Apple Security Under Scrutiny Amid Fallout from NSO Spyware Scandal
eSecurity Planet
JULY 21, 2021
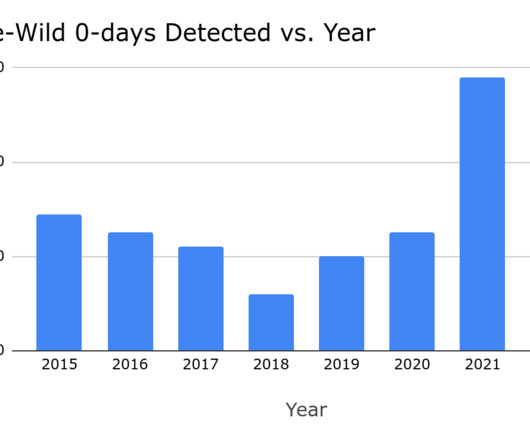
Reports that the NSO Group’s Pegasus spyware was used by governments to spy on Apple iPhones used by journalists, activists, government officials and business executives is becoming a global controversy for NSO, Apple and a number of governments at the center of the scandal. The impact of the burgeoning scandal continues to ripple.













Let's personalize your content