G7 Comes Out in Favor of Encryption Backdoors
Schneier on Security
APRIL 23, 2019
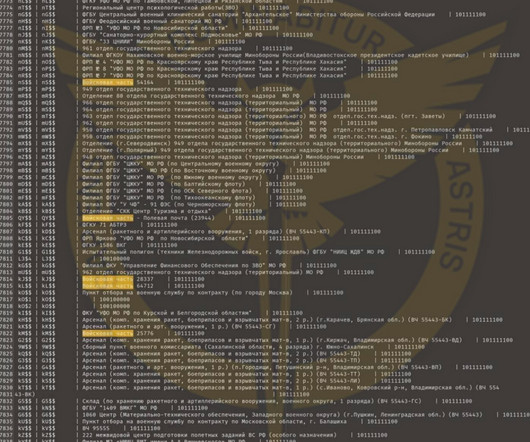
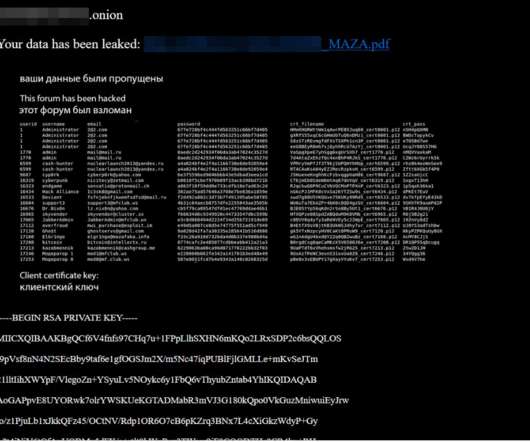
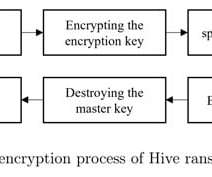
Some G7 countries highlight the importance of not prohibiting, limiting, or weakening encryption; There is a weird belief amongst policy makers that hacking an encryption system's key management system is fundamentally different than hacking the system's encryption algorithm.




































Let's personalize your content