT leaders protect devices from a growing number of mobile attacks.

Tech Republic Security
JULY 11, 2017
The cost of digital theft rose by 5% this year. Wendi Whitmore leads the IMB Security X-Force Incident Response & Intelligence Services team. She explains how your company can lower the cost of cyber-intrusions.

Advertisement
Keeper Security is transforming cybersecurity for people and organizations around the world. Keeper’s affordable and easy-to-use solutions are built on a foundation of zero-trust and zero-knowledge security to protect every user on every device. Our next-generation privileged access management solution deploys in minutes and seamlessly integrates with any tech stack to prevent breaches, reduce help desk costs and ensure compliance.

Tech Republic Security
JULY 12, 2017
The fix for the HoloLens remote code execution was released as part of Tuesday's bundle of more than 50 security patches.

Tech Republic Security
JULY 13, 2017
Updating software has become one of the many keys to data security. Jack Wallen explains why the excuses for failing to update must become a thing of the past.

Tech Republic Security
JULY 11, 2017
Researchers suggest human bias influences algorithms more than we realize, and offer a solution to weed the bias out. They received a $1 million National Science Foundation grant for their project.

Tech Republic Security
JULY 12, 2017
Vincent Weafer, Vice President of McAfee Labs, explains the technology why the Petya and WannaCry outbreaks were so virulent, and what you can do when your company is exposed to a cyberattack.

Speaker: Sierre Lindgren
Fraud is a battle that every organization must face – it’s no longer a question of “if” but “when.” Every organization is a potential target for fraud, and the finance department is often the bullseye. From cleverly disguised emails to fraudulent payment requests, the tactics of cybercriminals are advancing rapidly. Drawing insights from real-world cases and industry expertise, we’ll explore the vulnerabilities in your processes and how to fortify them effectively.

Tech Republic Security
JULY 11, 2017
A new report from Comparitech details how cyberattacks change the reputation of a company, and can hurt its value in the market.

Tech Republic Security
JULY 10, 2017
Ever wonder how hackers make money? Or where stolen corporate data is resold? What about cyberweapons and hacking tools? Etay Maor, Executive Security Advisor of IBM Security, shows us the 'Amazon of the Dark Web.

Privacy and Cybersecurity Law
JULY 11, 2017
According to a new joint report issued by the US Department of Homeland Security (DHS) and Federal Bureau of Investigation […].

Tech Republic Security
JULY 14, 2017
If America is hacked the country must show backbone, the president's son told TechRepublic during the 2016 campaign. A year later, are we more secure?

Advertisement
Many software teams have migrated their testing and production workloads to the cloud, yet development environments often remain tied to outdated local setups, limiting efficiency and growth. This is where Coder comes in. In our 101 Coder webinar, you’ll explore how cloud-based development environments can unlock new levels of productivity. Discover how to transition from local setups to a secure, cloud-powered ecosystem with ease.

Tech Republic Security
JULY 11, 2017
Only 26% of respondents in a study published by Black Hat Research were confident that the US government, under president Trump, would be able to react correctly to a major breach.

Tech Republic Security
JULY 13, 2017
During the presidential campaign at the 2016 New Hampshire primary, Donald Trump Jr. told TechRepublic cybersecurity is one of country's biggest challenges and the president would thwart attacks by hiring the "best of the best.

Tech Republic Security
JULY 13, 2017
"Every single day American companies are being hacked.

Privacy and Cybersecurity Law
JULY 11, 2017
According to a new joint report issued by the US Department of Homeland Security (DHS) and Federal Bureau of Investigation (FBI), hackers have been penetrating the computer networks of companies that operate nuclear power stations, energy facilities, and manufacturing plants in the US since May 2017. The joint report carried an urgent amber warning, which is the second-highest rating for the sensitivity of a threat.

Advertisement
After a year of sporadic hiring and uncertain investment areas, tech leaders are scrambling to figure out what’s next. This whitepaper reveals how tech leaders are hiring and investing for the future. Download today to learn more!
Let's personalize your content