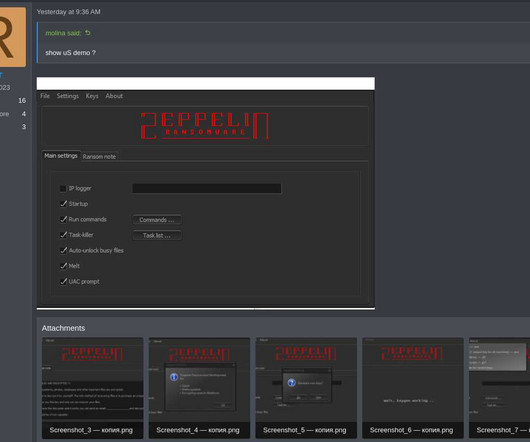
Researchers Quietly Cracked Zeppelin Ransomware Keys
Krebs on Security
NOVEMBER 17, 2022
He’d been on the job less than six months, and because of the way his predecessor architected things, the company’s data backups also were encrypted by Zeppelin. “We’ve found someone who can crack the encryption.” Then came the unlikely call from an FBI agent. “Don’t pay,” the agent said.










































Let's personalize your content