VMware NSX: The smart person's guide
Tech Republic Security
JULY 10, 2017
VMware's NSX hypervisor provides a platform to manage virtualized network deployments. Learn more about the network virtualization platform in this resource guide.

Tech Republic Security
JULY 10, 2017
VMware's NSX hypervisor provides a platform to manage virtualized network deployments. Learn more about the network virtualization platform in this resource guide.

Elie
JULY 13, 2017
This post looks at how and why people are using the private browsing mode. Private Browsing. , also known as. InPrivate. in Internet Explorer and. Incognito mode. in Google Chrome, is a special mode where the browser doesn’t record the browsing activity on the local device. The promise made to the user is that when the private windows are closed, no trace will be left on the computer.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

Privacy and Cybersecurity Law
JULY 13, 2017
Last month, after the WannaCry ransomware attack infected 230,000 computers in 150 countries, the US Department of Health and Human […].
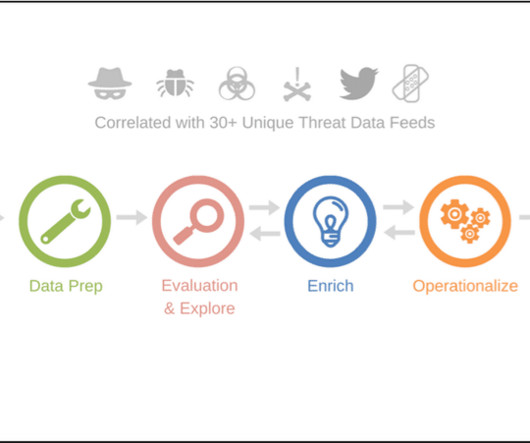
NopSec
JULY 11, 2017
Data is power virtually everywhere, and it’s all about how you utilize that information. In business, you can use data to grow your company, stay ahead of your competitors, develop new products, and more. In sports, data means the ability to efficiently identify the weaknesses of your opponents, develop better plays, and optimize practice and overall fitness regimens of your team among other things.

Advertisement
How many people would you trust with your house keys? Chances are, you have a handful of trusted friends and family members who have an emergency copy, but you definitely wouldn’t hand those out too freely. You have stuff that’s worth protecting—and the more people that have access to your belongings, the higher the odds that something will go missing.

Tech Republic Security
JULY 14, 2017
Often thought of as impenetrable, macOS is falling prey to a sneaky malware that's stealing bank credentials, bypassing Gatekeeper, and disabling attempts to remove it. Find out more here.

Elie
JULY 13, 2017
In-depth research publications, industry talks and blog posts about Google security, research at Google and cybersecurity in general in open-access.
Cyber Security Informer brings together the best content for cyber security professionals from the widest variety of industry thought leaders.

Tech Republic Security
JULY 14, 2017
Proofpoint security researchers examined the Ovidiy Stealer malware, which steals credentials and operates primarily in Russian-speaking regions.

Tech Republic Security
JULY 12, 2017
New research from SiteLock reveals that no website is too small to hack. Here is the data showing who is most vulnerable, and what mediums cybercriminals use to compromise sites.

Tech Republic Security
JULY 13, 2017
Knowing the basics of cloud security can help you pick a better cloud provider. Here are five bits of important information.

Tech Republic Security
JULY 11, 2017
The Electronic Frontier Foundation's Who Has Your Back report takes a look at how tech companies share user data with the government. Here are the lowest performers.

Advertiser: Revenera
In a recent study, IDC found that 64% of organizations said they were already using open source in software development with a further 25% planning to in the next year. Most organizations are unaware of just how much open-source code is used and underestimate their dependency on it. As enterprises grow the use of open-source software, they face a new challenge: understanding the scope of open-source software that's being used throughout the organization and the corresponding exposure.

Tech Republic Security
JULY 10, 2017
An expert panel at the Global Cybersecurity Summit in Kiev, Ukraine, discussed various devices that could be connected in the future, and how they might impact consumers, governments, and industries.

Tech Republic Security
JULY 10, 2017
Uninformed or careless employees are one of the top causes of a cybersecurity incident, according to a Kaspersky Lab report.

Tech Republic Security
JULY 12, 2017
Microsoft has ended support for Windows Phone 8.1, meaning users will no longer receive important updates. Here's how your business can respond.

Tech Republic Security
JULY 11, 2017
The cost of digital theft rose by 5% this year. Wendi Whitmore leads the IMB Security X-Force Incident Response & Intelligence Services team. She explains how your company can lower the cost of cyber-intrusions.

Advertisement
The healthcare industry has massively adopted web tracking tools, including pixels and trackers. Tracking tools on user-authenticated and unauthenticated web pages can access personal health information (PHI) such as IP addresses, medical record numbers, home and email addresses, appointment dates, or other info provided by users on pages and thus can violate HIPAA Rules that govern the Use of Online Tracking Technologies by HIPAA Covered Entities and Business Associates.

Tech Republic Security
JULY 10, 2017
Trend Micro's cybersecurity solutions are coming to VMware Workspace ONE and VMware AirWatch to help IT leaders protect devices from a growing number of mobile attacks.

Tech Republic Security
JULY 13, 2017
An IT employee was recently almost fired for storing documents on Dropbox. Here's how the employee and the company could have prevented that situation.

Tech Republic Security
JULY 13, 2017
Updating software has become one of the many keys to data security. Jack Wallen explains why the excuses for failing to update must become a thing of the past.

Tech Republic Security
JULY 13, 2017
To be safe with cloud storage, you need to know how it works. Here are five basic issues to look for.

Speaker: Blackberry, OSS Consultants, & Revenera
Software is complex, which makes threats to the software supply chain more real every day. 64% of organizations have been impacted by a software supply chain attack and 60% of data breaches are due to unpatched software vulnerabilities. In the U.S. alone, cyber losses totaled $10.3 billion in 2022. All of these stats beg the question, “Do you know what’s in your software?

Tech Republic Security
JULY 11, 2017
Researchers suggest human bias influences algorithms more than we realize, and offer a solution to weed the bias out. They received a $1 million National Science Foundation grant for their project.

Tech Republic Security
JULY 12, 2017
Vincent Weafer, Vice President of McAfee Labs, explains the technology why the Petya and WannaCry outbreaks were so virulent, and what you can do when your company is exposed to a cyberattack.

Tech Republic Security
JULY 11, 2017
July brought to a drastic reduction in critical-level vulnerabilities found in Android. Get the highlights.

Tech Republic Security
JULY 12, 2017
The fix for the HoloLens remote code execution was released as part of Tuesday's bundle of more than 50 security patches.

Advertisement
Within the past few years, ransomware attacks have turned to critical infrastructure, healthcare, and government entities. Attackers have taken advantage of the rapid shift to remote work and new technologies. Add to that hacktivism due to global conflicts and U.S. elections, and an increased focus on AI, and you have the perfect recipe for a knotty and turbulent 2024.

Tech Republic Security
JULY 10, 2017
Ever wonder how hackers make money? Or where stolen corporate data is resold? What about cyberweapons and hacking tools? Etay Maor, Executive Security Advisor of IBM Security, shows us the 'Amazon of the Dark Web.

Tech Republic Security
JULY 11, 2017
A new report from Comparitech details how cyberattacks change the reputation of a company, and can hurt its value in the market.

Privacy and Cybersecurity Law
JULY 13, 2017
Last month, after the WannaCry ransomware attack infected 230,000 computers in 150 countries, the US Department of Health and Human Services (HHS) Office for Civil Rights (OCR) issued a “ Quick-Response Checklist ” for HIPPA covered entities and business associates to follow when responding to a ransomware attack or other “cyber-related security incident,” as that phrase is defined under the HIPAA Security Rule. 45 C.F.R. 164.304.

Tech Republic Security
JULY 14, 2017
If America is hacked the country must show backbone, the president's son told TechRepublic during the 2016 campaign. A year later, are we more secure?

Speaker: Erika R. Bales, Esq.
When we talk about “compliance and security," most companies want to ensure that steps are being taken to protect what they value most – people, data, real or personal property, intellectual property, digital assets, or any other number of other things - and it’s more important than ever that safeguards are in place. Let’s step back and focus on the idea that no matter how complicated the compliance and security regime, it should be able to be distilled down to a checklist.

Tech Republic Security
JULY 11, 2017
Only 26% of respondents in a study published by Black Hat Research were confident that the US government, under president Trump, would be able to react correctly to a major breach.

Tech Republic Security
JULY 13, 2017
During the presidential campaign at the 2016 New Hampshire primary, Donald Trump Jr. told TechRepublic cybersecurity is one of country's biggest challenges and the president would thwart attacks by hiring the "best of the best.

Privacy and Cybersecurity Law
JULY 11, 2017
According to a new joint report issued by the US Department of Homeland Security (DHS) and Federal Bureau of Investigation (FBI), hackers have been penetrating the computer networks of companies that operate nuclear power stations, energy facilities, and manufacturing plants in the US since May 2017. The joint report carried an urgent amber warning, which is the second-highest rating for the sensitivity of a threat.

Tech Republic Security
JULY 13, 2017
"Every single day American companies are being hacked.

Speaker: William Hord, Vice President of ERM Services
A well-defined change management process is critical to minimizing the impact that change has on your organization. Leveraging the data that your ERM program already contains is an effective way to help create and manage the overall change management process within your organization. Your ERM program generally assesses and maintains detailed information related to strategy, operations, and the remediation plans needed to mitigate the impact on the organization.
Let's personalize your content