News alert: INE Security shares cyber hygiene guidance for small- and medium-sized businesses
The Last Watchdog
OCTOBER 23, 2024
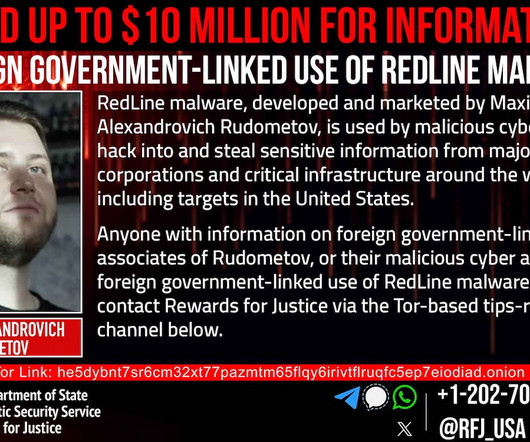
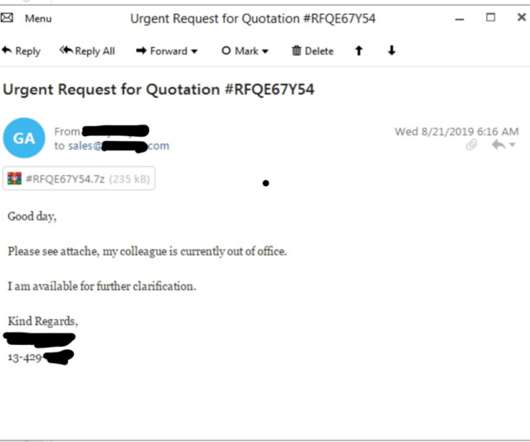
Tip 2: Implementing Strong Password Policies Weak passwords can be easily compromised, giving attackers access to sensitive systems and data. LastPass reports that 80% of all hacking-related breaches leveraged either stolen and/or weak passwords. 1 – Storing 1 copy offsite (e.g.,

















































Let's personalize your content