Clever Social Engineering Attack Using Captchas
Schneier on Security
SEPTEMBER 20, 2024
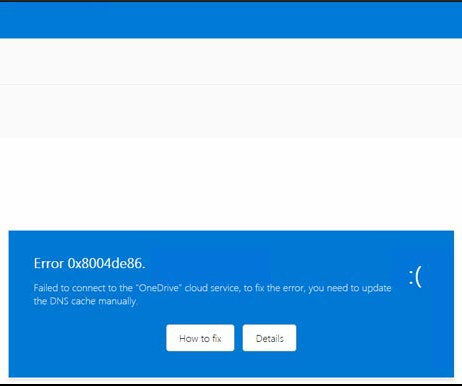
It’s a phishing attack targeting GitHub users, tricking them to solve a fake Captcha that actually runs a script that is copied to the command line. This is really interesting.













Let's personalize your content