New RedLine malware version distributed as fake Omicron stat counter
Security Affairs
JANUARY 12, 2022
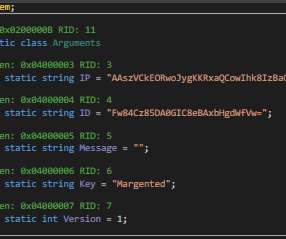
Experts warn of a new variant of the RedLine malware that is distributed via emails as fake COVID-19 Omicron stat counter app as a lure. The malicious code can also act as a first-stage malware. SecurityAffairs – hacking, RedLine malware). This variant uses 207[.]32.217.89 as its C2 server through port 14588. 154.167.91




























Let's personalize your content