SolarWinds Security Event Manager – SIEM Product Overview and Insight
eSecurity Planet
FEBRUARY 6, 2023
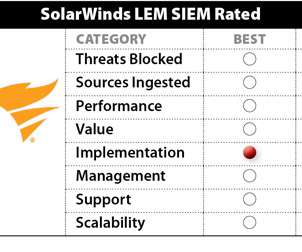
SolarWinds Security Event Manager (SEM) 2022.4 SolarWinds SIEM Features Rated Threats Blocked: Good. SolarWinds SEM supports a variety of event sources, including nonevent data sources that can be integrated into its analytics and correlation rules. It trades on the NYSE under the symbol SWI. Throughput: Good. Management: Good.















































Let's personalize your content