What is Form Submission?
Hacker Combat
JANUARY 19, 2022
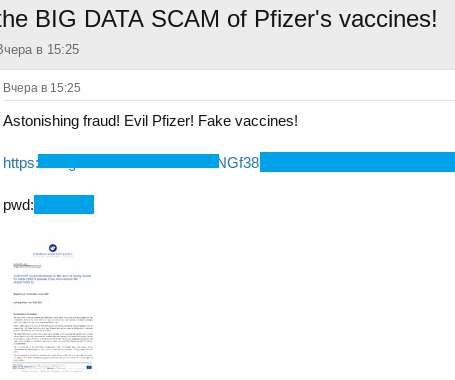
There is a new, less-hassle way to gather the data you need, and that is through a form submission. Form Submission Meaning. It is the process of taking and recording people’s responses sent through your online form builder. There are many robust form providers you can leverage. Google Forms.





































Let's personalize your content