How Microsoft's highly secure environment was breached
Malwarebytes
SEPTEMBER 7, 2023
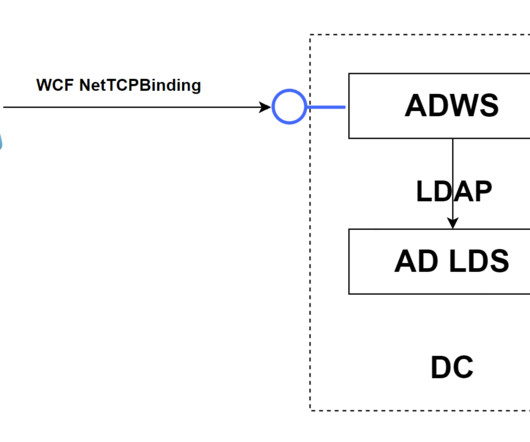
An investigation by Microsoft has finally revealed how China-based hackers circumvented the protections of a "highly isolated and restricted production environment" in May 2023 to unlock sensitive email accounts belonging to US government agencies. Assume you have been breached and monitor your environment accordingly.













































Let's personalize your content