Herjavec Group Wins 4 Cyber Defense Magazine Global InfoSec Awards
Herjavec Group
MAY 17, 2021
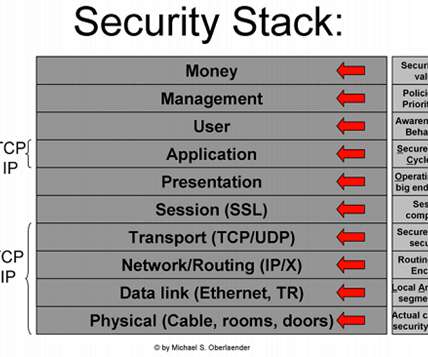
Quickly detect risks and amend access entitlement issues associated with privileged users. With HG MDR, your organization benefits from high fidelity alerting, improved threat detection, and time-to-value with expert-level response. . About CDM InfoSec Awards . A holistic view of your security and environment .

















Let's personalize your content